Threat Summary
New phishing campaigns are targeting mobile devices to deliver fraudulent courier delivery notifications to potential victims. While many organizations secure email and Microsoft Office applications directly within mobile phones, SMS threats are typically out of scope for many security teams, letting attackers exploit the lapse in coverage to leverage both consumer and business credentials. WMC Global's Threat Intelligence Team is currently tracking an increase in SMS-based courier scams in the United Kingdom. By the end of March over 5000 phishing URLs had been collected targeting Hermes alone. Targeted couriers are Hermes, DPD, and Royal Mail, with Hermes seeing a notable increase in distribution.
Analysis of the Hermes Phishing Kit
The group of files which creates the phishing site are called phishing kits. These kits are often created by skilled individuals and then offered cheaply and sometimes for free on online forums, the dark web, and other forms of social media. To evade detection and security protections often seen in corporate environments, the phishing kit creators have added additional php code to help prolong their campaign and ensure successful credential collection. The Hermes kit attempts to evade detection by passively checking the victim’s IP and user agent in order to access the phish. If the victim’s IP is outside of the UK or the user agent check results in anything other than a mobile phone, the victim is redirected to the legitimate Hermes site instead of the phish.
.png?width=563&name=carbon%20(9).png) Figure 1: Courier Scam Redirect Code
Figure 1: Courier Scam Redirect Code
If the victim is able to successfully pass the geoblocking and user agent checks, a variety of personally identifiable information (PII) is then collected from the victim. As the victim traverses the phish, the first page of the phish (track.php) collects the victim’s post code. Once this is provided the victim is directed to the next page (info.php) which alerts them of the need to reschedule their delivery. The victim is then directed to the third page (delivery.php) which collects their full name, phone number, date of birth, and address. After submission, the fourth page (delivery-info.php) notifies the victim of a redelivery fee and requests the victim’s card holder name, card number, expiration date, CVV, account number, and sort code. Finally, the last page (complete.php) sends the victim’s PII to the threat actor and redirects the victim to the legitimate Hermes site.
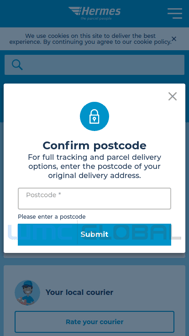
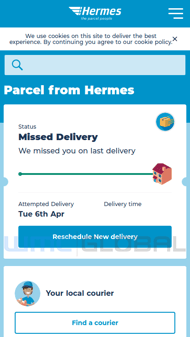
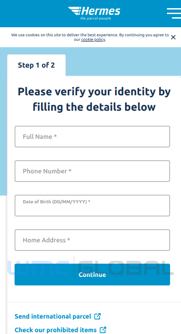
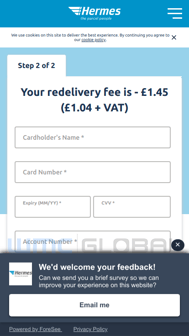 Figure 2: Hermes Phish User Experience
Figure 2: Hermes Phish User Experience
It does not take a great amount of skill to deploy the kits. Threat actors will typically alter parts of the phishing kit code to include the name of their online alias or group to brag or possibly attribute their work. The phishing kit associated with this Hermes campaign underwent several threat actor alias alterations. The most commonly found threat actor aliases in the Hermes phishing kits were PAV3LINO, CYAMON Fullz, BANDZI’S FULLZðŸ, @FullzNextDoor, Skyzino, and CACHELSZ Fullz.
.png?width=526&name=carbon%20(10).png)
Figure 3: Hermes Scam Code Snippet
Code overlaps with one Royal Mail kit allow WMC Global’s Threat Intelligence Team to assert that the same individual that created the Hermes kit also created one of the Royal Mail phishing kits. Despite the overlapping code, there have been no threat actor alias overlappings identified between the Hermes phishing kit and Royal Mail phishing kits. Each threat actor in the group may be using their own alias to attribute their work, or, it could be nothing more than an attempt to throw off security researchers. However, it is also plausible that the kits have been widely distributed which could also account for the numerous alias alterations.
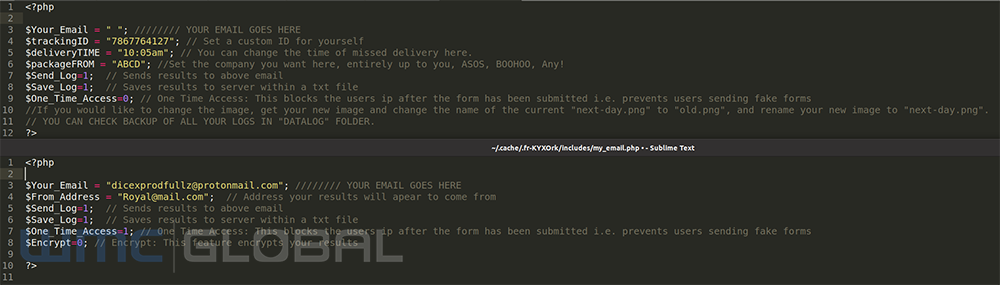 Figure 4: Royal Mail Scam Code Snippet
Figure 4: Royal Mail Scam Code Snippet
Errors in the way the threat actors are conducting these campaigns leads WMC Global’s Threat Intelligence Team to believe the group is amateur in skill and aptitude. They were observed deploying the wrong phishing kits on the wrong domains, such as a DPD themed URL hosting a Hermes kit. This also bolsters the team’s belief that the same threat actors are targeting multiple brands. Additionally, functionality to track victims was coded into the phish but does not appear to be used. The URL structures of the phish contain variables which create unique identifying strings each time a victim accesses the phish. In this particular phish, the sessionID variable is created by the generation of an MD5 hash of the victim’s IP address. The hash serves as a random number generator which creates the same unique number if a victim visits the phish multiple times. Typically, this is used to prevent victims, or researchers, from revisiting the phish. However, the code variable required to make this feature work isn’t present in the Hermes kit to prevent the secondary visits regardless of what the configuration setting is.
Because of the extent of information stolen from the victims, the compromised data is called ‘fullz’. At this time there has been no indication that the threat actor group has attempted to use the compromised credentials directly for financial gain. Most likely, the stolen data is being sold online to third party threat actors who will monetize access via direct bank theft, identity theft, or social engineering.
Conclusion
Mobile phishing is emerging as a common gap in phishing detection and mitigation. With almost two decades' experience in the mobile threat protection landscape and a market-leading anti-phishing product suite featuring KITIntel, our phishing kit search engine, WMC Global's telecommunications and threat intelligence expertise is uniquely positioned to help organizations identify and mitigate emerging mobile phishing threats.
