At WMC Global, we are tracking a threat actor who goes by the alias "Kr3pto," a phishing kit developer who builds and sells unique kits targeting UK financial institutions amongst other brands.
SUMMARY
Threat actor Kr3pto is continuously challenging companies and consumers to protect themselves with their quick thinking and innovative approaches to skirting security defenses. Heavily targeting mobile users, Kr3pto phishing kits are dynamic in nature, enabling threat actors to acquire real-time security codes and two-factor authentication data. Their flexibility and real-time nature makes them especially difficult to block and their ability to attack multiple sites at once ups the risk factor on this threat actor substantially.
Dynamic Phishing Kits Targeting UK Financial Institutions & Brands
Phishing kits allow threat actors to quickly assemble a theft operation with minimal skill or experience. While today’s organizations are updating their defensive postures, threat actors are returning the favor, finding new, creative ways to target personal and financial data. Today we are looking at Kr3pto phishing kits, dynamic kits that can bypass multi-factor authentication and that’s quickly gaining popularity online. What have become known as Puppeteer Kits or Live Kits, they are highly valuable and enable threat actors to deploy dynamic fraud attempts.
First detected in July 2020, there have been on average more than 50 new phishing URLs launched every day using kits attributed to Kr3pto.
What’s more, these phishing kits are dynamic, allowing threat actors to siphon login credentials, personal details, and two-factor authentication information in real-time. This makes Kr3pto kits more problematic than traditional, static kits that are becoming easier for organizations to thwart.
WMC Global has observed phishing campaigns attributed to Kr3pto using smishing (SMS phishing) messages to get users to click on phishing links landing them on the phishing sites. We’ve identified Kr3pto-linked kits targeting Halifax, Lloyds, Natwest, TSB, and HSBC.
Source: Twitter
When victims follow the link, they are presented with a clone of real banking sites. They are prompted to enter their login credentials and, if necessary, two-factor authentication credentials requested by threat actors.

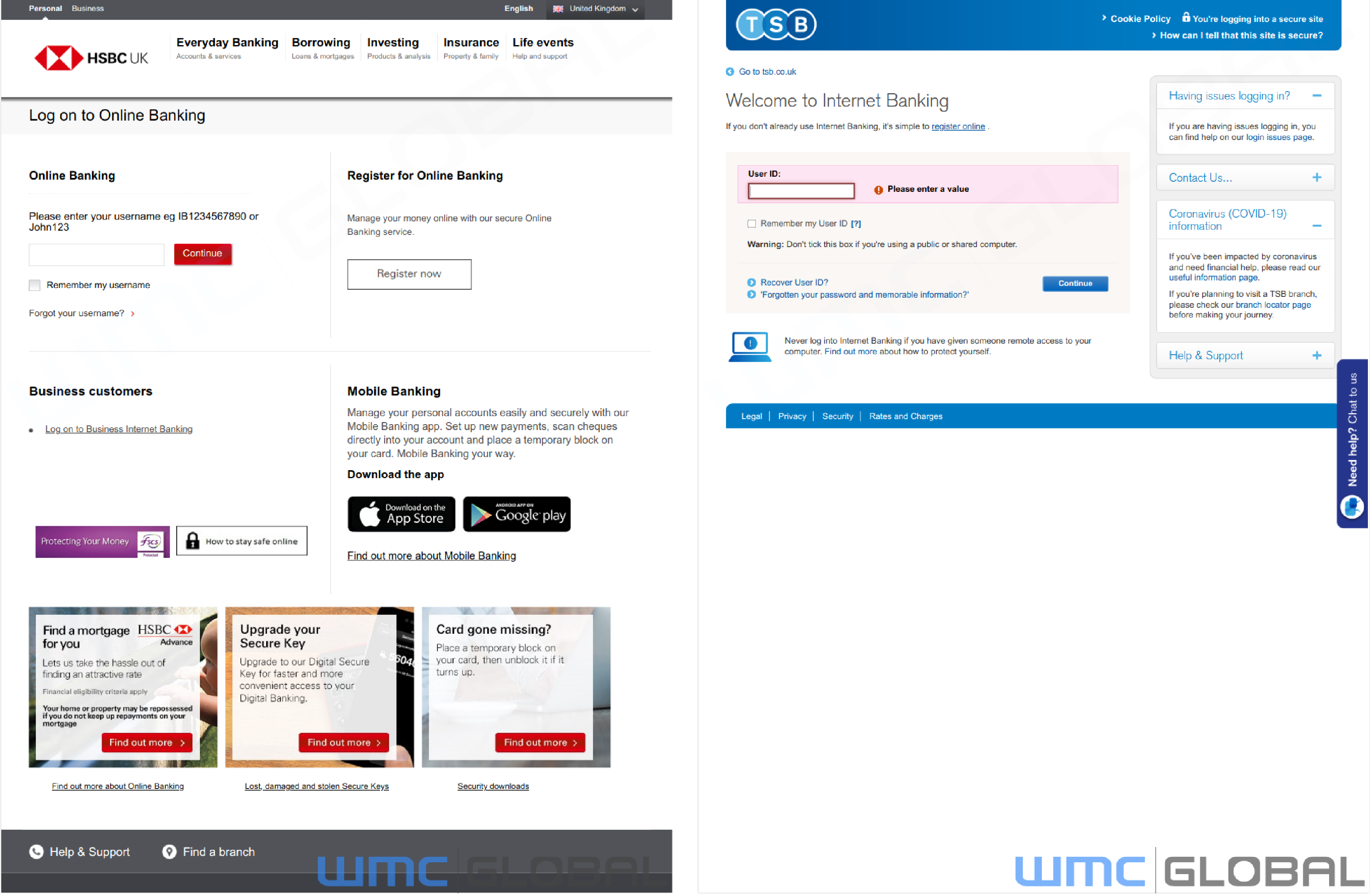
Notably, Kr3pto Puppeteer Kits use cookies to identify returning victims, allowing threat actors to redirect duplicate victims and avoid security professionals investigating their efforts.
Fast, Efficient Theft
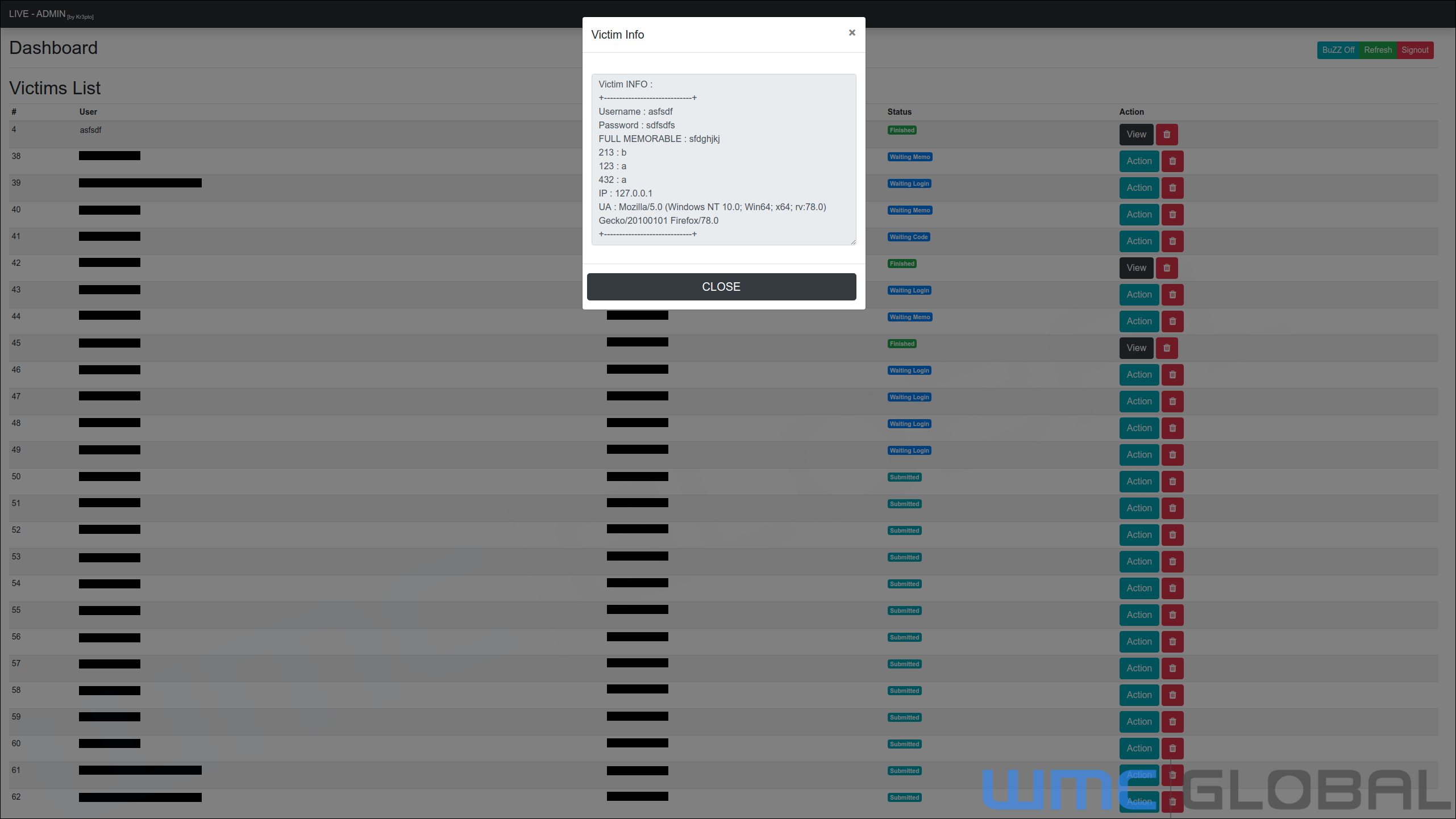
Kr3pto Puppeteer Kits include lures, optional gateways, and a control panel that allows threat actors to operate multiple lures at once. The control panel is distinctive, equipping threat actors to manage multiple entire phishing operations from a single platform in real-time.
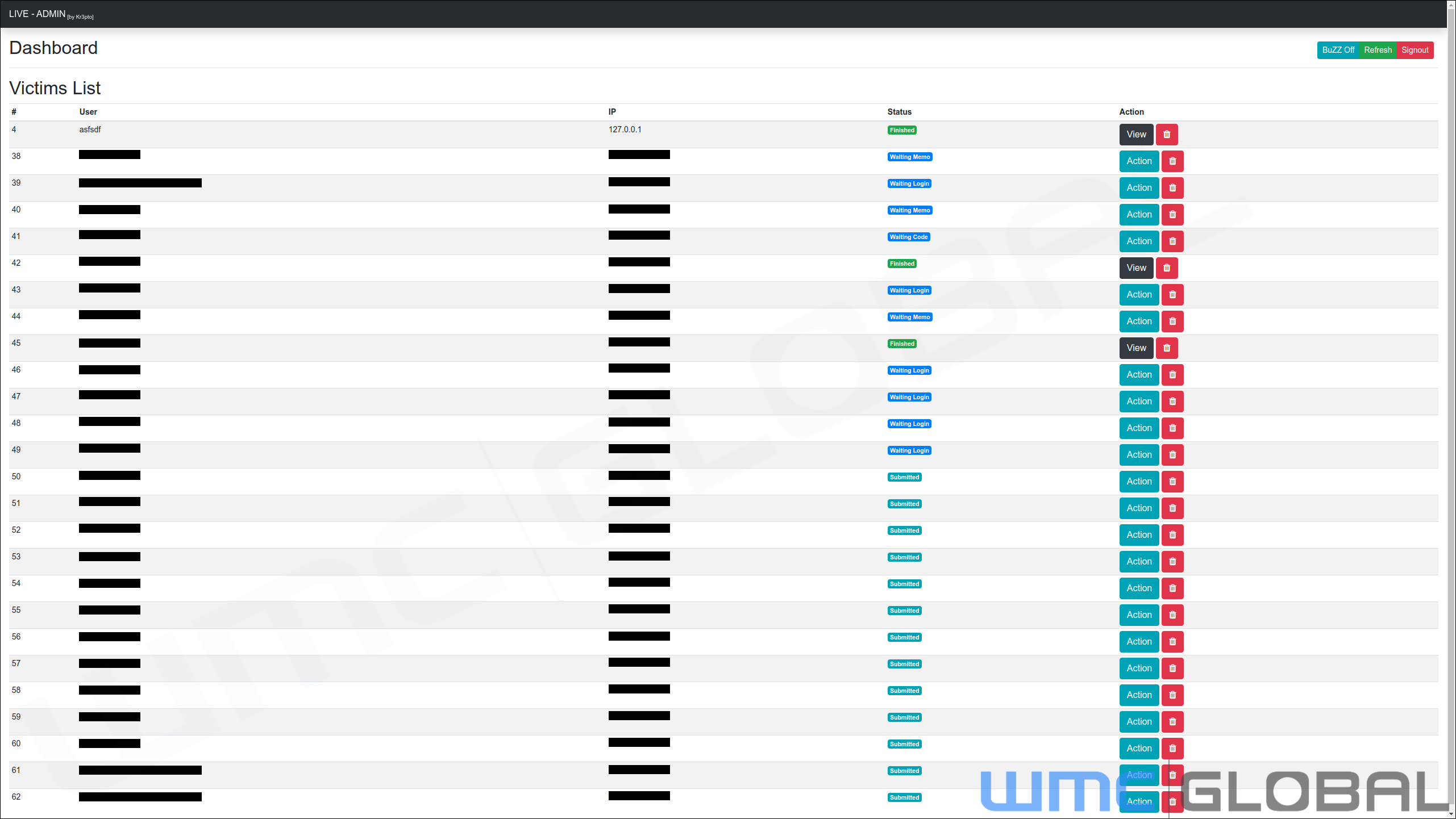
These phishing sites ask victims to wait or show a loading page while the threat actor manually logs in to the victim’s bank account. While modern security standards require secondary account validation, Kr3pto Puppeteer Kits equip threat actors to manually adjust the phishing page's response to the victim.
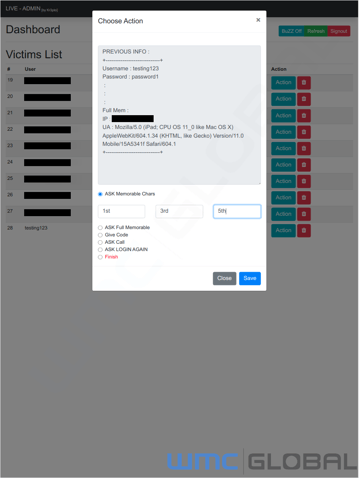
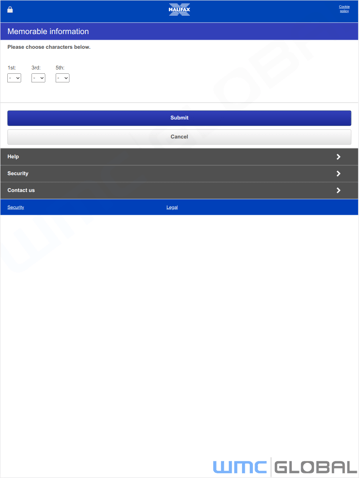
For instance, if the bank requires two-factor authentication via SMS, the bank will send the 2FA code as the actor logs into the account. Or the bank might request certain letters from the users' memorable word or phrase. Those codes are then input into the fraudulent page, allowing threat actors to gather and apply this information to victims’ accounts.
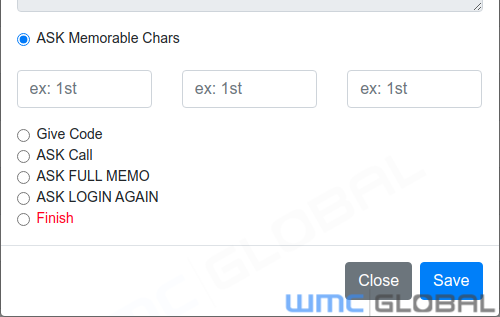
A threat actor can deploy several other security control options, including customizable memorable letters, asking the victim to call a specific number, which could be changed to the threat actor’s contact information. Specifically, we’ve identified examples of threat actors deploying the following options:
-
ASK Memorable Chars - Request 3 memorable characters from a victim’s memorable word. The 3 chars can be selected by the threat actor.
-
ASK Full Memorable - Request the full memorable word.
-
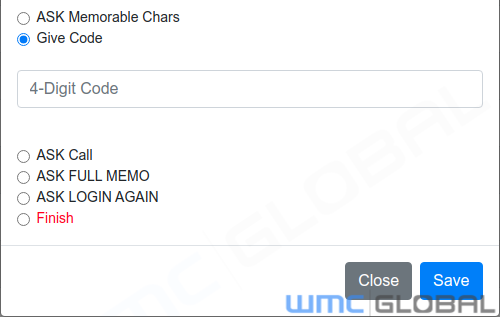
Give Code - Give a code to the user as a form of integrity check for the bank.
-
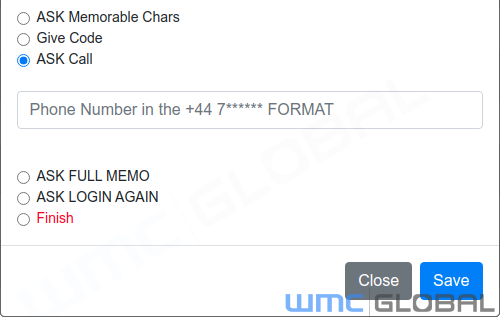
ASK Call - Ask the victim to phone a number.
-
ASK LOGIN AGAIN - Request username and password again.
-
Finish - Show completed and return the user to a legitimate banking website.
Traditional phishing kits can only transition stolen credentials to a configured email address. Kr3pto Puppeteer Kits offer a dynamic solution, enabling threat actors to acquire real-time security codes and two-factor authentication data.
This simple but expensive design allows threat actors to target multiple financial institutions at once to maximize returns. In addition, the control panel configuration allows teams of threat actors to collaboratively, expanding their scope and effectiveness.
Taken together, Kr3pto threat actors have extensive capabilities to target UK banking customers with sophisticated phishing scams that compromise personal and financial data.
Intel and assertions
Currently, there are two distinct websites with the same fingerprint: Kr3pto LLC & AUTOSHOP.
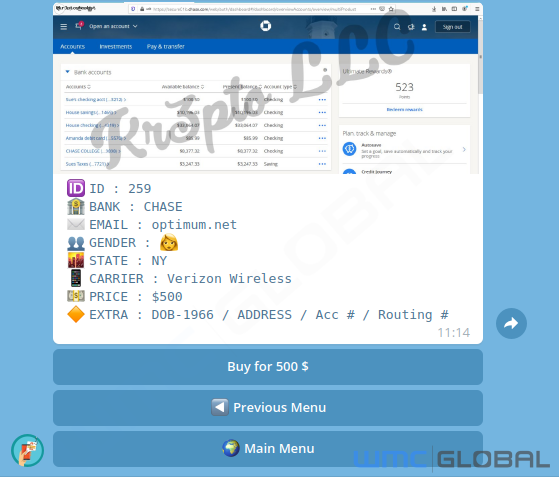
A Telegram channel for Kr3pto LLC sells credentials for brands, including Chase, PayPal, and Fullz. Arranged by log required, stolen credentials sell at various prices depending on the country of residence.
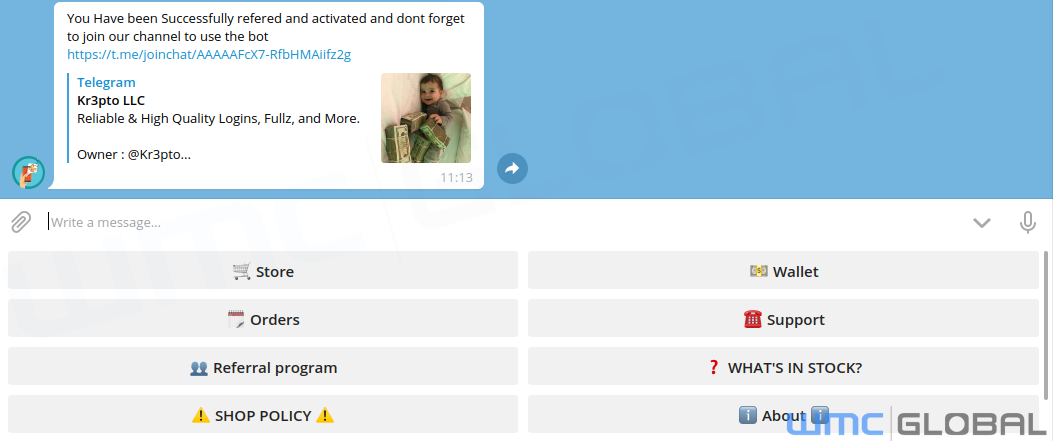
When engaged in a chat, the actor claimed to be selling the UK live banking kits for £1k each. Along with access to a secret forum for £1k. The forum claim was unsubstantiated. What’s more, the pay-for-access component feels fraudulent as competent threat actors are not joining forums where LE and security researchers are allowed access. The actor showed an awareness of public and open-source reporting on them and their kits.
The actor’s English was good but not perfect, showing they are not a native English speaker. Even so, they are fluent in the language with good spelling and grammar; however, a more complex English sentence structure was lacking.
Currently, the threat actor’s online store has a large number of credentials for sale. Since many phishing sites are stood up every day with similar TTPs, it appears managed by a single actor.
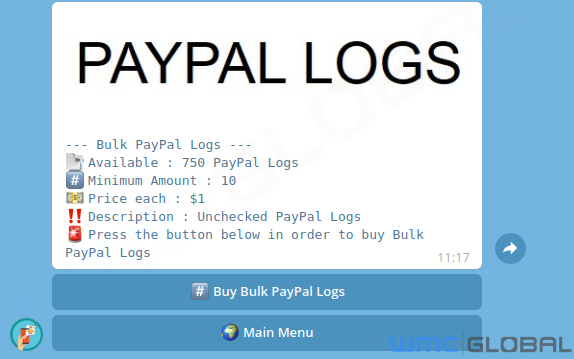
Fortunately, we have not seen an increase in credential stuffing attacks hitting UK financial institutions (FIs) or other services, making it possible that Kr3pto is standing the sites up themselves, harvesting the credentials, and selling them in their store.
While the workflow remains unclear, it is highly possible the whole process is fully automated, allowing for a continuous stream of fresh credentials to enter the marketplace.
CONCLUSION
Kr3pto Puppeteer Kits raise the stakes for companies and consumers defending their data from threat actors looking for new, creative ways to thwart our defenses. Adapting to the latest trends is one way to stay ahead of the threat.
Moving forward, it’s clear that two-factor authentication and other cybersecurity standards can’t be taken at face value as threat actors are becoming more agile and able to undermine critical cybersecurity efforts.
At WMC Global, our threat intelligence team is constantly monitoring these trends, identifying threat actors and their tactics to help keep you safe.
