
Compromised Credential Recovery
FIND STOLEN CREDENTIALS IN REAL TIME
In the event of compromise, timing is everything
PROACTIVITY AND EARLY PREVENTION DISRUPT THE TRADITIONAL RESEARCH MODEL
In reality, weeks, months, or years can pass before victim credentials become available on the Dark Web, rendering common monitoring services ineffective at offering visibility into the attack and threat actor behind it. This often leaves businesses bereft of an immediate solution and playing whack-a-mole with threat actors. Compromised Credential Recovery's unique data, however, comes from neither breaches nor the Dark Web. WMC Global locates compromised data at first exposure in phishing attacks and transfers it back to you via secure API, actively preventing account takeover.
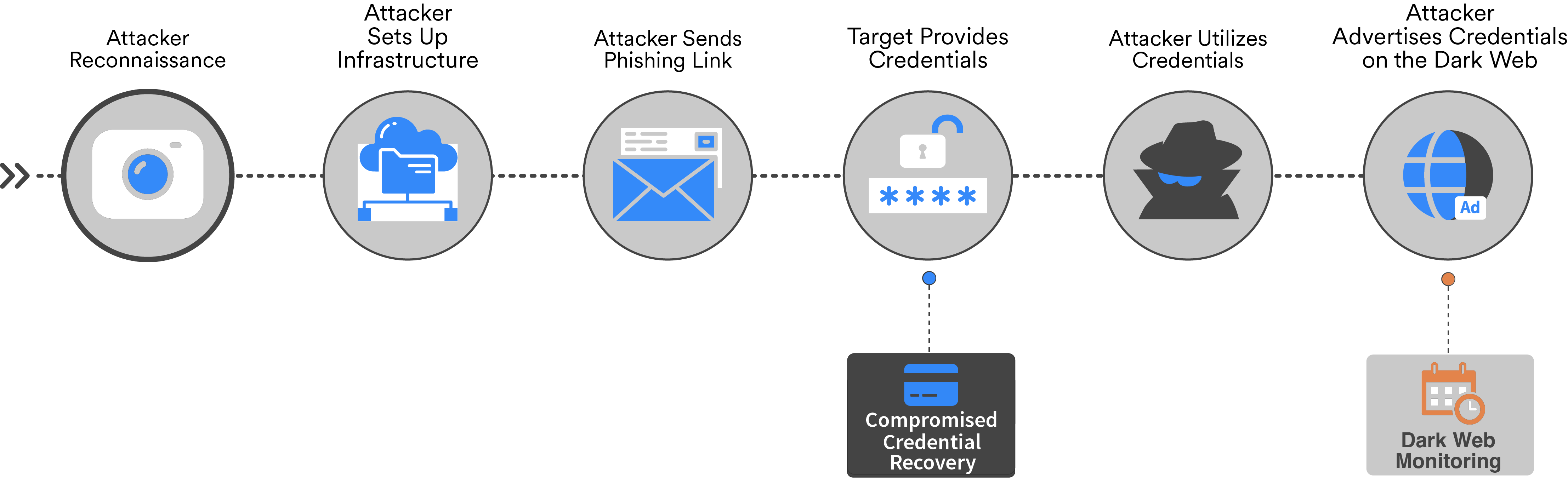
WHAT ARE THE OUTCOMES WITH COMPROMISED CREDENTIAL RECOVERY?
Shine a light on what's happening during live campaigns. Obtain a deeper understanding of threat actor tactics, techniques, and procedures (TTPs). Gain visibility into the exfiltrated data on unmonitored devices (BYOD) and networks, augmenting existing controls.
HOW WE WORK
RECAPTURE CREDENTIALS DURING ACTIVE PHISHING CAMPAIGNS




