Phishers are well known for identifying and exploiting security weaknesses. Many email and security teams are becoming more effective at blocking attacks, but phishers are targeting new gaps in remote workforce and SMS phishing detection. Specifically, threat actors are increasing the delivery of phishing campaigns via text message to avoid email vendor protections to deliver phishing directly to victims.
THE SCAM
WMC Global’s Threat Intelligence Team has identified a massive ongoing SMS phishing attack beginning 02.16.21 with 70,000+ unique URLs.. The attackers have converted a popular UPS email phishing lure to text message. We have observed in this attack that the URLs consistently vary per user.

Source: Networks Unlimited
Much like the previous email version of the attack, the text message informs the user that they have missed a package delivery and provides a link to receive more information. Once the user has clicked the link, the phishing website shows the victim what appears to be a UPS tracking number and updates. The site directs the user to enter their credit card payment information to schedule a new delivery. While the attack is impersonating UPS, its objective is to collect personal credit card numbers and accounts for VISA, Mastercard, American Express, and Discover.
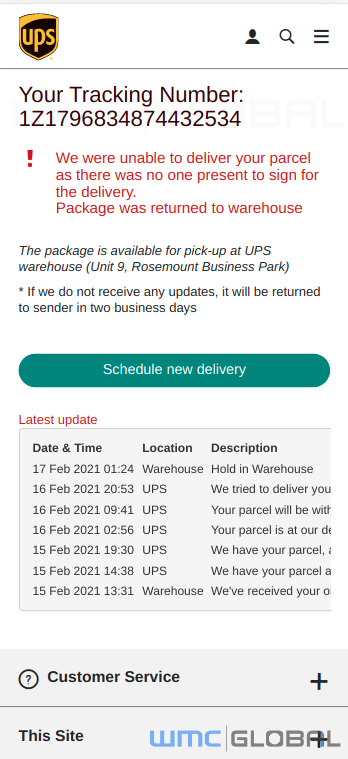
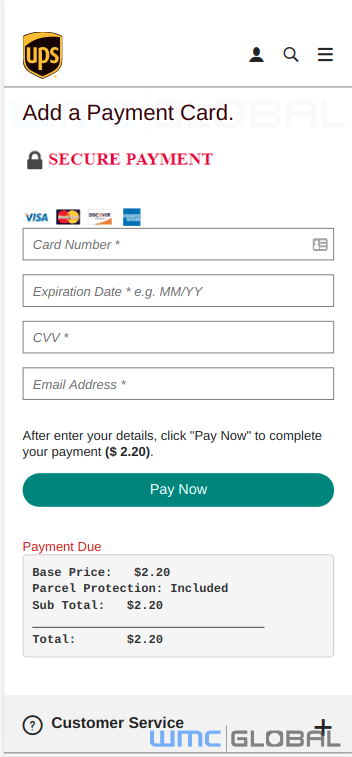
Fake UPS Tracking Number Page Fake UPS Payment Page
WHY IT MATTERS
Threat actors are incredibly adept at adapting to, and taking advantage of, changing conditions in the global marketplace. The pandemic has given them a golden opportunity to monetize e-commerce— a market segment that has grown exponentially. A rapid increase in online shopping means additional shipments made to people who are not used to buying everything online and are unfamiliar with basic personal protection measures when it comes to validating branded SMS messages.
However, the challenge begins before a text message ever makes it to a consumer. Phishing detection vendors have struggled to identify and block UPS branded phishing because of the the letters "ups" having legitimate uses in many contexts. While detection can use image processing, it is more resource intensive and less popular of a feature. This is part of why this particular threat remains effective.
ATTACK DETAILS
Threat actors frequently utilize automated deployment scripts to speed up the building of campaigns allowing them to create hundreds of URLs every hour. As a result of this, we can see automation patterns in the data and draw the following correlations.
TLS Certificate: All the observed URLs are utilizing a TLS certificate which has an issuer of DST Root CA X3. This means that the websites are using HTTPS, ensuring an encrypted connection between the host and the website. Many sites where there is not a TLS certificate are flagged by the user's browser to alert and protect them. As a result, it is now commonplace for phishing websites to install a TLS certificate on their websites to prevent arousing suspicion that the website is fake.
URL Construction: The URLs are all different in their structure; however, they all feature UPS. The URLs also contain a randomly generated number. These are usually used by threat actors to enable them to create hundreds of fake websites simply by changing a digit. If a website is taken down the threat actor has another site already installed just one number different.
Sample Domains:
- link42-ups[.]info
- link12-ups[.]info
- link-2ups[.]com
- conf220-ups[.]com
- link42-www-ups[.]info
- link-3www-ups[.]com
- 56ups[.]info
- 9-ups[.]com
- conf220-http-ups[.]com
- 3881-ups[.]com
- http-ups-link21[.]com
Sample URLS:
- hxxps://link12-ups[.]info/?=638527796
- hxxps://link2-http-ups[.]info/?=801560397
- hxxps://news1-http-ups[.]com/?=780956926
Geo-Filtering: When a user attempts to access the website, the code in the background will check for the accessing user's location. We found that this campaign's users had to be located in the US in order to access the phishing site. If the user was not located in the target area, then they would be redirect into a common scam network. At this time, we are unable to assert whether the scam network has any links or ties to the threat actors conducting the credential phishing.
Mobile Users: The phishing sites also ensured that a user was accessing the website using a mobile device by checking the user agent. If a user clicked the link on a desktop computer, then the same redirect chain would occur sending the user to a random scam network chain. The phishing site could only be accessed if a user was based in the US and accessing the phishing site from a mobile device.
In many cases with SMS phishing, each link tracks an individual phone number. The attacker records if the user clicks the link and if they fall for the phish. This helps identify the most vulnerable targets for future attacks as well as improve evasion. For example, the fact that the phish will block non-mobile users from connecting helps the attack stay active longer and avoid detection.
HOW TO PROTECT YOURSELF
What should you do if you receive a suspicious text message?
-
Do NOT engage. If you are, in fact, expecting a package, go to the legitimate service website to call or check your order online.
-
If you believe you have received a spam or a phishing text message you can report the message via SpamResponse.com or forward the message to your mobile carrier to 7726 for further investigation.





