Applying for a new school is often a stressful experience for parents. Securing their child a place at a top school can be extremely competitive and require fast action when application season opens. Today, online application submissions have become a regular part of the process and private schools especially can require a non-refundable deposit to be paid just to submit an application. As a result, threat actors are targeting private school applicants with well-built, complex, and compelling phishing attacks.
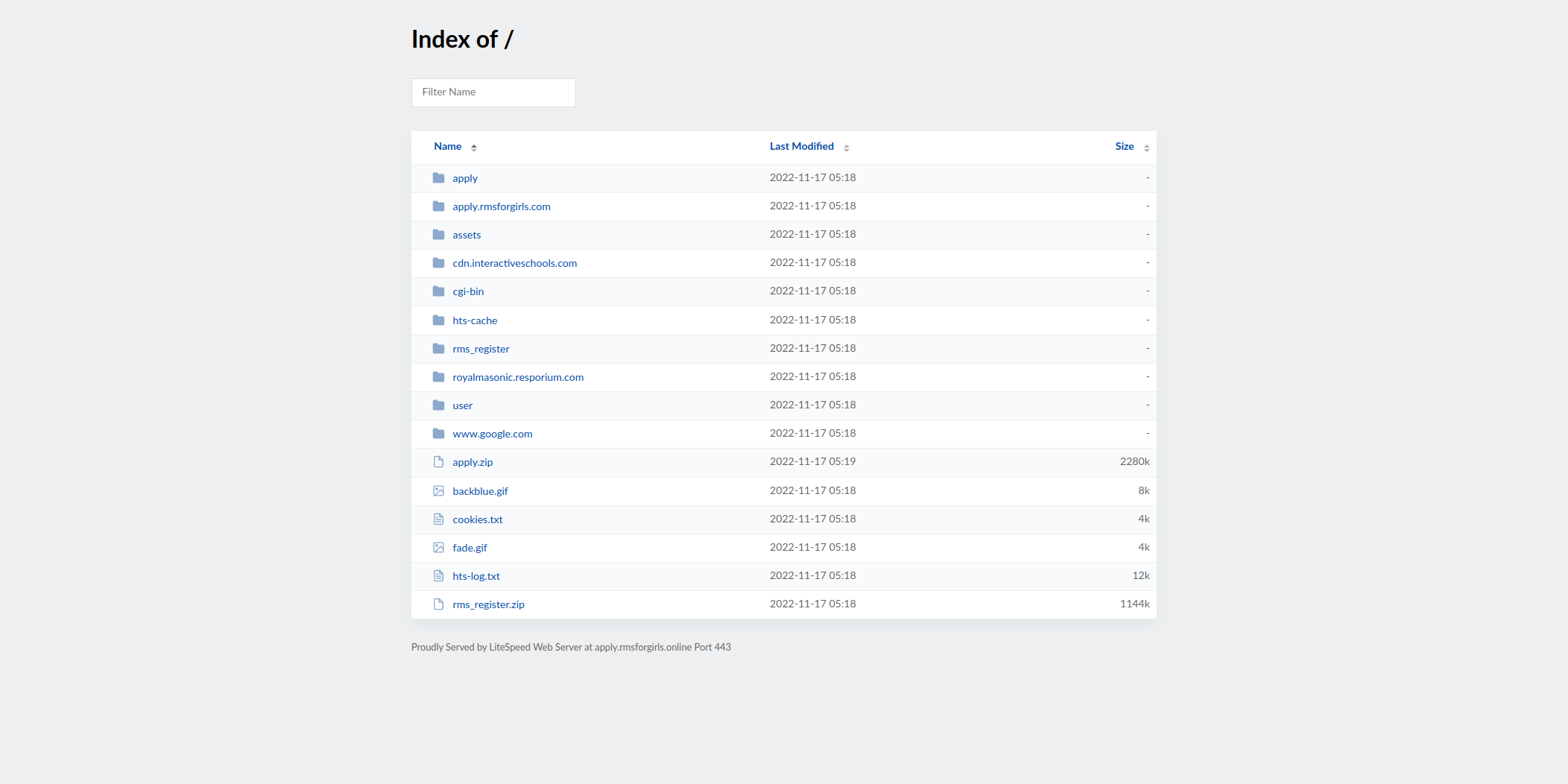 Figure 1: Open Directory on the Phishing Site
Figure 1: Open Directory on the Phishing Site
In a recent phishing campaign, a threat actor targeted The Royal Masonic School for Girls (RMS), an independent school in Rickmansworth, Hertfordshire, England, with day and boarding students. The phishing website domain was created on November 17th at 4:22am and weaponized the same day at 5:18am.
The phishing website housed two phishing kits, one of which was compressed inside the second kit, and both had been extracted onto the domain. The phishing kits contained forensic attributes including date and time stamps, the threat actor’s email address, and computer names from the threat actor’s machine, which allowed us to discover more about the creation of the kit.
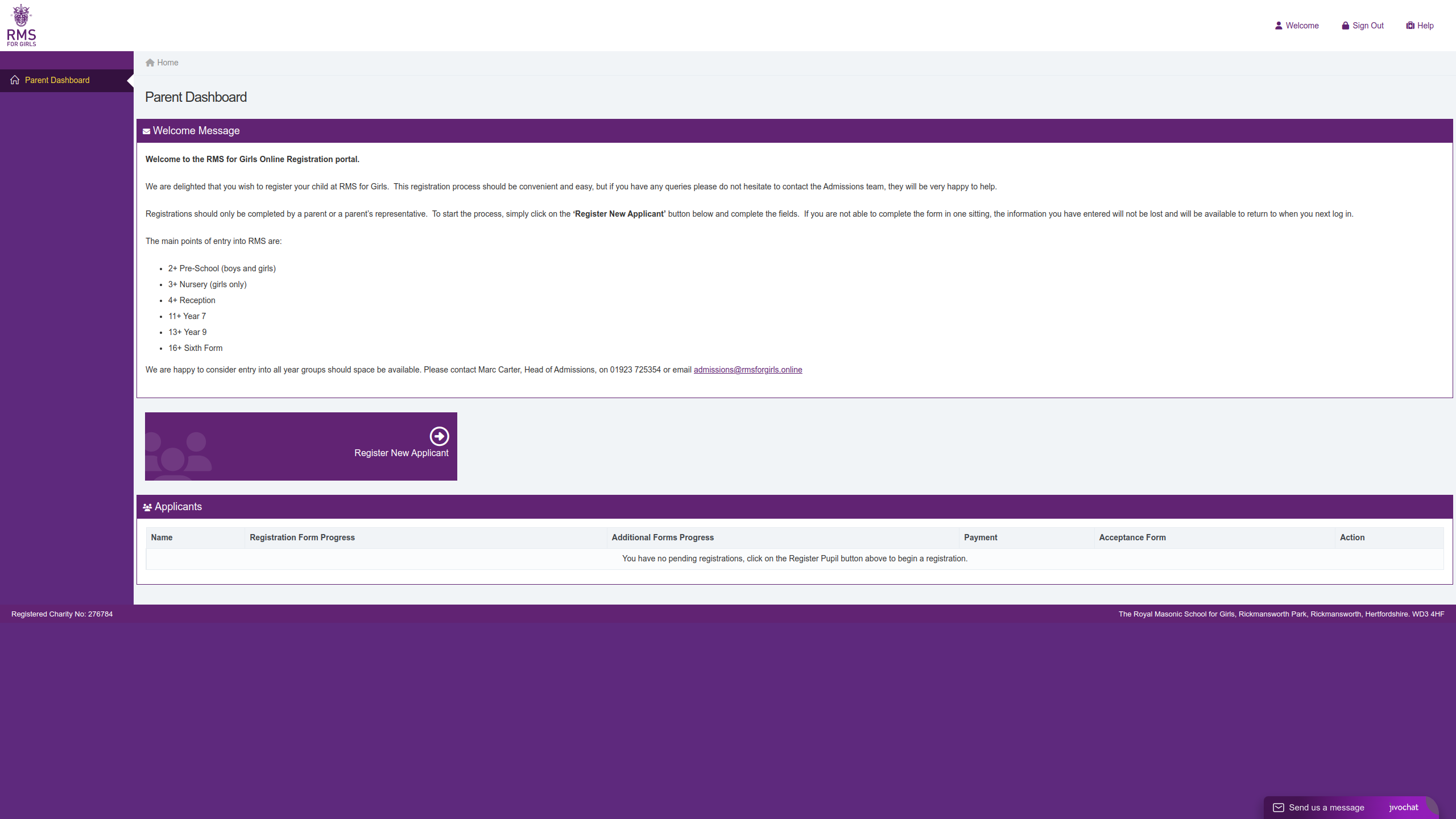 Figure 2: Parents' Dashboard on the Phishing Site
Figure 2: Parents' Dashboard on the Phishing Site
The original school's website was scraped by HTTrack on Saturday, October 22 at 07:36:41. Using this metric, we know that the actor spent twenty-two days between website scraping, weaponization, and campaign deployment. It is especially intriguing to be able to track how quickly a domain is purchased and set up using a ready-to-deploy phishing kit. The threat actor left the HTTrack timestamps in the phishing kit, allowing us to determine when the application form was originally scraped and due to the open directory, we can see when the files were uploaded. The speed of this threat actor also highlights the need for rapid detection of phishing kit creation and deployment.
 Figure 3: Application Form PII Headings
Figure 3: Application Form PII Headings
The RMS application portal is secured behind a login with open registration so anyone can sign up to gain access to the form. Thus, the threat actor needed to create an account before they could scrape the application form. This resulted in some of the user's details being ingested in the scraping. From this, we know the threat actor used the name “Mrs. Enoch” and the email address “atuohainitiatives@gmail.com.”
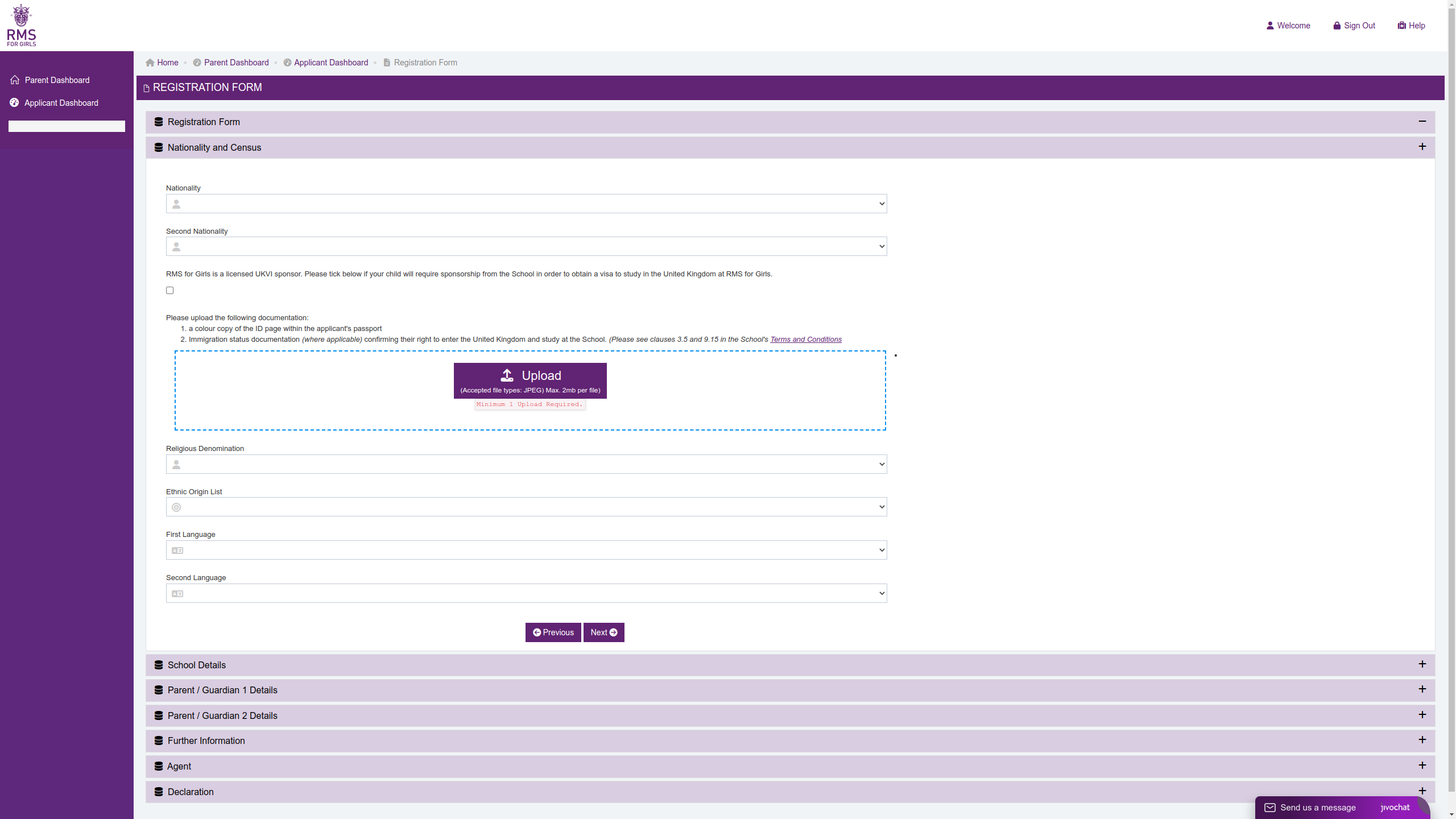 Figure 4: Passport Upload Facility
Figure 4: Passport Upload Facility
Interestingly, the phishing site did not actively exfiltrate stolen personal details when a user input data into the application form. This appears to be an oversight by the actor as the form JSON was built as data was entered and the original AJAX POST request was still present in the kit, but the PHP page was not included. However, it would be simple for the threat actor to add this exfiltration configuration into the kit and that would be a worrying development as the application form collected a significant amount of personal identifiable information (PII) which could have been harvested by the threat actor. The details requested included the child's identification documents and school reports as well as specifics about the parents.
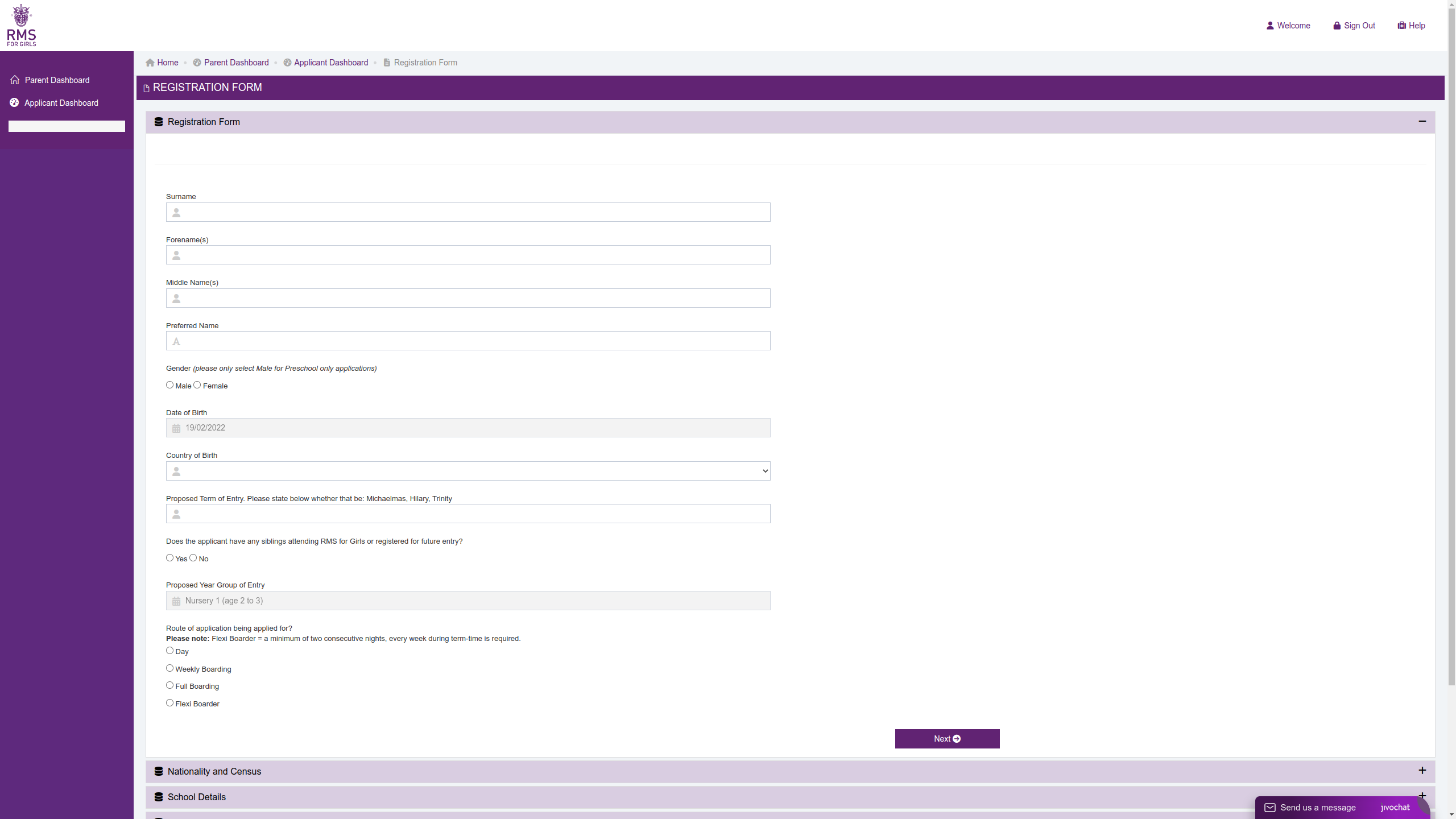 Figure 5: Parent / Guardian Details
Figure 5: Parent / Guardian Details
Once the user completed the application form, the website then requested the victim to pay a £500 submission fee. The phishing site offered Lloyds of London bank details including the necessary IBAN number, which suggests this phishing site was expecting foreigners to be applying to this school. Additionally, the site also offered the ability to pay using bitcoin and had a wallet address listed.
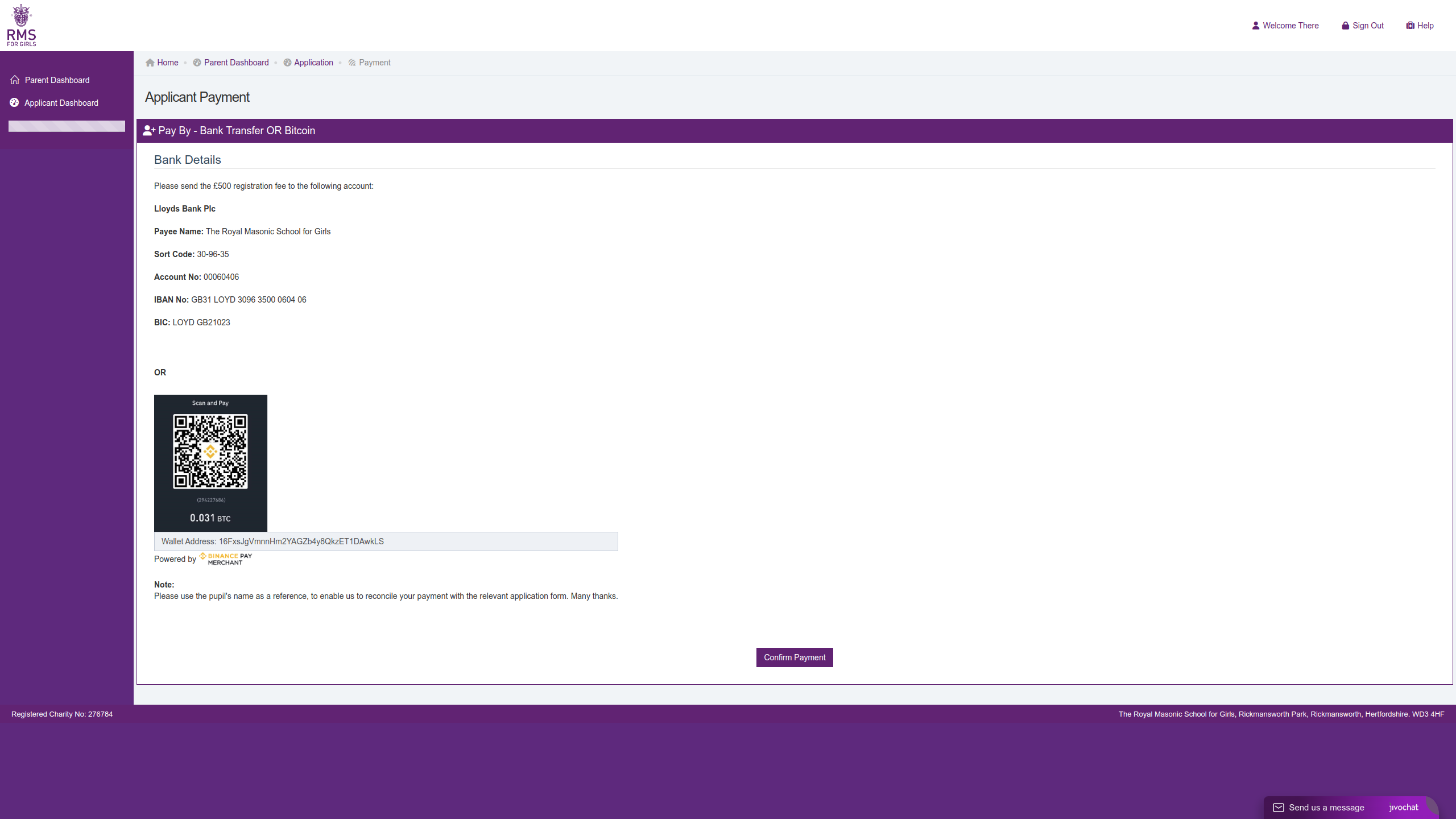 Figure 6: Application Payment Page
Figure 6: Application Payment Page
The threat actor’s main objective of releasing this campaign was likely to capture the £500 application deposit payment as this figure is £400 more than the current RMS cost. We suspect there may be a follow-up scam where the controlling actor could continue to impersonate RMS and request additional money or a down payment for a semester fee if the child was “selected to attend.” This is reminiscent of banking scams where small payments are requested and then a more complex and higher hitting scam will start. Threat actors will spend more time on victims who have fallen for one scam as they are more likely to fall for another scam or lose additional money to the original scam.
WMC Global took additional steps to protect potential victims of this scam. First, the linked bank account was raised directly to Lloyds for them to conduct an internal fraud investigation on the account. We were also successful in getting the website suspended by the hosting provider meaning the site is not resolving any longer.
IoCs
Phishing URL
https[:]//apply.rmsforgirls[.]online
Bitcoin wallet address
16FxsJgVmnnHm2YAGZb4y8QkzET1DAwkLS
dd1dbfd0-1012-4c0a-a4f3-ebd980c7f4fa
b4496ff8-b728-4ae9-b8c1-881d15953f74
