
KITIntel
PHISHING KIT ANALYSIS AT SCALE
Tackle your problems with SMS phishing early in the process
KITIntel is a tool for investigating and comparing phishing kit content within single or multiple kits. Use the graphical user interface (GUI) to search in the KITIntel dataset for file hashes and content, as well as to retrieve content, and submit external phishing kits for cross-analysis. All files are stored in their original form, allowing users to run complex searches against file content and then retrieve the complete file for offline analysis or additional indicators of compromise (IoC) extraction. Referred to as “The Search Engine for Phishing Kits,” KITIntel was built by threat hunters for threat hunters, cyber threat intelligence (CTI) teams and all security analysts.
What's In A Phishing Kit?
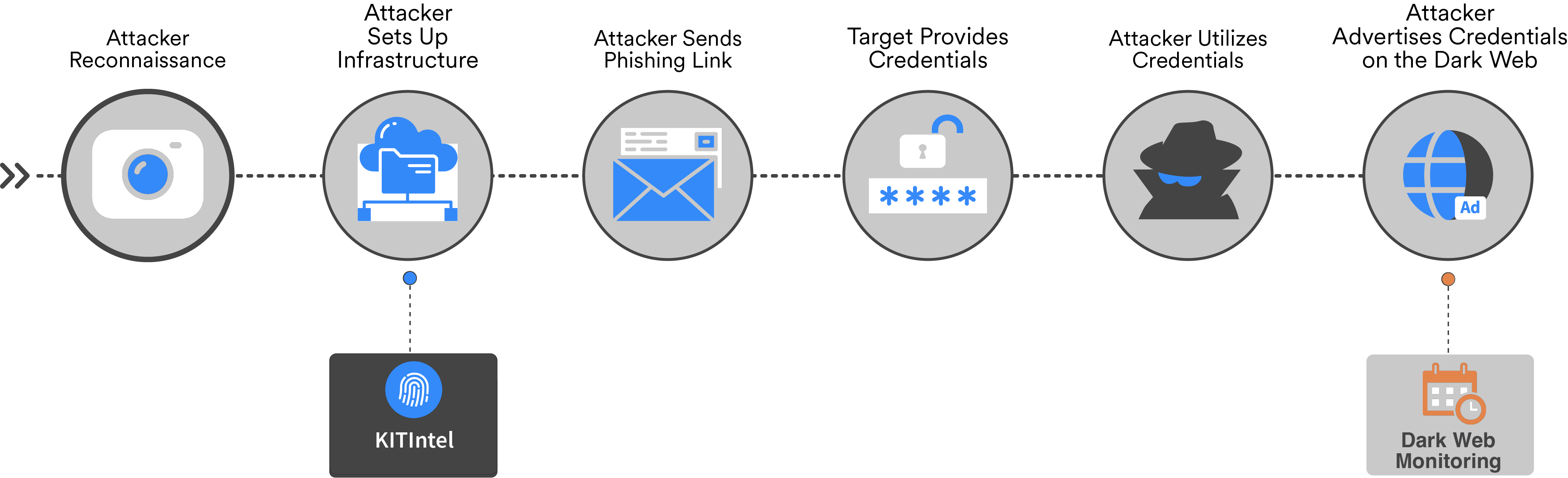
Phishing kits are the compressed set of threat actor files and source code that make up a phishing website. This includes HTML, JavaScript, CSS, PHP, exfiltration methods, images, videos, and directory structures. Discovery of a phishing site starts a process of analysis, attribution, and remediation. Phishing kits contain all the information you need to understand the threat. KITIntel gives your security team a holistic view of the phishing ecosystem, offering visibility into all elements, allowing you to explore the attack in a safe and protected sandbox environment.
Go Left
DISRUPT THE TRADITIONAL RESEARCH MODEL
Built by Threat Hunters for Threat Hunters
Phishing kits are a commodity and searching on your own is not an effective method of detecting attacks on your customers. KITIntel automatically detects and collects phishing kits at scale 24/7 so you don't have to. WMC Global's team of threat hunters supplements the platform for unrivaled phishing kit detection. WMC Global has proven that leveraging the intelligence contained within phishing kits can lead to arrests of threat actors.
WHAT CAN YOU DO WITH A PHISHING KIT?
Leveraging access to WMC Global's phishing kit database, the largest private repository of unique phishing kits, you can:
DISCOVER PHISHING KITS
Find phishing kits from the latest campaigns often before the attack goes live.
ATTRIBUTE CAMPAIGNS
Definitively link phishing campaigns to known threat actors.
PIVOT RAPIDLY
Discover new and unique links and activity clusters as well as overlaps between phishing kits allowing for enhanced visibility.
AUTOMATE EFFORT
Utilize the KITIntel GUI or API to search at scale and perform rapid work.
FIND SOURCE CODE
Understand threats in never-seen-before detail. Discover linked resources, phishing kits, and technologies allowing for greater understanding of threat actor behavior.
ANALYZE INTELLIGENCE
Research and develop working strategies to combat threats and identify new zero-day techniques.
PRIORITIZE INQUIRIES
Use data-driven analysis to classify investigations based on clustered attacks or other important data.
BUILD ALLIANCES
Identify other organizations targeted by the same threat actors and share information.
UNDERSTAND THE ATTACK VECTOR
Be able to answer questions like:
