Over the last two years, threat actors have found many lucrative ways to exploit pandemic-induced lifestyle changes and financial strain by creating scams using package delivery services as well as unemployment payments, grants, and vaccine passports as lures. As the world begins to adjust to life beyond Covid-19, threat actors are creating new lures, while still focusing on consumer behavior driven by the pandemic.
The global online food delivery market grew as usage spiked and is predicted to hit $1.92 billion in revenue by 2025, up from $1.26 billion in 2021. The UK alone is projected to reach £13.55 million in revenue by the end of 2022. It is a natural progression then that food delivery apps have become a new targeting vector for credential phishing. Within the last eight months, WMC Global has seen an increase in UK-based phishing attacks using delivery service lures. Currently we are tracking URLS in SMS messages pretending to be from popular UK delivery service Just Eat. We have also seen URLS imitating Deliveroo and Uber Eats.
JUST EAT PHISHING ATTACK
Just Eat holds 45% of the market share for delivery apps in the UK. Thus, a threat actor targeting British consumers has a good chance of reaching a person who has used the service. This likelihood coupled with the marked increase in at-home dining makes food delivery apps an attractive lure as they are also not yet commonly imitated.
WMC Global recorded URLs imitating Just Eat on March 29th of this year and determined they were linked to SMS messages. They initially directed users to a branded phishing page but have since gone offline. We have captured the user experience below.
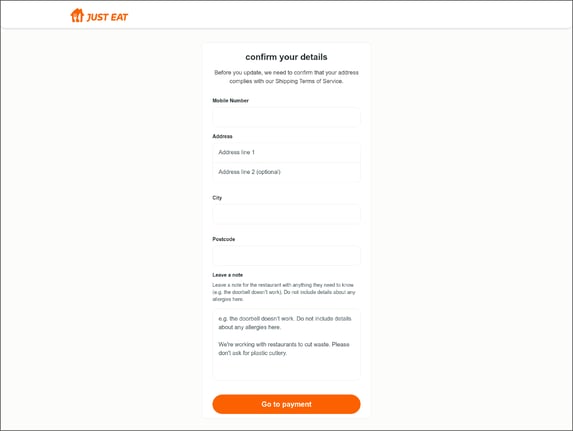
Figure 1. Just Eat Phishing Landing Page
First, the user receives a text message purporting to be from Just Eat and asking them to update something about their app profile. Most of these scams will use a generic lure for multiple situations. This message includes a phishing link that takes them to a landing page (Figure 1) which prompts the user to confirm their address is compliant with T&Cs prior to the update. The page then requests personally identifiable information (PII) including the user’s mobile number, address, city, and postcode.
Once the user submits their details for verification, they are taken to a second landing page (Figure 2, below) which asks the user to pay a £0.50 service charge to update their information. This is a phishing script that steals the user’s credit or debit card details along with their billing information. Stealing debit card information causes additional problems as the threat actor can then access the direct funds of the user rather than the credit card company.
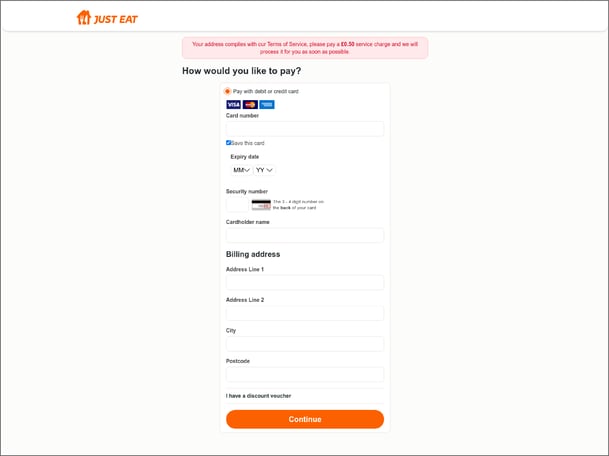 Figure 2. Just Eat Phishing Payment Page
Figure 2. Just Eat Phishing Payment Page
The phishing page is very well made, using highly obfuscated source code, a well-built and realistic template, and anti-analysis features on the page including a debugger detection script which blocks security researchers from inspecting the source code. Obfuscating the source code creates difficulty for researchers in attributing attacks to specific threat actors. This threat actor has chosen to invest in both a higher quality phishing kit as well as covering their tracks in order to avoid detection and to prolong their campaigns with impunity.
It is important to track when threat actors begin to use different lures to target consumers. Changing tactics, techniques, and procedures (TTPs) typically signifies those old methods are becoming ineffective and security researchers always need to be analyzing from where new money may flow. These evolutions point to the fact that all brands are at risk of being used as lures if the right circumstances permit.
WHAT NOW?
A 2021 UK study found that British consumers expect companies to reimburse them if they are tricked by a branded phishing lure. This increases the risk of customer churn and brand devaluation when companies do not adequately protect their brand, and, by extension, their customers from threat actors.
But the onus cannot solely rest on a brand’s shoulders. Consumers should remain vigilant about their personal security across all digital brand interactions. No longer are tech companies and financial institutions the main brands used to steal PII like credit card details and login credentials. Threat actors will use whatever lure they think will be effective, especially ones that are relevant in current news cycles or have gained popularity in recent times.
URLs
Just Eat URLs
https[:]//just-eata[.]co[.]uk/pay
https[:]//just-eata[.]co[.]uk/checkout
Deliveroo URLs
https[:]//deliveroo-restriction-removal[.]com
https[:]//deliveroo-review[.]com
https[:]//deliveroo-lock[.]com
https[:]//deliveroo-restriction-removal[.]com
Uber Eats URLs
https[:]//ubereats-help[.]com
https[:]//www[.]uber-orderconfirmation[.]com
https[:]//www[.]uber[.]refunds-help[.]com
https[:]//www[.]eats-order-comfirm[.]com
