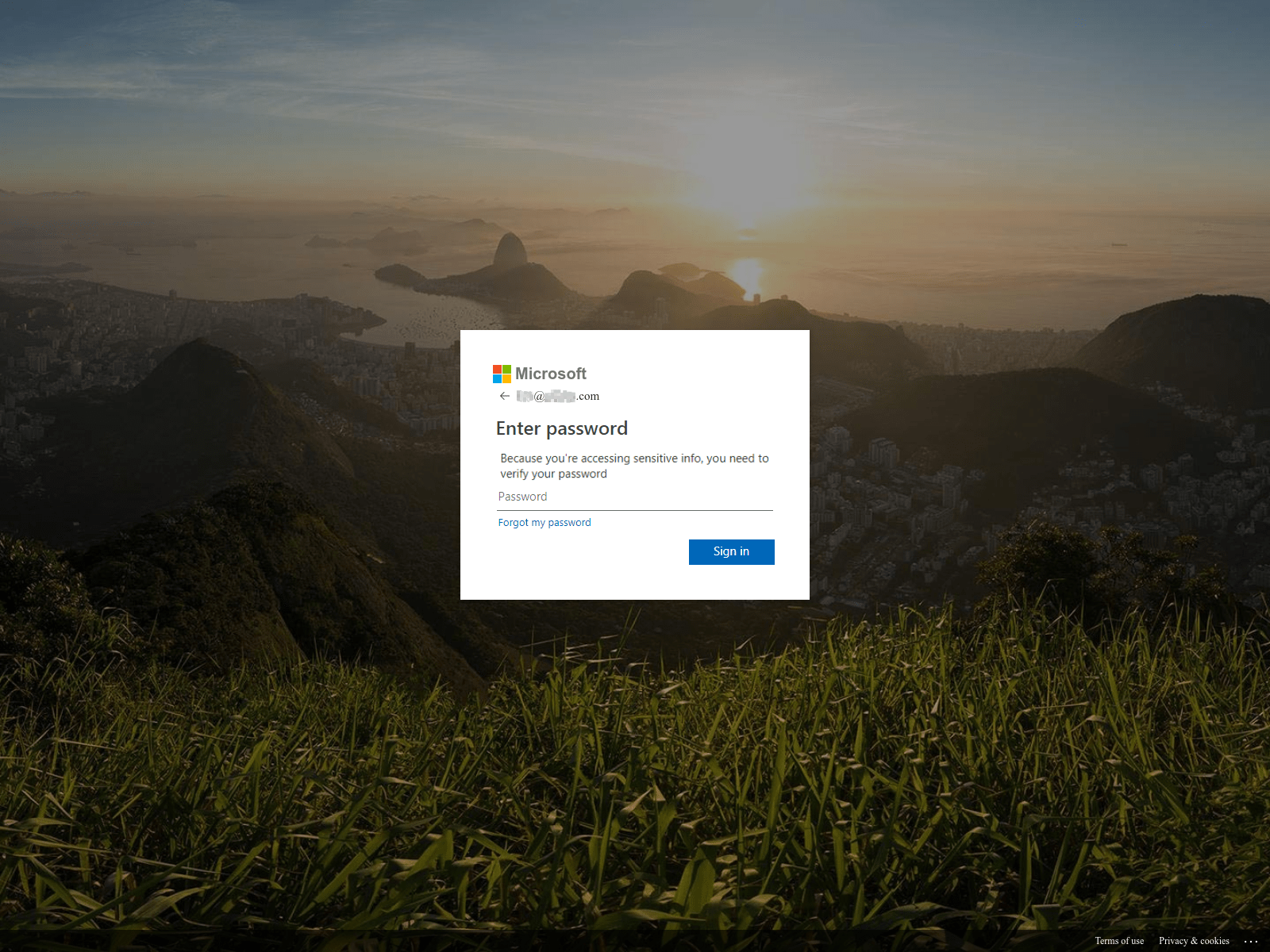
Many detection engines crawl websites and follow links to determine whether a website is malicious or masquerading as another. The difficulty threat actors face combatting these advanced technologies is that their phishing websites must bypass the detection engine, while simultaneously gaining a victim’s trust by displaying images and themes that mimic the targeted website.
 {phishing page image}
{phishing page image}
WMC Global threat analysts recently discovered a novel way some threat actors are tricking these scanning engines, and this bot avoidance mechanism in particular has been deployed on multiple Office 365 credential phishing websites. WMC Global threat analysts attribute the use of this method to a single threat actor selling the phishing kit to multiple users.
Because image recognition software is improving and becoming more accurate, this new technique aims to deceive scanning engines by inverting the colors of the image, causing the image hash to differ from the original. This technique can hinder the software’s ability to flag this image altogether.
 {inverted image backgrounds}
{inverted image backgrounds}
However, a victim visiting the website would likely recognize that the inverted picture is illegitimate and exit the website. As a result, the threat actor has stored the inverted image and, within the index.php code, has used a CSS method to revert the color of the image to its original state.
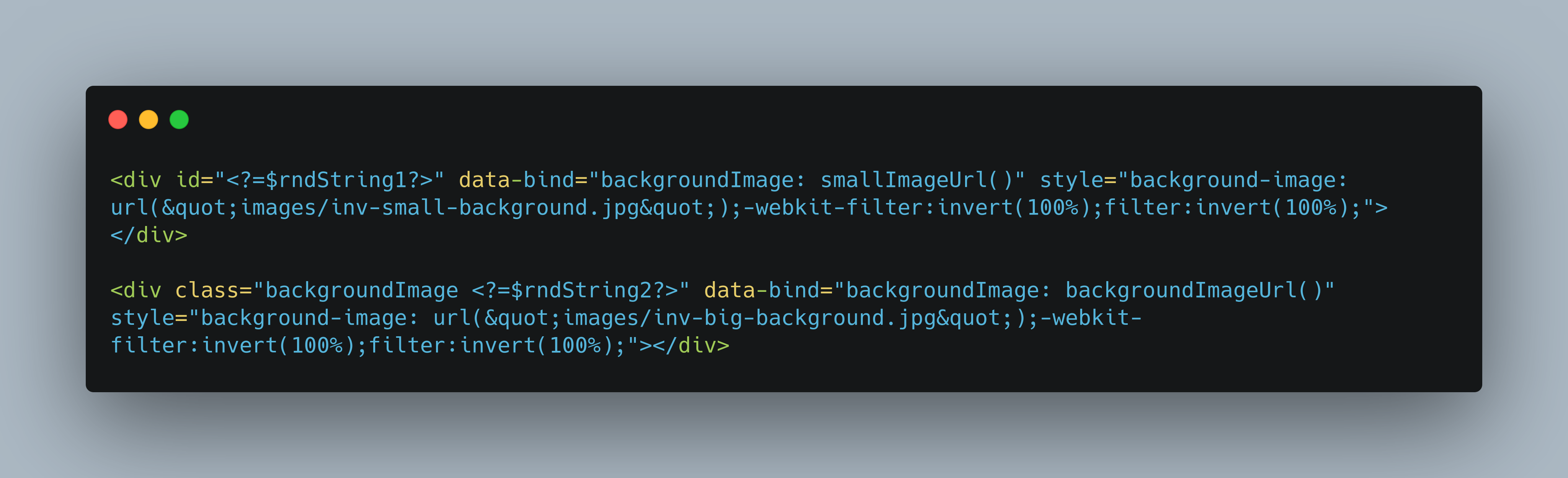 {CSS Code}
{CSS Code}
 {inverted image and original comparison}
{inverted image and original comparison}
This approach results in the final website’s appearing legitimate to users who visit, while crawlers and scanning engines are highly unlikely to detect the image as being an inverted copy of the Office365 background.
It is notable that the inverted image was discovered within a deployed Office 365 credential phishing kit. Our team reviewed other campaigns deployed by this threat actor, discovering that the individual was using the same inversion technique on the newer Office 365 background.
Threat actors constantly attempt to bypass detection, and they can fool scanning engines by inverting or altering recognizable logos and images. However, image-based systems are more likely to detect the deception if the website where the phishing kit was deployed was sandboxed or rendered. Although, a sandbox method does take longer than a basic scanning engine, and the website can still harm victims during that period.
IoCs
Older style background images original and inverted
d9288957bd276f9144e1fe321e598b8bab81af20fd36db702d716664a6f7c65d inv-big-background.jpg
7c10fa25b9ebad3a8d71a19bb2a7a0664df3415a2bfae566aa91beb11ae07b89 big-background.png
Newer style background images original and inverted
a59ea699d353d00ff2999111f9fa11fb73a47eda7800642609ca230560ea3703 inv-big-background.png
e6180f6c05e9fd25723e3d804dac6ea95212516610d7a007f8ce6cd954962190 big-background.png
