Using a variety of tools and techniques, WMC Global actively tracks threat actors engaged in credential phishing attacks—from canary detection to phishing site launch to the selling of compromised credentials, WMC Global monitors phishing activities the world over.
For complete background information, please first read Deep Dive Into Cazanova Morphine Phishing Kit
In 2018, a new threat actor dubbed “Cazanova” hit WMC Global’s radar, as we were made aware via a secure and sensitive source about the threat actor’s malicious activities. Cazanova created several phishing as a service (PaaS) kits, which were sold to other threat actors on Cazanova’s own website. The number of lures has since increased to include PayPal, Office, Netflix, American Express, and Apple (Figure 1).
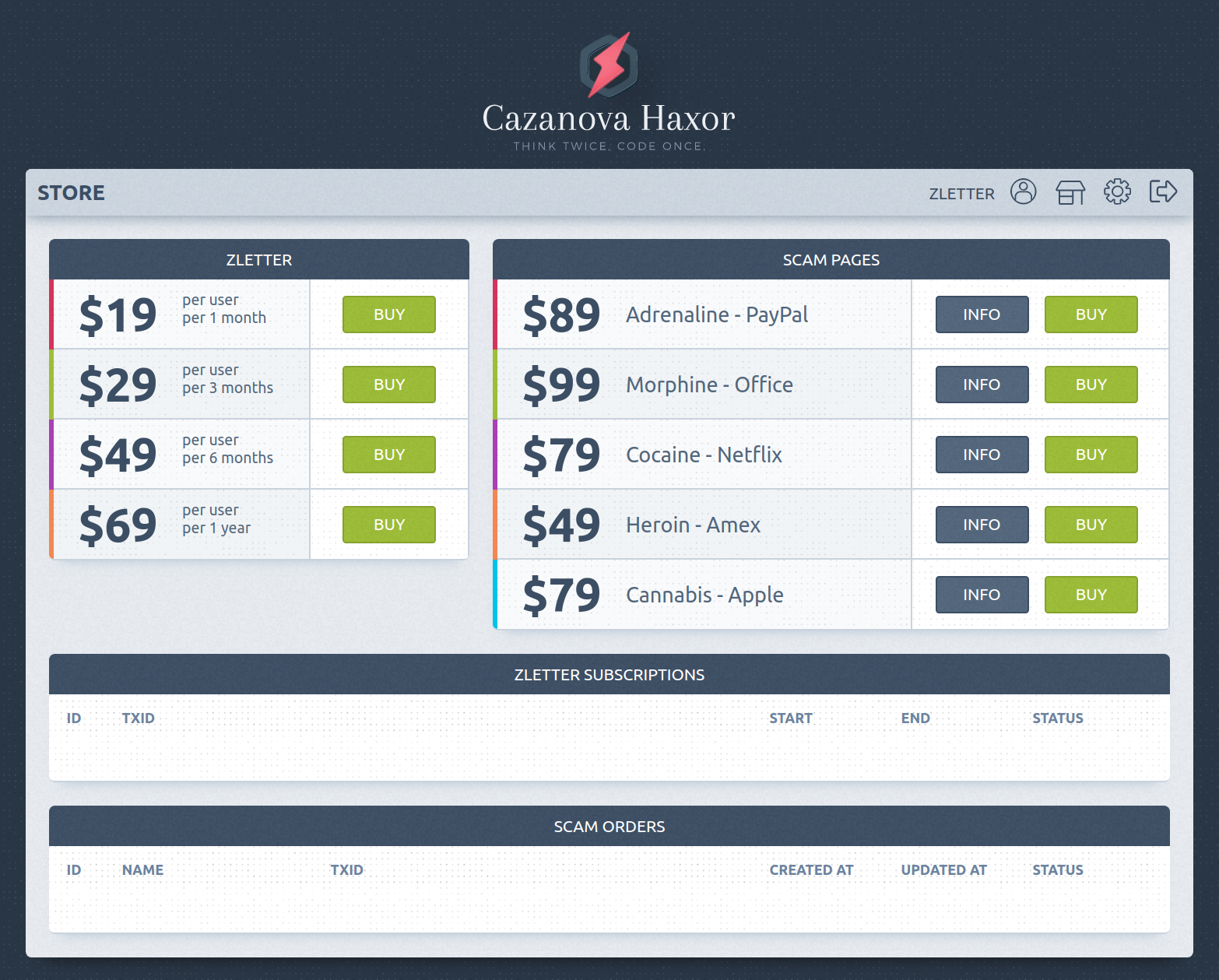 Figure 1: Cazanova's Store Front
Figure 1: Cazanova's Store Front
DETECTION AND INVESTIGATION
The source code used by Cazanova for the Office phishing attack known as “Morphine” was acquired, and WMC Global successfully reverse engineered the phishing kit, enabling a build out of detection rules and line-by-line examination of the code. More information on this analysis is available on WMC Global’s blog Deep Dive Into Cazanova Morphine Phishing Kit.
Cazanova’s true identity was made public on Twitter in December 2019. Cazanova claimed that an unknown threat actor—referred to as “Pheonix Coder”—bypassed the controls on Cazanova's phishing kits and was selling their own versions of the kit. Around the same time, Cazanova also claimed to have stopped creation of malicious phishing pages in a series of revealing Tweets (Figure 2). Despite Cazanova’s claim to be “on the good side,” WMC Global continued its monitoring for signs of malicious activity. In July 2020, WMC Global detected continued activity using Cazanova’s phishing kits.
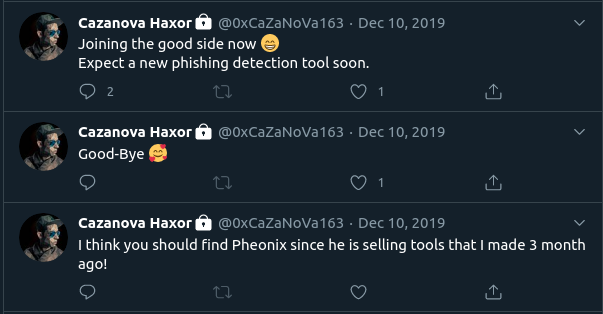 Figure 2: Cazanova's Tweets from December 2019
Figure 2: Cazanova's Tweets from December 2019
Within all Cazanova’s kits exist a distinctive admin panel, which the threat actor who purchases a Cazanova phishing kit can use to view harvested victim details, such as login credentials or other personally identifiable information. A panel from the Morphine phishing kit is shown below (Figure 3).
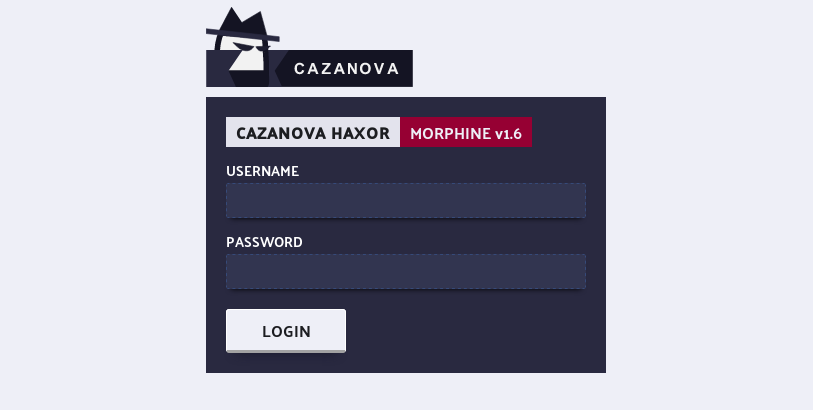 Figure 3: Morphine Phishing Kit Admin Login Panel
Figure 3: Morphine Phishing Kit Admin Login Panel
Attribution
As previously indicated, WMC Global came into receipt of the source code for the Morphine phishing kit—notably, the kit was delivered by the threat actor himself—Cazanova. While examining the kit, WMC Global investigated the phishing kit's validation process. The team extracted all images from the kit, which included an embedded SVG image file within an HTML file. In it, the listed threat actor’s name was not Cazanova but in fact “Pheonix Coder”—the same threat actor Cazanova called out in his December 2019 Tweets (Figure 2 above).
Figure 4 below displays the image differences between an old Cazanova SVG and the newer Pheonix Coder SVG detected by WMC Global in the source code sent by Cazanova. The branding differences between the two phishing kits was unexpected, as WMC Global expected to view the Cazanova-branded phishing kit, given that the kit was received directly from Cazanova himself. WMC Global believes with high confidence it unlikely that Cazanova would have the Pheonix Coder logo on his machine, given his previous assertion that Pheonix Coder had stolen his code. The updates to Cazanova’s Morphine logo represent a potential link between Cazanova and Pheonix Coder.
 Figure 4: Comparison of Cazanova (left) and Phoenix Coder (right)
Figure 4: Comparison of Cazanova (left) and Phoenix Coder (right)
In digging into the asset's directory from the Morphine source code, WMC Global additionally found two images used for the admin panel logo—one using the name Cazanova and another using the name Pheonix Coder (Figure 5).
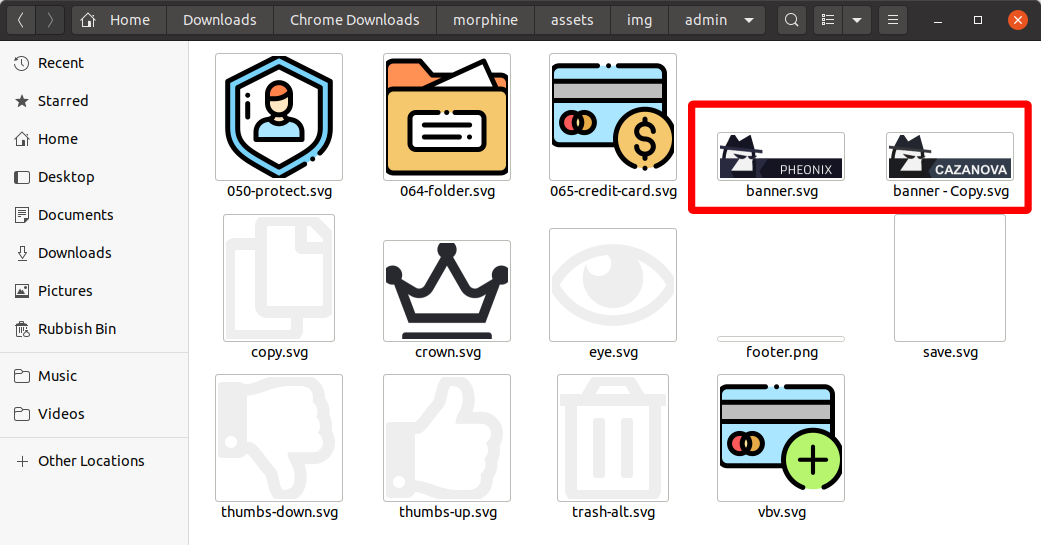 Figure 5: Both Threat Actor Names Found within Assets Directory
Figure 5: Both Threat Actor Names Found within Assets Directory
Further supporting evidence was presented to WMC Global, which asserted that, during the time Pheonix Coder started to release the “stolen” phishing kits, un-activated Morphine phishing kits that previously displayed the Cazanova SVG logo were replaced by the Pheonix Coder SVG logo before being activated.
Additional circumstantial evidence leads WMC Global to assert that the Cazanova and Pheonix Coder threat actors are in fact one and the same. Cazanova’s website is still operating and selling phishing kits, and the back-end version control and update system is still running and operating from Cazanova’s website. WMC Global is unable to find any selling accounts for Pheonix Coder and to date has identified the phishing kits for sale by Cazanova only on his own domain.
Conclusion
WMC Global asserts with confidence there is only one threat actor behind the Morphine phishing kit, and this threat actor answers to both Cazanova and “Pheonix Coder” aliases. WMC Global believes Cazanova attempted to distance himself from malicious activities of his own making after their identity was posted online by using the alias Pheonix Coder as a form of "enemy," allowing them to continue to engage in malicious online activities. In leaking the wrong logo and both banners in the shared kit—not to mention sharing the source code of the phishing kit—Cazanova leaked his connection to his alter ego, Pheonix Coder.
