The WMC Global Threat Intelligence Team observed a noticeable escalation in targeted and sophisticated phishing campaigns throughout 2022, with a surge in SMS phishing and a decrease in campaigns featuring large corporations. Threat actors began to shift their focus to developing smish-to-vish campaigns — campaigns where threat actors use phone numbers in SMS messages as opposed to link-based phishing. In 2022, we also finally saw a move away from Covid-19 phishing lures as pandemic-related government funds and support stopped. Several new threat actors made an appearance in 2022 with prolific and novel campaigns explored below targeting banks and big name brands.
The latest US trend has seen threat actors moving from generic, wide-reaching phishing attacks using major banks as lures to targeted attacks featuring small credit unions. Although customers of financial institutions are the most common mark, there was a jump in threat actors specifically targeting credit union customers throughout the US, whereas in the UK a prevalent phishing campaign took advantage of the government-backed energy rebate scheme as energy prices peaked at an all-time high. As expected, big brands like Microsoft, Apple, Netflix, and PayPal were still targeted regularly throughout the year.
CONTENTS
Notable Phishing Attacks in 2022
- Credit Union Phishing Attacks (US)
- Energy Rebate Scams (UK)
- Package Delivery Phishing Attacks
- Food Delivery App Scams
BACKGROUND
2022 rang in the beginning of "normalcy" post-pandemic as commenced a natural end to pandemic phishing practices and a return to traditional brand lures. The barrier to entry for threat actors is getting consistently lower. New phishing marketplaces appeared throughout 2022 with the number of active users hitting record highs. WMC Global has been tracking marketplaces with a significant number of subscribers ranging from 600 up to 4100 for each marketplace. New threat actors joined these marketplaces and attempted to sell their phishing kits containing custom configuration panels and simplified instructions for buyers on how to edit, deploy, and monetize these kits.
Notable Phishing Attacks in 2022
Credit Union Phishing Attacks (US)

The US saw a marked increase in the number of credit unions whose customers were targeted with SMS phishing scams during 2022. Hundreds of credit unions operate in the US alone compared to a much smaller number of big banks, giving threat actors many more options for campaign lures. Credit unions have significantly reduced security budgets compared to mainstream banks and threat actors knowingly featured credit unions nationwide. WMC detected a huge increase in credit union phishing attacks while noting a decrease in attacks on major banks. This led WMC Global to make the assertion that large scale attacks were less likely and the majority of campaigns running currently were smaller scale, more targeted, and with higher sophistication. These attacks were targeting residents of specific states as well as citizens using services from sectors like the Employment Development Department (EDD) who used local credit unions to increase the chance of a user falling for a phishing attack, as opposed to the large multi-thousand SMS campaigns which used a high-profile bank lure. It is likely that threat actors switched to smaller scale lures because their larger scale campaigns were shut down before they were able to gain enough victims to make the attack cost effective. Additionally, we believe threat actors found that bypassing fraud controls at major banks was difficult to cash out victims. This led to the shift in targeting credit unions and smaller institutions to evade detection for longer allowing more victims to fall for the campaigns, and that threat actors are finding cashing out techniques easier or more cost effective for these credit unions.
Energy Rebate Scams (UK)

As the UK entered a cost-of-living crisis in late 2021, the government announced plans to support households with monetary payments and energy bill discounts. This unfortunately led to a wave of SMS phishing campaigns using these rebates as a lure. The campaigns started with small-scale test runs targeting the customers of energy regulator Ofgem. Then, in September, campaigns targeting customers from multiple energy suppliers started to increase in quantity. The NCSC released an official consumer warning regarding the scams, with the energy rebate lures accounting for over 90% of the detected SMS phishing in the UK. Interestingly, the campaigns disappeared as quickly as they came, with a shift moving back to the more traditional lures.
Package Delivery Phishing Attacks

Package delivery companies were heavily targeted with SMS phishing campaigns throughout 2022. One large UK package delivery company rebranded and within a week, threat actors had deployed phishing kits using the new theme and company name. WMC Global analyzed a phishing kit used in one of the Evri-themed campaigns and within it was a clean and simple-to-modify configuration script allowing deploying threat actors the ability to adjust the settings and phishing site setup without having to rewrite any code. WMC Global analysts were additionally able to utilize the actor's alias and pivots leveraging other phishing kits to discover an additional alias linked to the same actor which increased the visibility into the building threat actor responsible as well as previous scams which they created under their old alias.
Food Delivery App Scams

WMC Global detected a Just Eat phishing website in April of 2022 which led the threat intelligence team to investigate the food delivery app market and found several other small-scale campaigns using door delivery companies as lures for phishing credit card information. The threat intelligence team found additional campaigns featuring Uber Eats and Deliveroo branding. It is unusual that these kits were all very well made, which is not often seen for new campaigns. Furthermore, WMC has not tracked any subsequent widespread campaigns using food delivery companies as lures. It is difficult to say why this trend hasn’t continued. It may be that threat actors found the click rate wasn’t high enough and other campaigns delivered better value for money. It’s also possible that the threat actor who held the kits didn’t sell them or isn’t engaged in the illegal market anymore, so the core of the campaign has been lost and a new phishing kit needs to be deployed which no current threat actors are willing to put the time or resources into.
Notable Threat Actors in 2022
WMC Global tracks and detects a vast number of threat actors every year and most scammers come and go without ever making a name for themselves. They are usually people trying to scam a quick buck but fail to ever make a mark. However, some threat actors remain more memorable with even a few creating original or prolific SMS phishing kits, while others are notable for their unique phishing kit workflows or featuring a previously unseen technique. Here is a brief rundown of notable actors who were of interest through 2022.
Robin Banks

In mid-2022, WMC Global began tracking a new threat actor by the name of Robin Banks. The actor stood out due to the large number of companies featured in their attacks and the unique backend system they employed. In July, another threat intel vendor released a blog on the scammer explaining the threat actor's phishing kits and tactics, techniques, and procedures (TTPs).
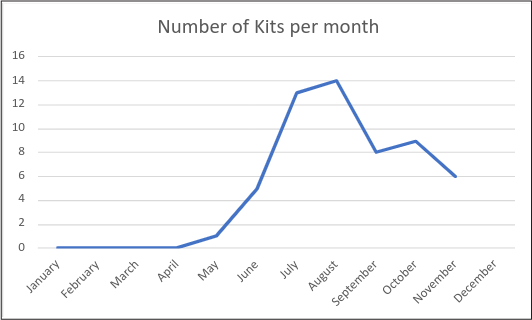
Figure 1: Robin Banks branded kits detected per month
This led Robin Banks to change the backend system to a new dynamic IP system the following month and referred to the threat intel company in some domain names on which they used to host their marketplace on. WMC released a subsequent blog detailing the updated code and backend system.
MRWEEBEE

In mid-2021, MRWEEBEE surfaced as a prolific SMS phishing kit creator, but it wasn’t until April 2022 that WMC Global observed a sharp increase in the number of MRWEEBEE kits being deployed, reaching a peak of more than 70 kits deployed in the month of July. Like other threat actors, this one sells phishing kits over Telegram channels that contain instructions for buyers.
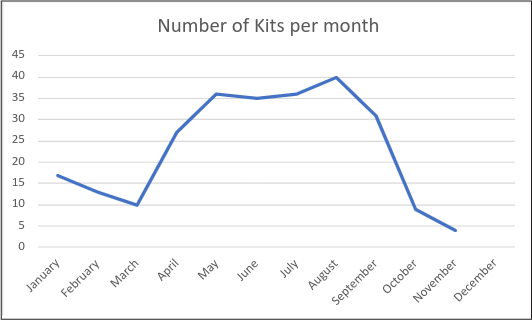
Figure 2: MRWEEBEE branded kits detected per month
What is interesting about MRWEEBEE’s kits is that they are heavily focused on extracting personal identifiable information (PII), user agent information, and banking security questions which give threat actors access to personal banking without having to worry about the bank’s detection measures.
Greatness Boss

In late August 2022, WMC Global captured the first phishing kits carrying the threat actor signature “Greatness Boss.” These kits impersonate the Office365 login portal, and although they are simplistic, they do utilize a Microsoft account validator and an admin panel for their users as seen in Figure 3.
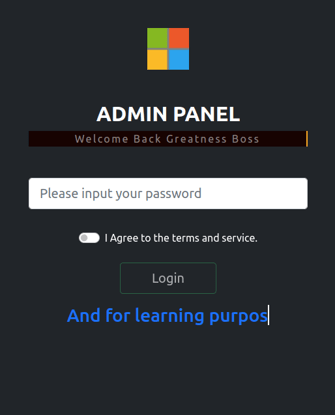
Figure 3: Greatness Boss Admin Panel
While Greatness Boss has created only one phishing kit, they have deployed it a substantial number of times. Since early August, WMC Global has tracked over 700 phishing URLs that contained the threat actor’s phishing kit. What is unique about the delivery method is that the phishing kits were hosted on compromised domains or open directories on domains completely unrelated to Microsoft. The common factor among these domains is that they were all hosted on Apache, Nginx, LiteSpeed, and TwistedWeb web servers. The phishing kit’s intention is to steal Microsoft employees’ login credentials for their corporate environment.
YoCHI
This year, we have attributed 443 phishing kits to the threat actor YoCHI. More than 200 kits were deployed between August and September and were heavily focused on targeting US banks, as well as Amazon and Netflix.
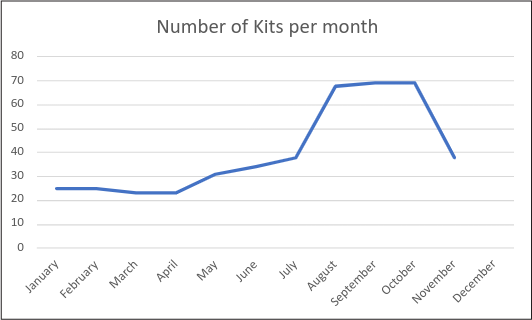
Figure 4: YoCHI branded kits detected per month
YoCHI has paid extra attention to long lasting phishing pages as is demonstrated by YoCHI’s instructions to threat actors that deploy the phishing kits.
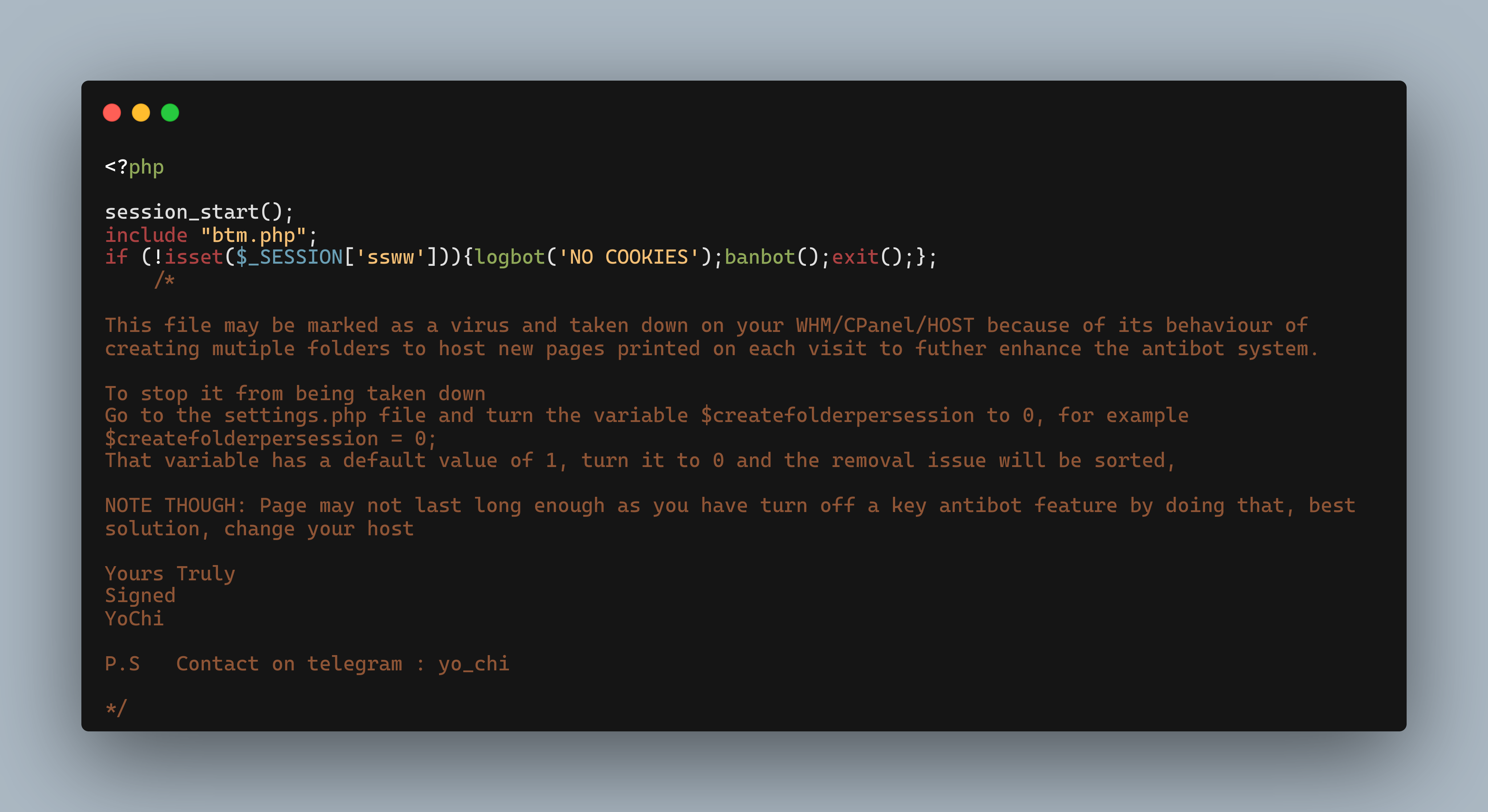
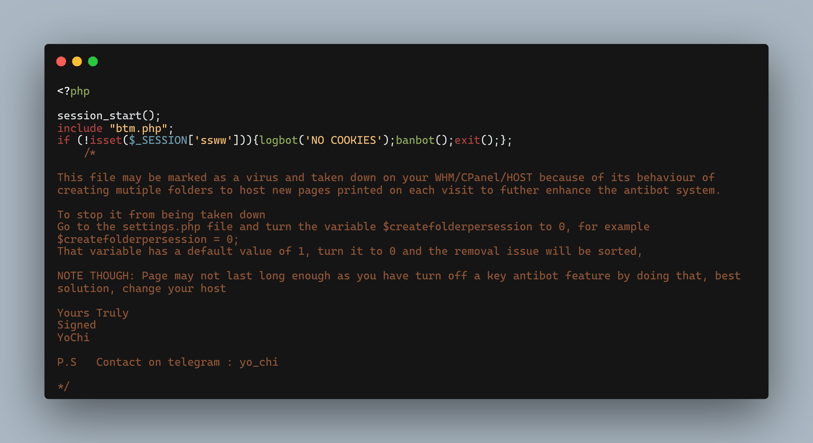
Figure 5: YoCHI support readme
Figure 5 offers instructions from YoCHI to his phishing kit buyers on how to make their phishing page less detectable.
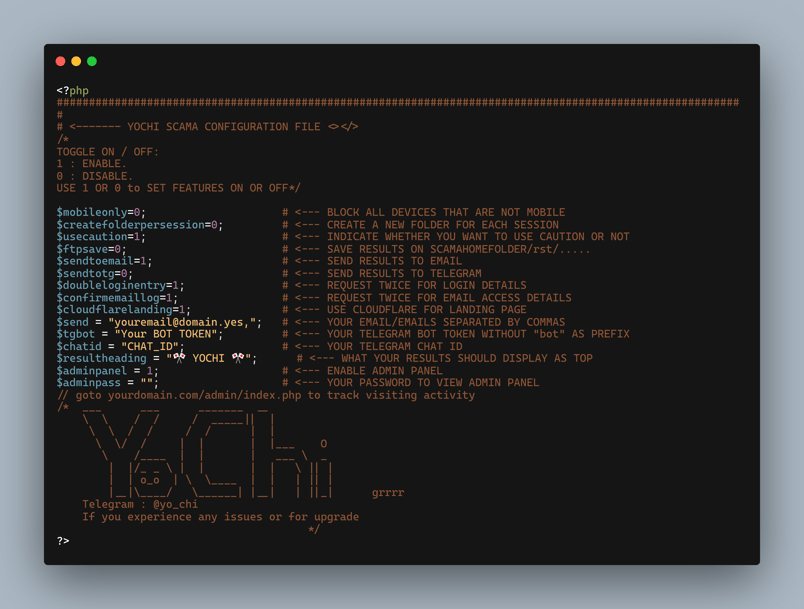 Figure 6: YoCHI configuration panel
Figure 6: YoCHI configuration panel
Figure 6 shows the configuration file where the deploying threat actors can change the settings for things like antidetection mechanisms, Telegram exfiltration, and email exfiltration.
blue_prints
In early 2022, WMC Global tracked blue_prints creating and distributing a sizable number of kits targeting corporate financial institutions, well-known credit unions, and commonly featured brands like Amazon and Netflix. This threat actor paid great attention to anti-detection mechanisms like proxies, bots, and crawlers blocking via a third-party API (Figure 7)
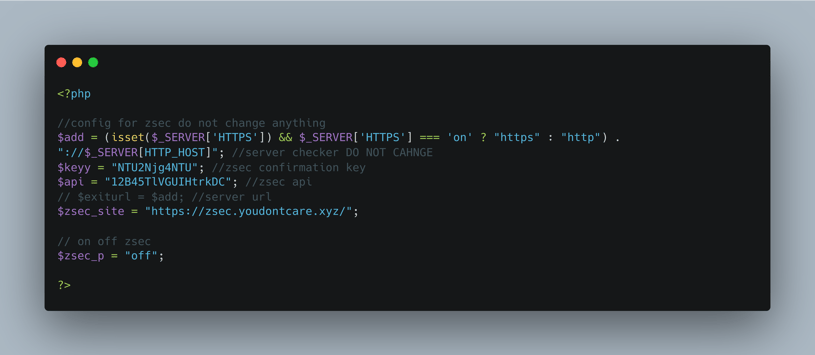
Figure 7: blue_prints configuration panel
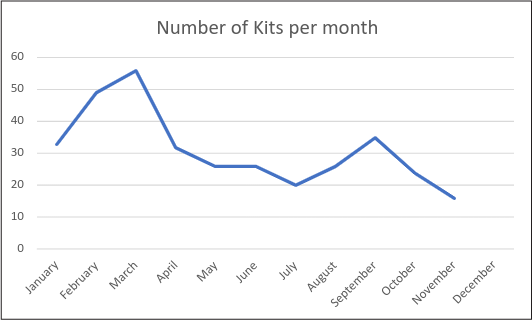
Figure 8: blue_prints branded kits detected per month
AREA16
During the second quarter of 2022, WMC Global uncovered another threat actor using the alias AREA16. Almost 90% of the threat actor’s phishing kits targeted Amazon, whereas the rest featured PayPal and Chase bank. AREA16’s phishing kits are sophisticated, implementing many different anti-detection mechanisms and even an admin panel as seen with other threat actors.
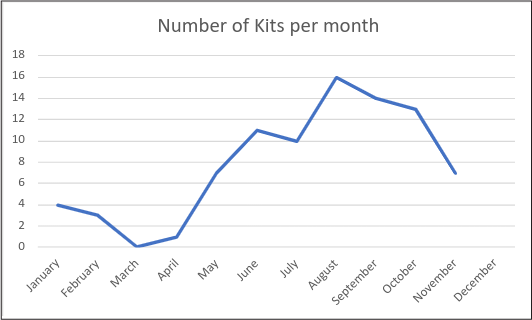
Figure 9: AREA16 branded kits detected per month
PHISHING KITS

The past year has continued to prove that phishing kit research and analysis is invaluable in the fight against SMS phishing. In 2022, WMC Global removed duplicate phishing kits from our internal kit collection, creating a visibility that has allowed us to turn previously undetermined threats into actionable intelligence and has led to easier campaign detection, shutdown, and stoppage.
Throughout the year, phishing kits mutated and adapted, changing based upon the demands of the market and real-world events. 2022 saw a noticeable decrease in puppeteer kits which were very popular throughout 2020 and 2021. WMC Global suspects this is due to the cost of purchasing the phishing kits, the complexity of creation for these kits limiting the available actors who can build such systems, and the cost to run these campaigns. In order to generate the full victim log, a threat actor is required to sit on the admin panel constantly waiting for a victim to land which is a big commitment to a campaign.
2022 also saw a marked increase in phishing kits featuring configuration pages and panels, allowing controlling actors the ability to easily change, update, and permutate the phishing kit on each deployment or session. Configuration scripts varied from the more simplistic centralized variable option to more complex admin panel logins with systems allowing actors to change options using a HTML form.
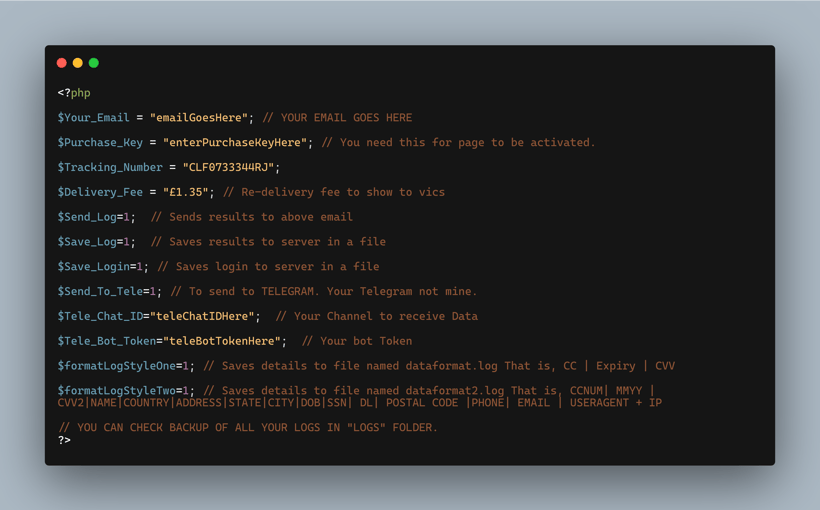 Figure 10: Ex-Robotos phishing kit configuration panel
Figure 10: Ex-Robotos phishing kit configuration panel
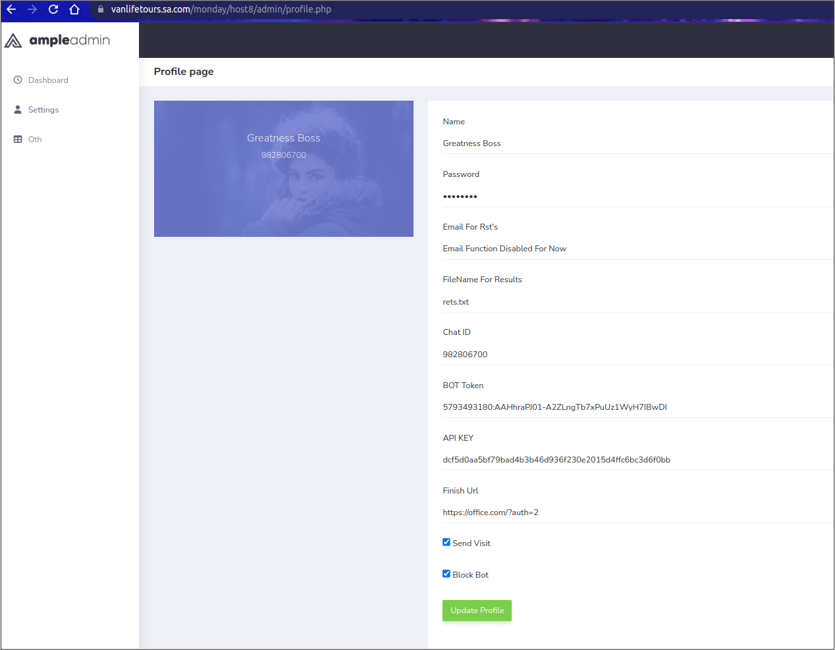
Figure 11: Greatness Boss admin panel settings
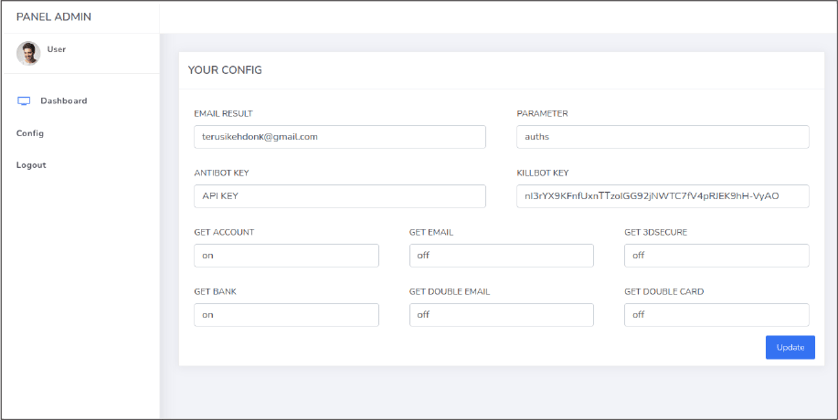
Figure 12: AREA16 admin panel settings
2023 Outlook
Many threat trends are influenced by real world events, however there are some overarching trends which WMC Global thinks might become more prevalent based upon internal metric tracking and general actor behavior.
Smish-to-Vish – SMS to Call Abuse Will Rise
WMC Global expects that SMS messages leading to phone calls will rise. WMC Global has been monitoring the smish-to-vish trend increasing throughout 2022 and expects it to spread further globally as it finds success in existing markets. The technique uses several methods. Some SMS messages will have a phone number CTA in the first SMS sent encouraging users to call the number for an urgent reason. Some ask for a return text and then another SMS is sent with a phone number requesting the user for a callback. Another requests the victim to reply to an SMS and then the threat actor will call the victim directly. In all these cases, the scam starts with an SMS, and leads to a phone call where the threat actor will conduct a social engineering scam to steal money from the victim on the phone. These are an evolution of well-known computer support scams.
